New DarkIQ features can provide an ‘early-warning’ to cyber attacks
DarkIQ adds new range of features to boost your cybersecurity

Searchlight Cyber has released new features as part of its DarkIQ platform, allowing live dark web traffic monitoring.
This unique capability provides its users with the ability to not only gather dark web data to help with threat investigation, but also anticipate cyber attacks and stop them before sustaining damage.
By anticipating and stopping cyber threats before they launch an attack, there is a significant reduction in both impact and cost.
Tor network monitoring with a twist
DarkIQ provides businesses with the ability to monitor traffic between their own infrastructure and Tor going in both directions.
Traffic traveling from the dark web to the company can provide insights into hackers attempting to gain access to data or trying to install malware. Traffic traveling externally from the company to the dark web can suggest that employees are using the dark web, that hackers have already breached a company network, or if data is being extracted from company systems and uploaded to the dark web.
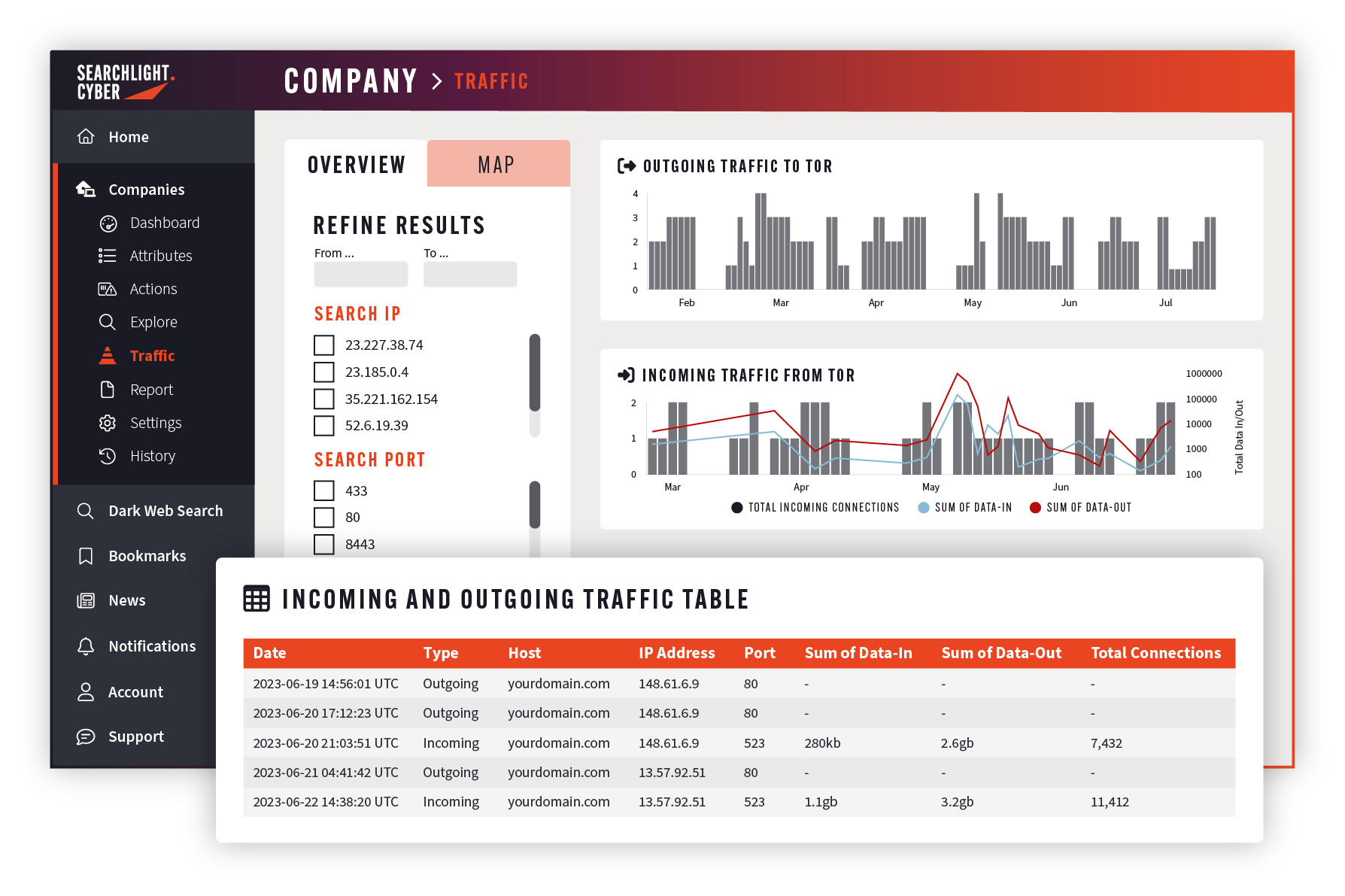
The latest enhancements to the Dark Web Monitoring system include; enhanced granularity allowing your cyber security team to see detailed information on connections to and from the dark web including how much data is being transferred; new visualizations allowing security teams identify threats through data analysis; and traffic splitting which divides incoming and outgoing traffic to allow more efficient threat identification.
“Dark web traffic between Tor and the corporate network is a very reliable datapoint for identifying malicious activity, and we have seen first hand how organizations have used it to identify cyberattacks and take preventative action before any damage was done,” said CTO of Searchlight Cyber, Dr Gareth Owenson.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
“However, this relies on them firstly having visibility into the traffic, and secondly having the data points they need to identify where to start their investigation. The enhancements we have made to our Dark Web Traffic Monitoring feature provide our customers with even more context, to help them assess exactly what malicious activity is taking place, and the best mitigative actions they can take.”
More from TechRadar Pro

Benedict has been with TechRadar Pro for over two years, and has specialized in writing about cybersecurity, threat intelligence, and B2B security solutions. His coverage explores the critical areas of national security, including state-sponsored threat actors, APT groups, critical infrastructure, and social engineering.
Benedict holds an MA (Distinction) in Security, Intelligence, and Diplomacy from the Centre for Security and Intelligence Studies at the University of Buckingham, providing him with a strong academic foundation for his reporting on geopolitics, threat intelligence, and cyber-warfare.
Prior to his postgraduate studies, Benedict earned a BA in Politics with Journalism, providing him with the skills to translate complex political and security issues into comprehensible copy.