How do social media in-app browsers affect your online privacy?
Meta and TikTok seem to use these to better track users
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
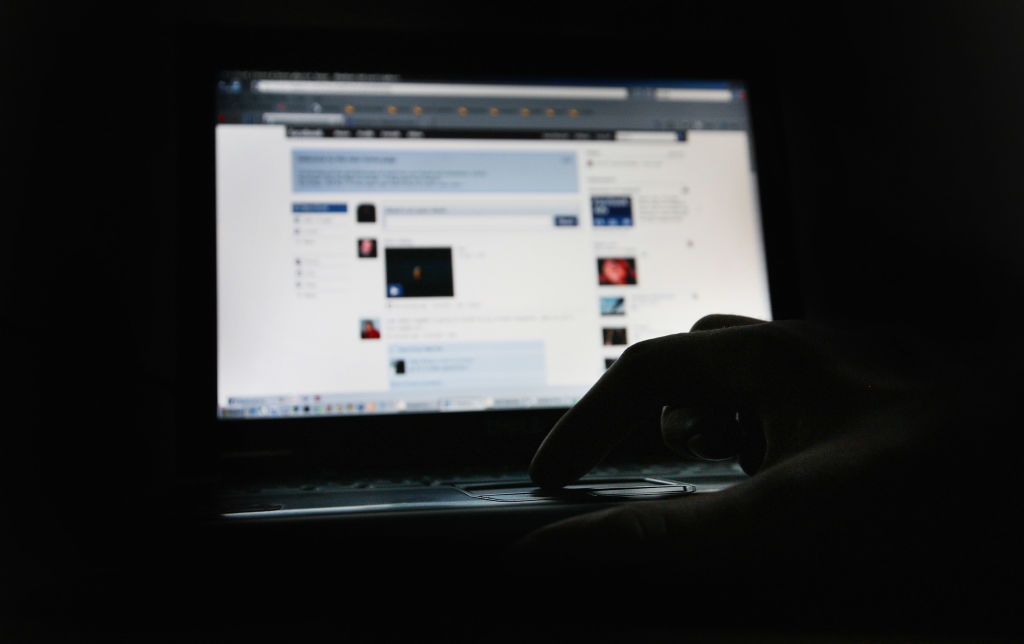
As a new research on social media in-app browsers shows, there are some hidden web trackers that not even the best VPN services can prevent.
Felix Krause, a former Google engineer, reported that people who directly open webpages from their Facebook and Instagram app could be putting their personal information at risk. This is because Meta seems to inject additional lines of code on websites to better track users' online activities.
In another report published a few days later, Krause explained that also the popular video-led platform TikTok uses the same type of JavaScript injections for similar purposes.
Meta and TikTok inject codes to track users
"I don’t have a list of precise data Instagram sends back home. I do have proof that the Instagram and Facebook app actively run JavaScript commands to inject an additional Javascript SDK without the user’s consent, as well as tracking the user’s text selections," wrote Krause.
He explains that such apps inject their JavaScript code into every website shown, even on ads.
"Even though the injected script doesn’t currently do this, running custom scripts on third party websites allows them to monitor all user interactions, like every button and link tapped, text selections, screenshots, as well as any form inputs, like passwords, addresses and credit card numbers," he said.
Also, the TikTok iOS app has been found capable of "subscribing" to all keyboard inputs. This means that it can potentially monitor everything you click on your screen while using the app.
💥 New Post: Instagram & Facebook tracks everything you do on any website in their in-app browserhttps://t.co/dj5CMJUwHc pic.twitter.com/LvWXGa34N2August 10, 2022
Both Meta and TikTok quickly replied to such allegations.
Despite not revealing the practice to its users in advance, Meta said that the script injected helps Meta respect the user’s ATT [App Tracking Transparency] opt out choice.
“The code allows us to aggregate user data before using it for targeted advertising or measurement purposes. We do not add any pixels. Code is injected so that we can aggregate conversion events from pixels,” a Meta spokesperson explained to The Guardian.
TikTok also confirmed the existence of such features, Forbes reported. However, they claim not to use JavaScript injection for aggressively tracking users.
"Like other platforms, we use an in-app browser to provide an optimal user experience, but the JavaScript code in question is used only for debugging, troubleshooting and performance monitoring of that experience — like checking how quickly a page loads or whether it crashes," spokesperson Maureen Shanahan told Forbes.
What is Javascript injection?
Javascript injection defines the practice of adding an extra line of code to a webpage before opening it to a user.
As it has the potential to allow the manipulation of websites or other web applications, it is generally used by hackers or other malicious actors to send cyberattacks. Similarly to malware injection, these attacks aim to collect users' sensitive data.
As Krause explains in his blog posts, this practice allows both Meta and TikTok to track users' activities after they leave the social media app: from the page they visit, to what they type on the devices' keyboard and screenshot they take.
Even though the companies behind these popular social media platforms assured they don't use Javascript injection for malicious intents, its potential dangers cannot be verified just yet.
What's certain is that Meta, for example, experienced a record drop in daily users and a 26% fall in the company share price this year. The latter came after Apple introduced a stricter policy against cross-host tracking. This means that app developers now need to ask permission to track users across apps.
Krause also pointed out that Safari, Google Chrome and Firefox have all been revamping their third party cookies policies lately.
How to protect yourself against in-app browsers tracking
Whether or not social media developers use in-app browser links to enhance their control on users, there are a few ways to simply avoid the practice.
1. Open the URL directly on the browser
A quick way to be sure of escaping JavaScript injection via in-app browser links is not clicking on these. You can either select the option of "Open the tab on your browser" or copy and paste the URL to open it on the browser of your choice.
2. Use the web version of the social media app
As social networks also have a web-version of their apps, you could consider using this instead of the mobile application to escape any danger of in-app browser pages.
3. Verify which type of information your apps retain about you
There is also a way to know exactly which JavaScript commands your apps have sent. Only available for iOS users right now, share the InAppBrowser.com link somewhere inside the app (you can send it to a friend as a DM, for example.) Once you've done this, tap on the link you send to open it. A detailed report listing the JavaScript injections executed will then appear for you to review.

If you are worried about your general online privacy, you can also use additional security software to protect your sensitive information.
You can replace your data-hungry Google Chrome with one of the most secure browsers, for example. You should also consider securing your overall online anonymity with a secure VPN service.
One the best cheap VPN services around, Surfshark, even offers a full security bundle including four cybersecurity tools with just one subscription. Surfshark One comes with its own VPN, a data leak detection system, a private search engine and antivirus software.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!

Chiara is a multimedia journalist committed to covering stories to help promote the rights and denounce the abuses of the digital side of life – wherever cybersecurity, markets, and politics tangle up. She believes an open, uncensored, and private internet is a basic human need and wants to use her knowledge of VPNs to help readers take back control. She writes news, interviews, and analysis on data privacy, online censorship, digital rights, tech policies, and security software, with a special focus on VPNs, for TechRadar and TechRadar Pro. Got a story, tip-off, or something tech-interesting to say? Reach out to chiara.castro@futurenet.com