TechRadar Verdict
Harmony is music to our ears. The platform is easy to deploy, as there are multiple setup options. The cloud portal is very easy to navigate and well laid out. It also immediately detected threats in our tests.
Pros
- +
Simple setup
- +
Very intuitive interface
- +
Advanced threat detection
Cons
- -
Unclear pricing model
Why you can trust TechRadar
1993 was the year Jurassic Park first appeared on screens, as well as the inauguration of the current European Union. It was also the year that "Check Point Software Technologies Ltd." was founded in Israel.
In the past 30 years the company have released any number of software and hardware products focusing on cyber security. Of all the companies we've reviewed frankly they even rival Microsoft in the number of solutions offered.
The focus of this review is on Check Point's "Harmony Endpoint". The platform is designed for endpoint protection and its creators claim it offers this along with EDP (Endpoint Detection and Reponse) and XDR (Extended Detection and Response) from a single console.
Has the Israeli-American IT Security giant done it again or should Check Point have just stayed home and watched Jurassic Park?
Check Point Harmony Endpoint: Plans and Pricing
Harmony Endpoint is actually part of a range of 'Harmony' products offered by EndPoint. Its main page reveals that there are three main tiers: Basic, Advanced and Complete.
If you want specific pricing information though, you'll need to use CheckPoint's "Partner Locator" to provide specific information about your whereabouts. This was rather puzzling to us given that Check Point offer a free 30 day trial of the platform for up to 100 endpoints. Presumably it would be simpler to offer a payment option via the online console to extend the subscription after the trial ends.
Still, we persevered and entered our location info. This led us to 'Optiv' who supposedly offer Harmony products but on visiting their website no pricing was available. A little online delving revealed CheckPoint's pricing for Amazon Web Services, as well as other third party services. We encourage readers to sign up for the free trial and approach Check Point directly to confirm exact prices, as Amazon prices an annual subscription to Harmony Endpoint Basic as $1,050 for up to 50 seats. This works out at $21 per seat, which would make the platform very expensive compared to competitors.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
This nebulous pricing model is disappointing, particularly as similar EDP platforms usually display subscription fees clearly on their website.
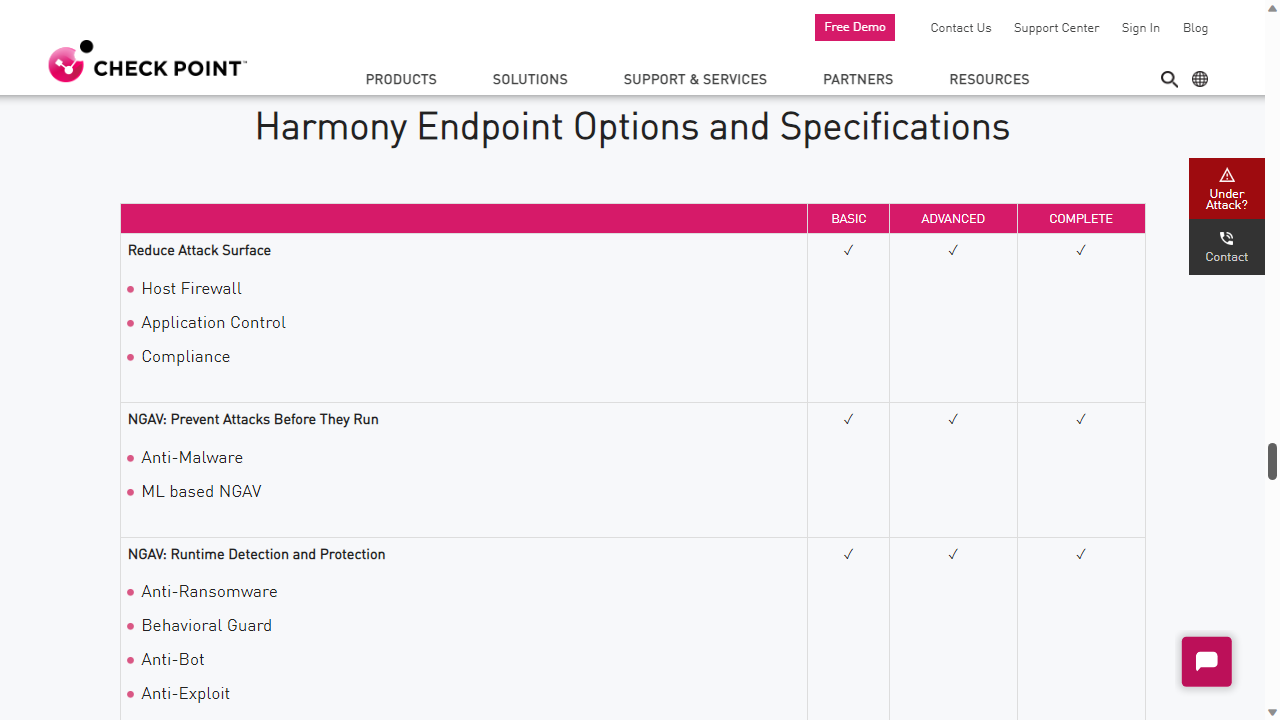
Check Point Harmony Endpoint: Features
Despite a vague subscription model, anyone who avails of the 'Basic' Harmony EndPoint plan will enjoy a range of security features including a host firewall and application control.
Basic subscribers also benefit from antivirus. The platform uses machine learning to detect and prevent threats like ransomware and other types of exploits.
There's also a built-in function to block malicious sites as well as filter URLs specified by managers. We were particularly impressed to see that even the 'Basic' pricing tier includes a remote access VPN.
'Advanced' Subscribers to Harmony Endpoint benefit from all of the above, as well as "Content Disarm & Reconstruction (CDR) across email and web". In practice this seems to consist of a sandbox for testing suspicious files as well as the ability to sanitize files in 1.5 seconds.
Those users who sign up for the 'Complete' package will benefit from all the perks of the 'Basic' and 'Advanced' tiers, as well as host and media encryption. The Harmony Endpoint page also lists 'port protection' as a perk of the 'Complete' tier but goes on to explain this is available for other tiers too.
All subscription tiers include professional support, nine hours a day, five days a week.
Check Point also has an in-depth data sheet listing more of Harmony Endpoint's features.
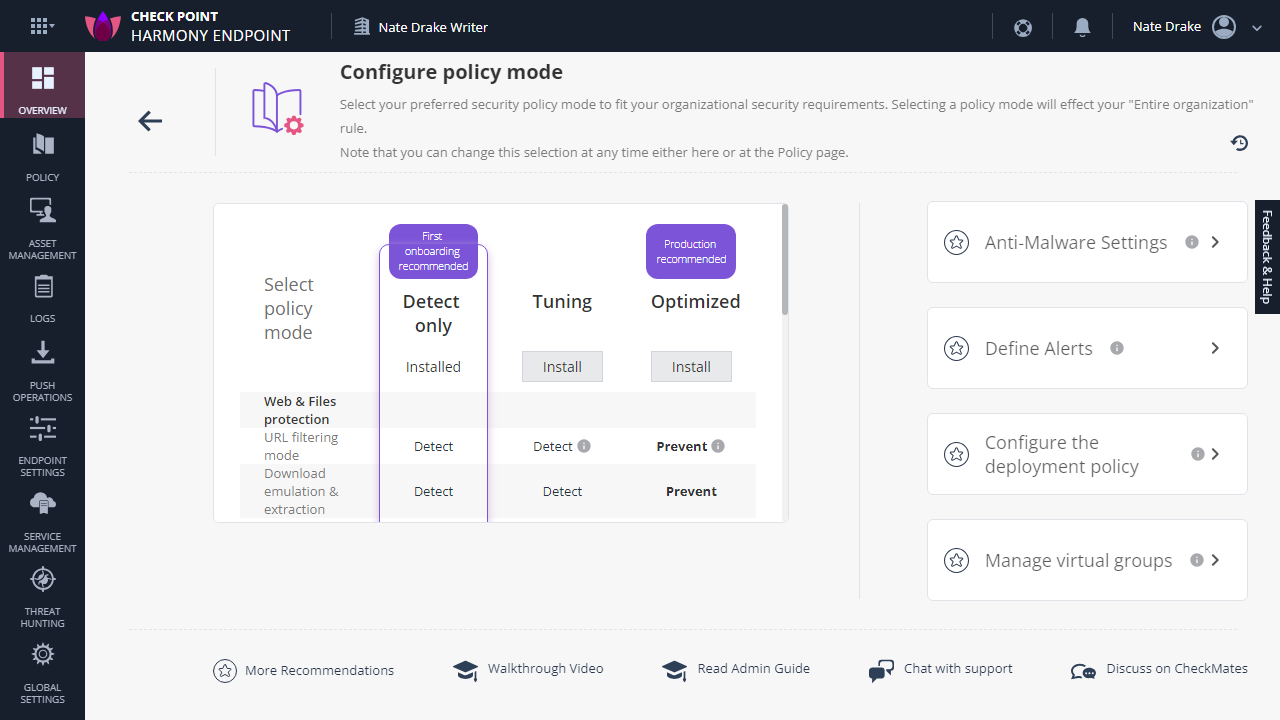
Check Point Harmony Endpoint: Setup
In order to access the free trial Harmony Endpoint interested parties must fill in an online registration form with their company details. No credit card is required.
Once users confirm their email address, you can log in to the 'Infinity Portal', from where you can download trials of any number of Check Point products including Harmony Endpoint.
On selecting the platform we were pleased to see the 'getting started' section which provided helpful links like configuring policy mode and connecting/distributing your first agent.
On choosing to install the agent, we were surprised to see a number of different ways this could be done. If the endpoint's running Windows or Linux you can choose to do an 'online install' as we did, to download a small program which in turn loads the main agent program. There's also a macOS client.
Although Harmony Endpoint itself can't manage Android/iOS devices, you can sign up for Harmony Mobile (formerly Sandblast Mobile) if your organization needs this.
As the endpoint client was downloading and installing, we took a gander at the Harmony Endpoint Portal's policy modes, as per the 'getting started' section. By default this is set to 'detect only', which we presumed to mean the client software would raise alerts for threats but not take action.
This is only recommended while onboarding, but as we were keen to make sure the platform proactively blocked threats, we changed the policy to 'Optimized'. By default any policy changes will apply to all endpoints in your organization.
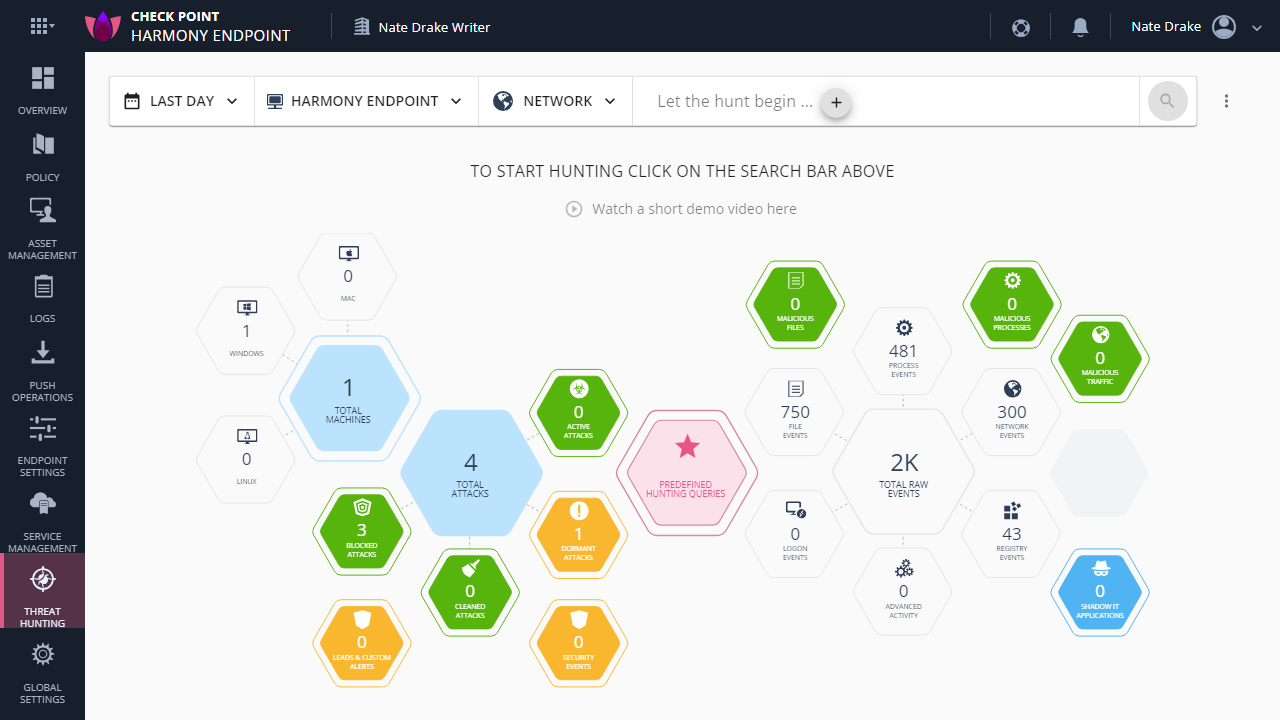
Check Point Harmony Endpoint: Interface
We've already touched on the helpful screen that first displays when logging in to the Harmony Endpoint portal. The left hand pane contains easy to understand icons, which are labeled.
The 'Overview' section is especially well laid out, its "Unified Dashboard" displaying workstations by operating system, as well as details of malicious file attacks and alerts. You can click in to any notification area to see for information, as we did for 'Alerts' to discover that the new endpoint (our test machine) hadn't yet been scanned for malware.
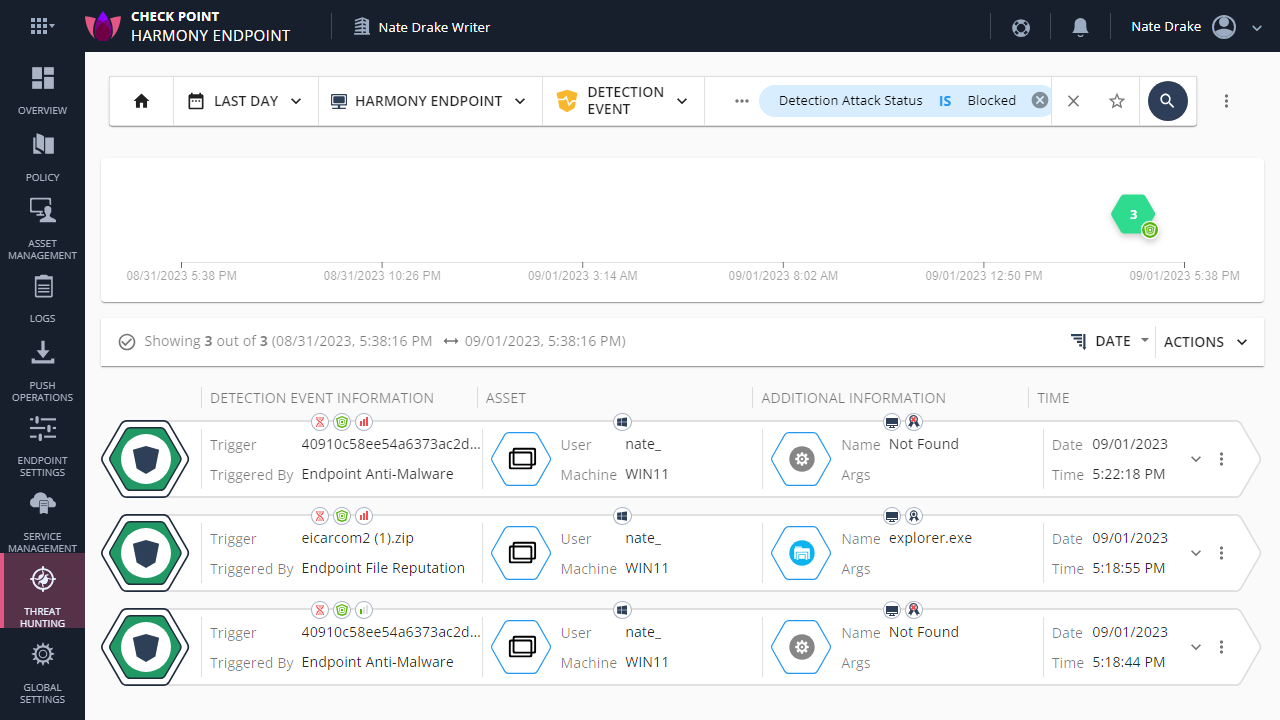
Special mention should definitely go to the 'Threat Hunting' section which makes excellent use of graphics to display a network overview of endpoints in your organizations, as well as the number of attacks. From here you can also apply filters to find specific events either by clicking on a graphic e.g. 'Total Attacks' or by using the search bar at the top of the screen.
Although searching for threats is a commonplace feature of endpoint security platforms, Harmony Endpoint stands out given how simple the 'Threat Hunting' section is to navigate, given its layout and use of color.
Check Point Harmony Endpoint: Performance
When reviewing Endpoint Security platforms our first test is always to try to download a fake computer virus via Microsoft Edge in our test machine running Windows 11.
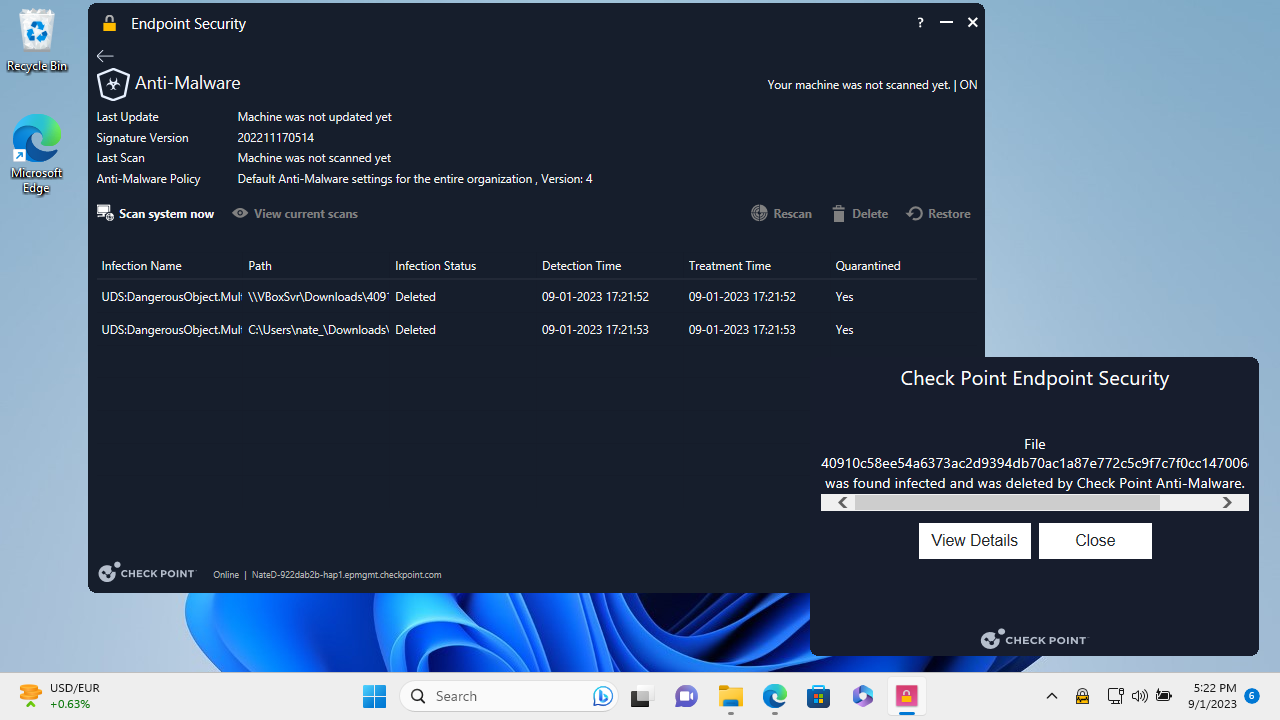
We visited the website hosting the virus (provided by the good people of EICAR), then tried to download the virus in compressed (ZIP) format. The Harmony client software immediately detected and blocked the file from downloading. This is impressive given that not all endpoint security platforms see ZIP files as a threat.
We next tried to copy over a real computer virus that we'd caught in the wild to the 'Downloads' folder to our test machine. Once again, Harmony didn't disappoint by immediately detecting and quarantining the virus.
Our next test was to log in to the Harmony Endpoint cloud portal to check if any alerts or reports had been triggered to alert managers to the threats on the endpoint. Sure enough on first log in to Harmony's "Security Dashboard" we saw each one of our test files along with their exact location and threat rating.
Check Point Harmony Endpoint: Final Verdict
From a technical point of view Harmony Endpoint is faultless. Even its basic tier has everything you'd expect to see in an endpoint security platform, with the possible exception of support for mobile devices which is managed by a separate 'Harmony' product. We were particularly happy to see support for endpoints running the Linux operating system.
There's a free trial of the platform which requires no payment information and in our tests we were able to deploy the endpoint installation software in minutes. Security is iron clad, blocking both suspicious URLs and quarantining potentially dangerous files immediately.
We were extremely impressed by the responsiveness of Harmony's cloud portal, which generated alerts as soon as threats were detected. As mentioned, the "Threat Hunting" section is a pleasure to use, being clearly color coded and easy to navigate.
The only criticism we can level against Harmony Endpoint is the vague pricing model, whereby interested parties must contact one of Check Point's partners to sign up. This is at odds with all the other endpoint security platforms we've reviewed in the past who clearly display pricing tiers on their page.
It's also the reason we've awarded Harmony Endpoint 4 out of 5 stars, as naturally if users are considering this solution for endpoint security they need to know the exact cost to their organization. Provided you are able to obtain a detailed quote however, we strongly recommended this platform for endpoint protection.
We've listed the best MDM solutions.
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.
