Wondering how DNS really works? Watch it in action with this free app
This freebie shows DNS at work and gives you some real benefits

Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Use the web for more than five minutes and you're sure to hear about DNS, the Domain Name System.
Indeed, you may already know that it's a vital internet technology that translates domains such as techradar.com, into IP addresses like 192.232.198.114. But unless you're a networking geek, that might sound too complicated and theoretical to be really useful.
DNSQuerySniffer proves it doesn't have to be that way. It's a free Windows tool which absolutely anyone can use to watch DNS in action to see how it really works. And there are very real practical benefits, too: you can spot apps accessing the internet without your knowledge, maybe detect malware, and even help confirm your VPN is working correctly.
DNSQuerySniffer
Getting started with DNSQuerySniffer begins by downloading the version you need from developer NirSoft's site. There are 32 and 64-bit flavours; the 64-bit should cover all but the oldest Windows systems, so choose that option if you're unsure.
Clicking the link gets you a tiny zip file (136KB), and you can extract the contents in the usual way (right-click the file in Explorer, select Extract all... and accept the default folder).
And that's it, you're done. There's no downloader to fetch 500MB of other files, no installation required, no network drivers to conflict with anything else. Just switch to the folder you just created, run DNSQuerySniffer as an administrator (right-click, choose Run As Administrator) and you're ready to go.
Launch DNSQuerySniffer for the first time and it asks which network adapter you'd like to monitor. There might be several options in the list, especially if you've installed a few free VPNs on this system. But normally all you have to do is choose the adapter with the connection name Ethernet if you have a wired connection, or WiFi for wireless.
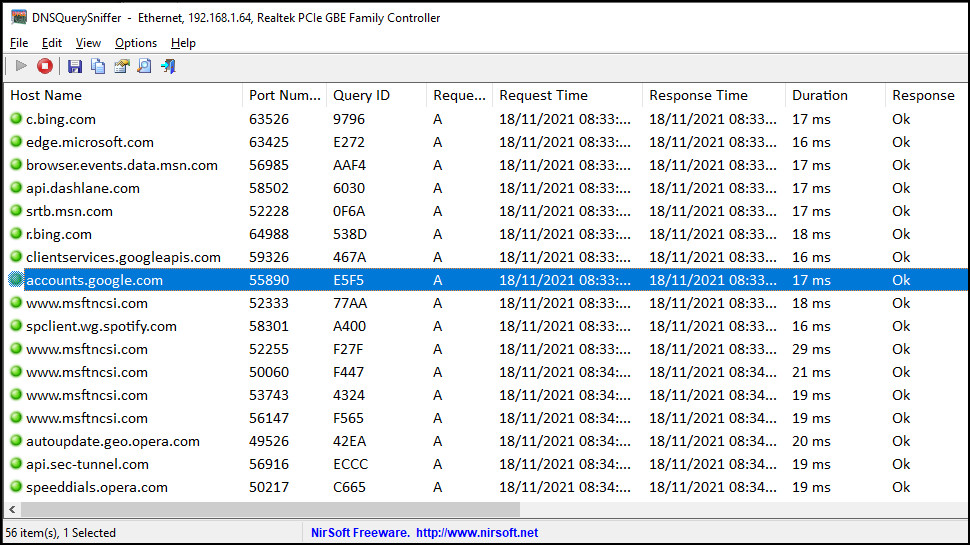
DNS in action
To get a look at how DNS works on the web, just point your browser at a popular ad-packed website which you haven't visited so far today (because your system might have stored previous DNS query results, and you won't see them this time). Newspaper websites are often a good choice:.
DNSQuerySniffer can show a huge number of queries - 20, 30, 40, more - from a single page, because big websites often contact so many other many domains. Some might store their own content - images, videos, comments, scripts - but they can also link to ad servers, trackers, all kinds of other third-party sites.
That works as a quick and easy demonstration of why some sites are really, really slow: they must access content from a long list of other domains before they can finish loading.
But it can also be interesting if you look at exactly which domains they're accessing. Are there any you recognize, are some sites querying a high number of ad, tracker or social media domains? Maybe others look really clean by comparison: they're loading their own HTML, images and scripts from their own servers, but not trying to share your details with the rest of the world. Try a few of your favorite websites, see how they compare.
(Note that DNSQuerySniffer keeps adding new queries to the end of the table, which can make for a very long list in a very short time. Click File > Clear All Current Items if you'd like to empty the table and start again.)
What's using your internet connection?
DNS queries aren't just used for browsers. They're made whenever an app accesses a website. That means you can also use DNSQuerySniffer to show you which of your apps are making background web requests, and the domains they're trying to reach.
You don't have to do any extra work to make this happen. Just close any other open apps, leave DNSQuerySniffer running, and look at the HostName and CNAME columns for any new queries which pop up.
Most PCs always have a lot of background internet activity going on. We saw queries from our password manager (Dashlane), backup app (Backblaze), chat tools (Slack) and Windows VPN, for instance, as well as queries to Windows Update and Office URLs (Outlook and others.) There's no harm in any of that: many apps will regularly be checking servers, syncing data and generally getting on with their regular tasks.
But you might see more surprising traffic, too. Maybe an app you've installed is regularly going online, when you'd rather it didn't? Perhaps there's a 'check for updates' switch you can turn off. Could be other apps are trying to access ad servers, Google Analytics, any odd domains which indicate they're doing something you didn't expect.
You could even spot a malware infection, if there's a lot of unusual traffic, though run the domains through a Google or two before you panic. We spotted plenty of cryptic domain names which turned out to be entirely legitimate.
A quick VPN test
Just watching normal DNS activity can tell you a lot about your system, but stick with DNSQuerySniffer and there's plenty more to discover.
We'll cover just one trick here. If you use a VPN then you'll probably know it's supposed to redirect all your internet traffic, including DNS queries, through a secure encrypted tunnel.
In some cases you can see this in action just by watching DNSQuerySniffer in action. Run the program as normal, browse to a few sites, confirm it's displaying DNS queries. Then connect to your VPN, visit more sites, and if DNSQuerySniffer doesn't display any DNS requests, that shows the queries are being redirected as we'd expect.
This isn't a conclusive test and doesn't absolutely prove that your VPN is handling DNS queries correctly (or not). But it gives you an indication, and is quick and easy to run. We tried the test with both ExpressVPN's and NordVPN's apps, and in each case DNSQuerySniffer didn't detect or display any DNS queries while the VPN was connected: an ideal result and exactly what we'd expect from two of the world's best VPNs.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.