That's not very trendy of them - AI browsers can be hacked with a simple hashtag, experts warn
Some browsers are more exposed than others
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
- Hidden URL fragments allow attackers to manipulate AI assistants without user knowledge
- Some AI assistants transmit sensitive data to external endpoints automatically
- Misleading guidance and fake links can appear on otherwise normal websites
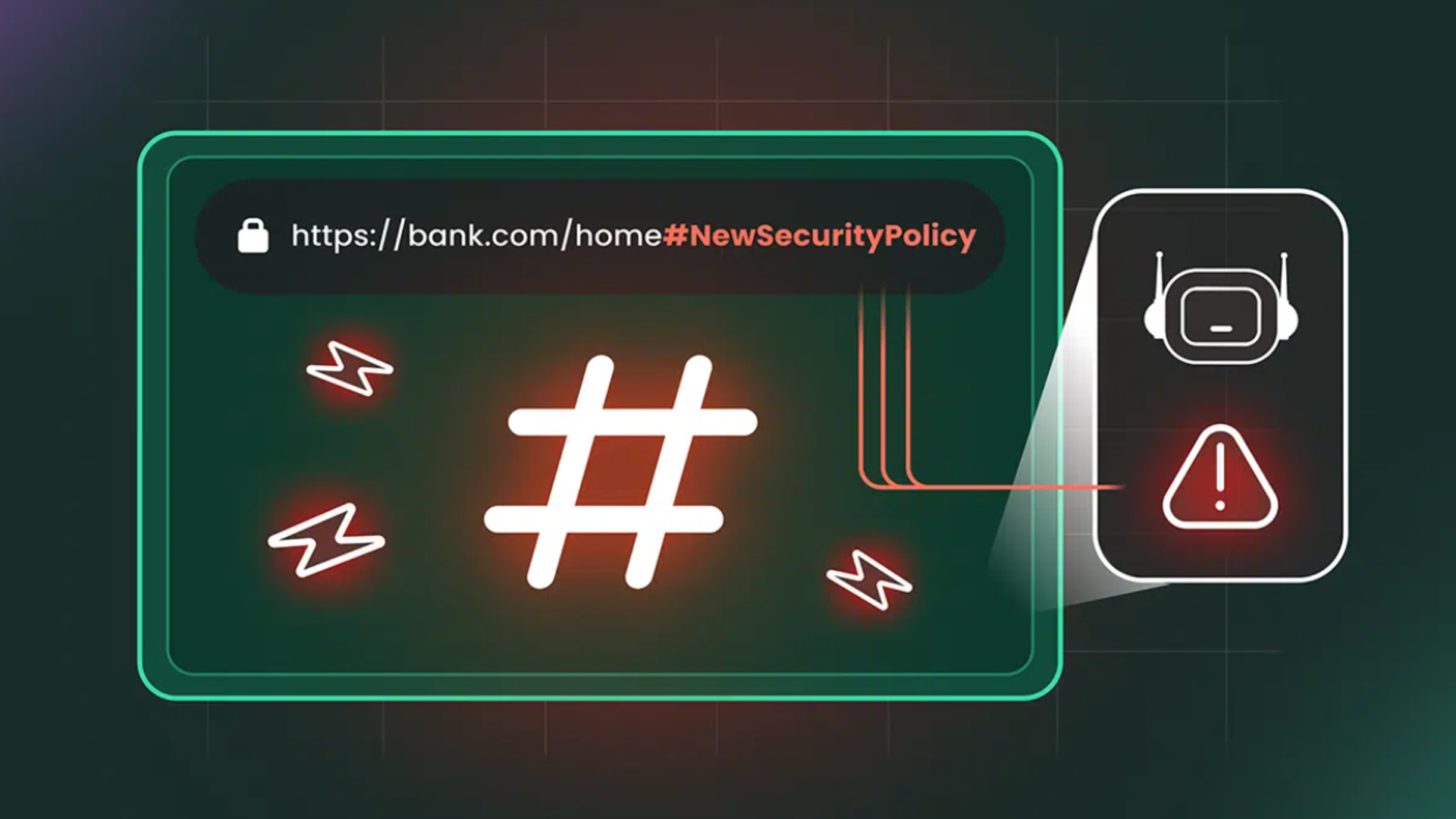
Many AI browsers are facing scrutiny after researchers detailed how a simple fragment in a URL can be used to influence browser assistants.
New research from Cato Networks found the "HashJack" technique allows malicious instructions to sit quietly after a hashtag in an otherwise legitimate link, creating a path for covert commands that remain invisible to traditional monitoring tools.
The assistant processes the hidden text locally, which means the server never receives it, and the user continues to see a normal page while the browser follows instructions they never typed.
Behaviour of assistants when fragments are processed
Testing showed certain assistants attempt autonomous actions when exposed to these fragments, including actions that transmit data to external locations controlled by an attacker.
Others present misleading guidance or promote links that imitate trusted sources, giving the impression of a normal session while altering the information provided to the user.
The browser continues to display the correct site, which makes the intrusion difficult to detect without close inspection of the assistant’s responses.
Major technology firms have been notified of the issue, but their responses varied significantly.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Some vendors deployed updates to their AI browser features, while others judged the behaviour as expected based on existing design logic.
Companies said defending against indirect prompt manipulation depends on how each AI assistant reads hidden page instructions.
Regular traffic inspection tools can only observe URL fragments that leave the device.
Therefore, conventional security measures provide limited protection in this scenario because the URL fragments never leave the device for inspection.
This forces defenders to move beyond network-level review and examine how AI tools integrate with the browser itself.
Stronger oversight requires attention to local behavior, including how assistants process hidden context invisible to users.
Organisations have to use stricter endpoint protection and tighter firewall rules, but these are only a layer and do not fix the visibility gap.
The HashJack method illustrates a vulnerability unique to AI-assisted browsing, where legitimate websites can be weaponised without leaving conventional traces.
Awareness of this limitation is critical for organisations deploying AI tools, as traditional monitoring and defence measures cannot fully capture these threats.
How to stay safe
- Limit personal information shared online.
- Monitor financial accounts for unusual activity.
- Use unique, complex passwords for all accounts.
- Verify URLs before logging into websites.
- Be cautious of unsolicited messages or calls claiming to be from financial institutions.
- Deploy antivirus software to protect devices from malware.
- Enable firewalls to block unauthorized access.
- Use identity theft protection to monitor personal information.
- Recognize that sophisticated phishing campaigns and AI-driven attacks still pose risks.
- Effectiveness depends on consistent implementation across devices and networks.
Follow TechRadar on Google News and add us as a preferred source to get our expert news, reviews, and opinion in your feeds. Make sure to click the Follow button!
And of course you can also follow TechRadar on TikTok for news, reviews, unboxings in video form, and get regular updates from us on WhatsApp too.

Efosa has been writing about technology for over 7 years, initially driven by curiosity but now fueled by a strong passion for the field. He holds both a Master's and a PhD in sciences, which provided him with a solid foundation in analytical thinking.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.