Avalanche of money-stealing malware in 2008
Panda Security predicts web threats evolving next year
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Security firm Panda Security has warned how internet threats such as malware will evolve and become more complicated in 2008, creating an 'avalanche' of spam and phishing tools.
The amount of known and unknown malware in circulation is set to increase next year, Panda Security predicted. Platforms not previously targeted by cyber criminals, such as Apple Mac computers and VoIP services are also expected to be hit.
The aim of cyber crime will remain the same as today - to obtain confidential data for online fraud and theft. Trojans will continue to be present, and will also evolve to try to steal information from users of social networking websites such as MySpace and Facebook, and online games.
OS vulnerabilities
Cyber crooks will also continue looking for new vulnerabilities in operating systems and applications that allow them to install malware without the user's knowledge. So-called 'drive-by downloads' -where a user is made to click on a link or open a document containing a page that can detect vulnerabilities on their computer to infect them - will also be an issue.
"Malware attacks have been increasingly sophisticated throughout 2007 in the technological field and there is evidence that new malware is becoming increasingly complex," said Luis Corrons, technical director at PandaLabs.
"This complexity stems from the merging of several types of threats, resulting in the appearance of hybrid malware. It appears that this phenomenon will continue over the next year."
Corrons reminded that it is essential to always download the latest security updates for both your operating system and your web browser when these are released. Also, never click on links in emails claiming to be from a financial institution, auction website or stock broker unless you are absolutely confident about their authenticity.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
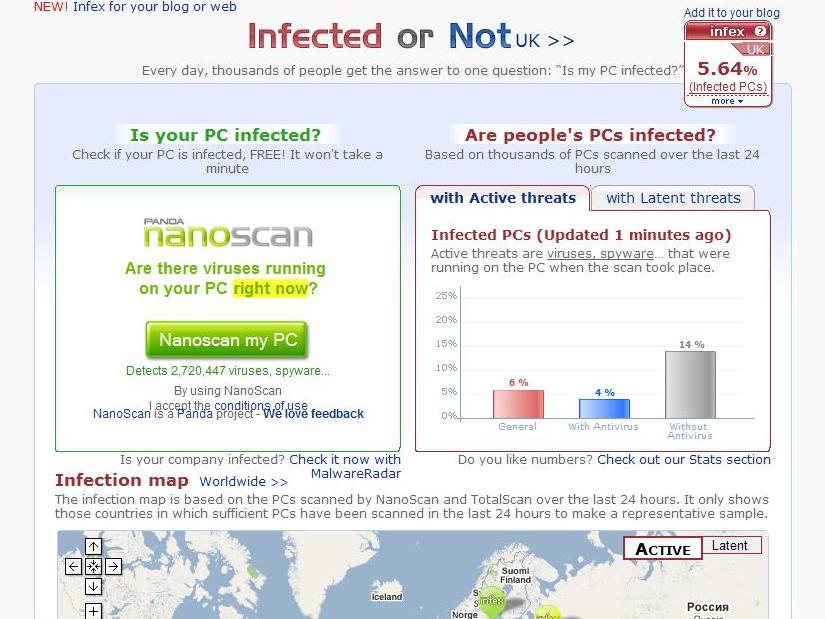
Panda Security offers several free tools for scanning computers at http://www.infectedornot.com.