TechRadar Verdict
Acronis comes from the latin for 'cutting edge' and we feel Cyber Protect Cloud lives up to this name. Setup is one of the fastest we've experienced and the interface is incredibly easy to navigate. Threat detection (if properly configured) is shockingly fast and there's a free trial. What's not to like?
Pros
- +
Very fast setup
- +
Simple interface
- +
Advanced threat detection
Cons
- -
Complicated pricing model
Why you can trust TechRadar
For over 20 years, Swiss technology company Acronis has been developing top-notch security software. In October 2021, Acronis partnered with Addigy, the cloud-based Apple device management platform provider, for its latest integration of Acronis Cyber Protect Cloud.
Among many other inventions, Acronis' home country is famous for its exceptional timepieces. Despite the rather unwieldy name, Acronis claims that its Cyber Protect Cloud works along similar lines, incorporating many moving parts like anti-malware, antivirus, and endpoint management into one solution.
The question is whether Acronis Cyber Protect Cloud is one of the best endpoint protection software platforms. Let's find out.
Acronis Cyber Protect Cloud: Plans and pricing
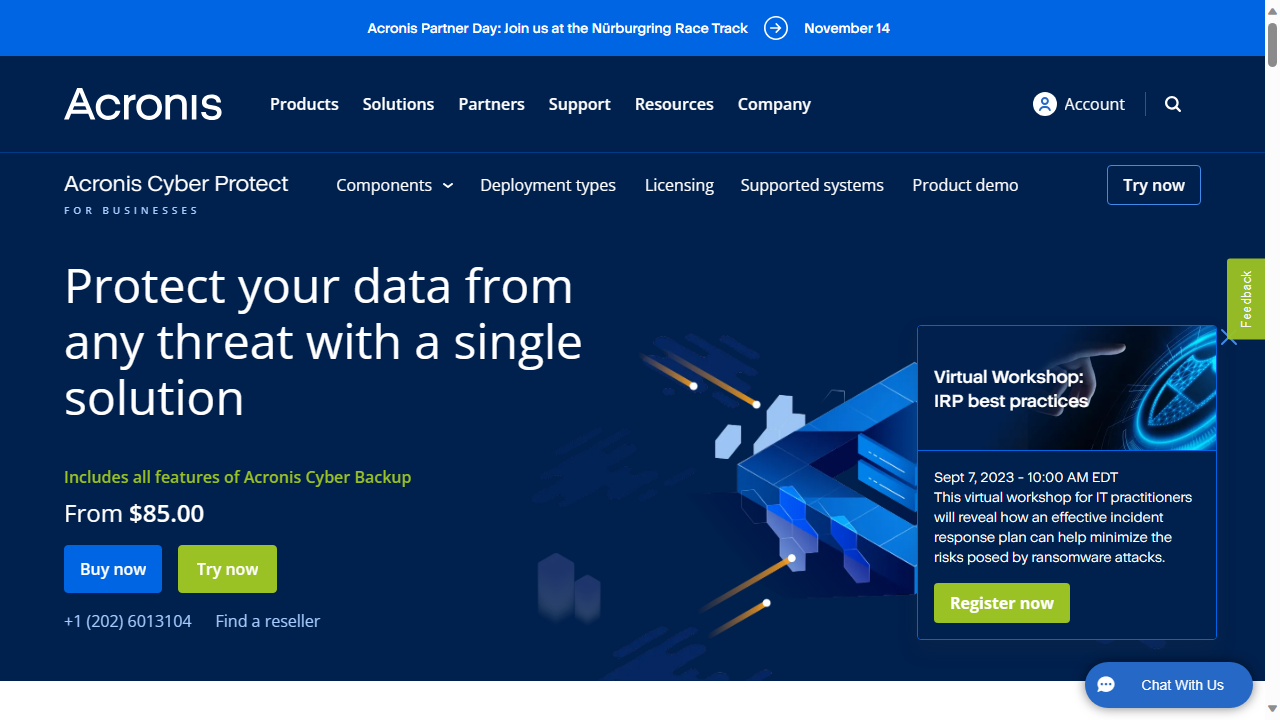
The more basic product, Acronis Cyber Protect, has three main pricing tiers. The 'standard' version costs $85 and is designed for 'small to medium' environments. The 'Advanced' version is for 'large IT environments' and costs $129. The 'Backup Advanced' tier costs $109. Each tier comes with 50GB of Acronis cloud storage, though if you opt for any of these, you'll need to set up your management server.
Alternatively, you can sign up for Acronis Cyber Protect Cloud, where the management server is located at one of the company's data centers. Cyber Protect Cloud has a detailed pricing page, but if you're disappointed if you're looking, you'll roughly estimate.
There are two main ways to pay for Cyber Protect Cloud. One is ''er workload.’'In other words, you pay per the number of devices or workloads protected. This includes apparent appliances like laptops, virtual machines, and servers. Acronis claims this pricing model is best for clients with fewer devices and more significant amounts of data on each one (servers come to mind). You can also store backup data in one of AAcronis'52+ global data centers, which is charged separately per GB.
Acronis Cyber Protect Cloud services can also be purchased based on the protected data volume. This pricing model is best for organizations with more workloads to protect, each with smaller data volumes, such as an office with individual workstations. By choosing this model, you can also benefit from volume discounts, making you feel financially savvy. You can save data further by storing it in a client-side location rather than in AAcronis'sdata centers.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
There is a minimum monthly fee depending on where clients are based and the currency in which they use. Acronis encourages interested visitors to its site to use its price calculator.
Acronis offers a free 30-day Cyber Protect trial without requiring payment information upfront.
Acronis Cyber Protect Cloud: Features
We particularly enjoyed the Acronis Cyber Protect Cloud overview video, which, despite the tinny audio, neatly sums up the product's main features.
As we'd expect from an endpoint security platform, Acronis has AI-based detection routines and analysis tools to detect and prevent malware and ransomware, brought together in 'Acronis Active Protection'.
Back in 2019, the platform even came 2nd place in a competition for which endpoint security products could best detect cryptojacking - the unauthorized use of someone else's computer to mine cryptocurrency.
Unlike many platforms we've reviewed, there's a clear emphasis on helping organizations to recover lost data. Cyber Protect can actually perform backups of an entire endpoint to the cloud via its agent software. The platform also supports a range of backup sources including NAS and network shares.
Perhaps the most lucrative feature of the platform however is the fact that it can be extended further with "advanced packs". These are add-ons which extend Cyber Protect's security further, such as "Advanced Email Security", which includes anti-phishing and anti-spoofing engines, as well as better protection against zero day exploits. These "packs" are available for purchase separately. The Acronis product page gives full details of each one's function and you can request a quote for these add-ons via the pricing calculator we mentioned earlier.
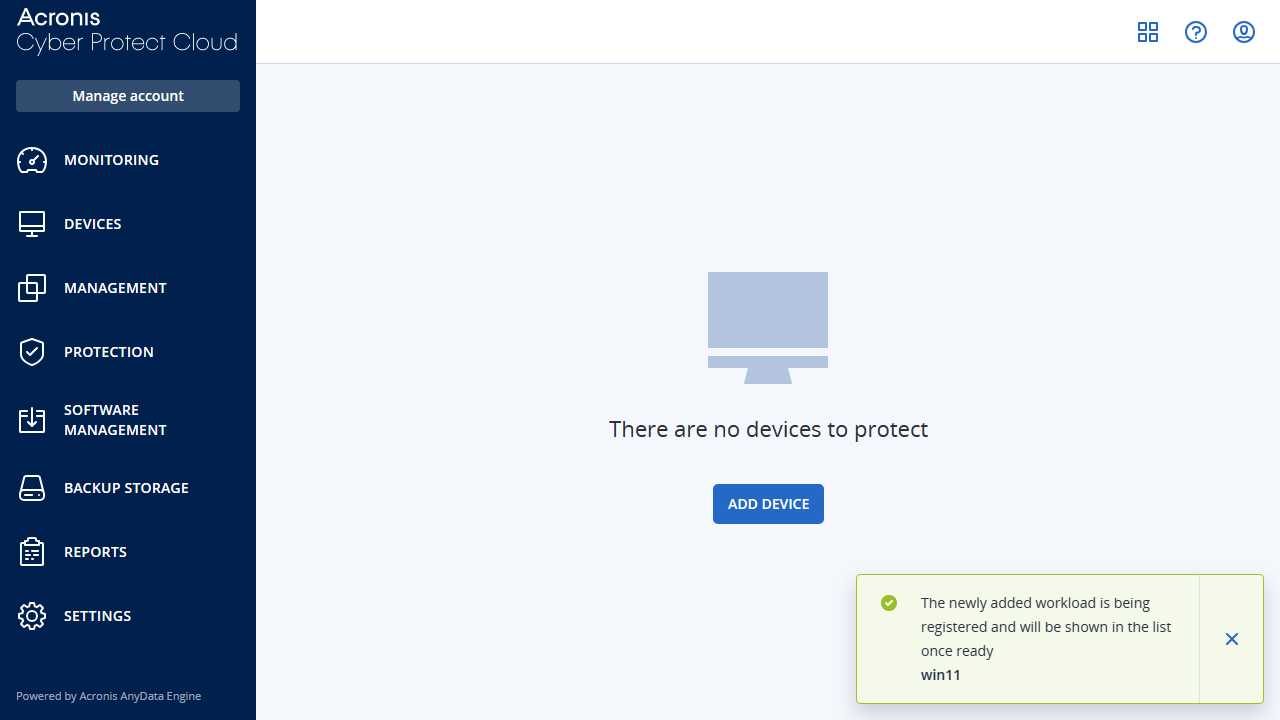
Acronis Cyber Protect Cloud: Setup
In order to download the free trial, we filled in a registration form and were quickly sent an activation link. This automatically led us to the Acronis Cyber Protect cloud console, which immediately displayed a button to 'Add Devices'.
This was impressive as other platforms we've reviewed make users hunt around for the correct link to deploy agent software. We noted that agent software is available for Windows, macOS, Android and iOS though deployment on multiple devices is supported on Windows only. Linux servers are also supported, though sadly there's no Linux client for endpoints.
After downloading the miniature installer, the necessary files were downloaded from Acronis in less than 2 minutes. We then had to click to "Register Workload" and confirm the registration code in order for the device to be enrolled by the cloud console. It's not clear what security benefit comes from this. We also noticed the device took around 5 minutes to provision, which is a relatively long time compared to other endpoint security platforms we've reviewed.
Once the agent was up and running we ignored its suggestion to apply the 'default protection plan' and chose to customize our own instead. This led us to the cloud console, where we applied the 'Cyber Protect Essentials'. True to its name, this includes features like real time threat detection.
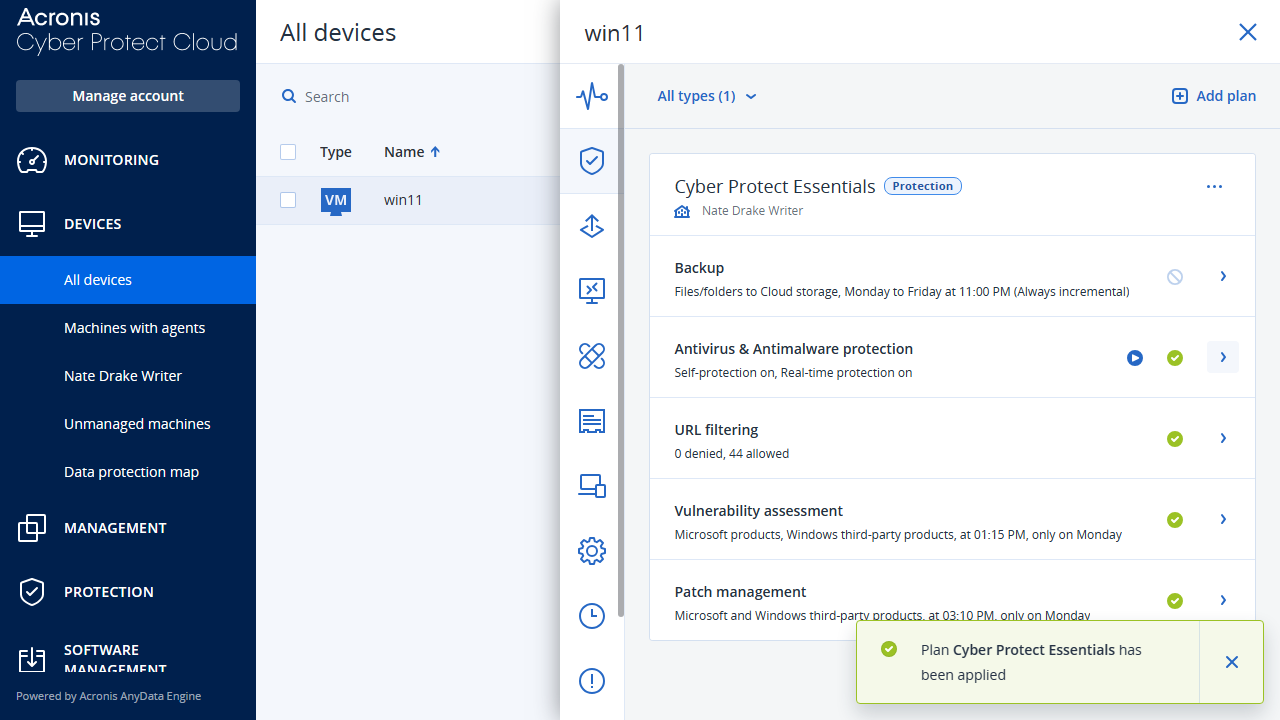
Acronis Cyber Protect Cloud: Interface
The Acronis agent has a very threadbare interface. Clicking on the system tray icon will display notifications such as the fact that real-time antivirus has been enabled. Clicking into the 'settings' area by default only contains options to encrypt backups and configure a proxy server.
The Acronis Cyber Protect Cloud console, on the other hand, is well laid out with just the right amount of data to provide helpful information without overcrowding the screen.
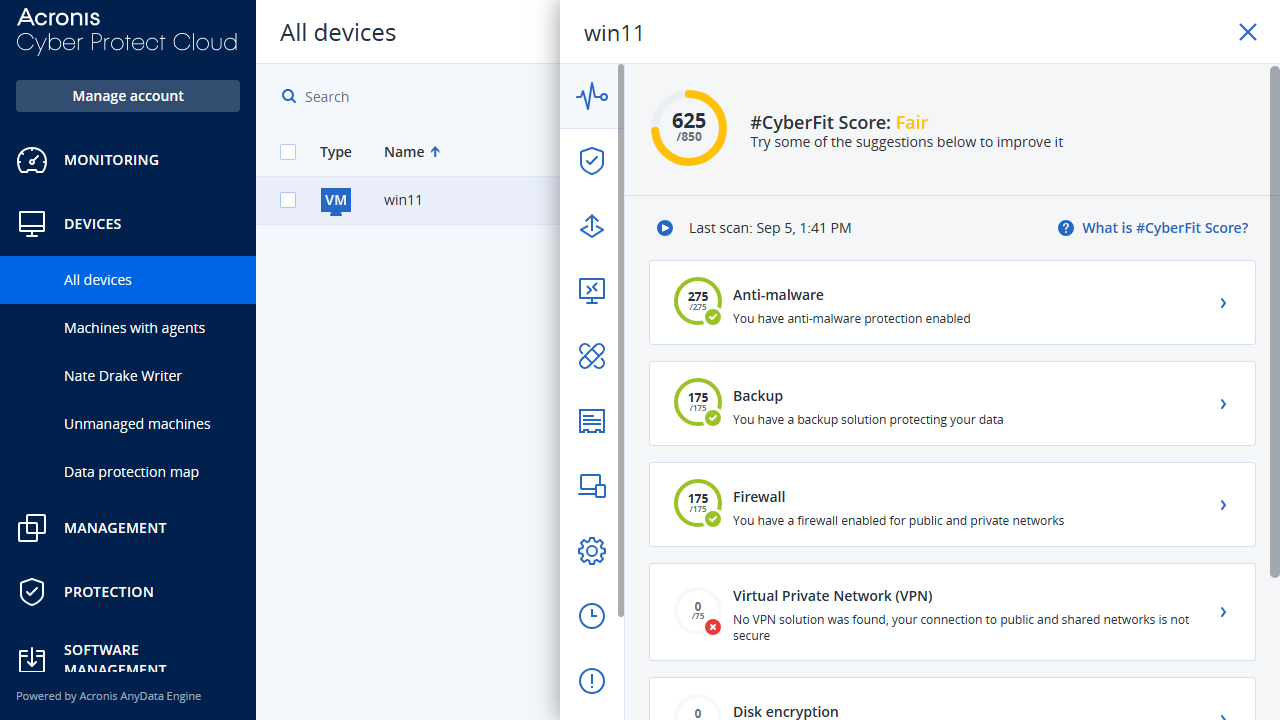
Navigation between sections is managed via the left-hand pane. The 'Monitoring' section, for instance, has an 'Overview' option which gives a rundown of all essential endpoint data. This includes the protection status of your endpoints, active alerts summary, patch installation status, and disk health status. This is also a good area to view the 'CyberFit' score Acronis' awards to each machine based on its perceived level of security.
If you click into the "Devices" section and select an appliance, a right hand pane appears offering links to helpful functions like recovering data and viewing the aforementioned CyberFit score. Our only small criticism of this pane is that it overlaps the 'Status' message for devices, so you need to hover your mouse over it to view the overall message.
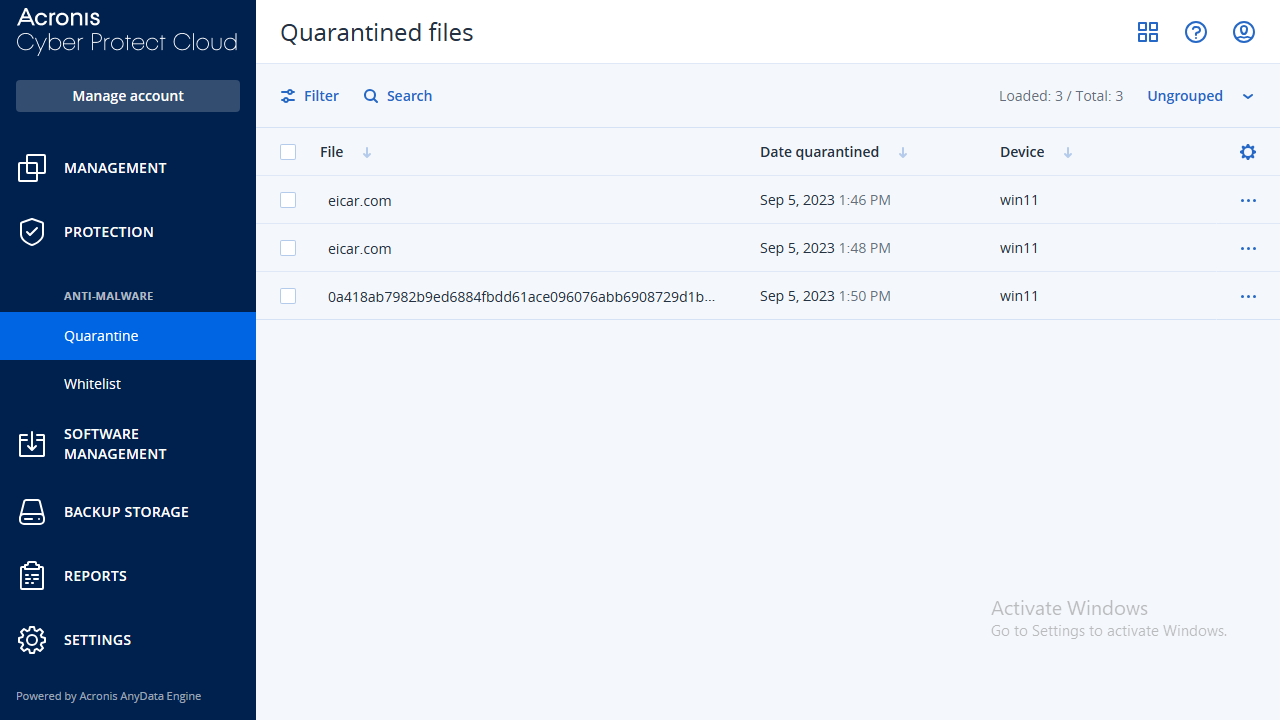
The 'Protection' section also deserves special mention, as it has a dedicated 'Quarantine' area where you can view suspicious files isolated by the platform.
Acronis Cyber Protect Cloud: Performance
Earlier we mentioned that we activated the 'Cyber Protect Essentials' plan using the Acronis Cyber Protect Console. This was because although there's also an 'Acronis Antivirus' plan, activating it didn't seem to install any new software.
Our first test for endpoint security platforms involves trying to download a fake computer virus provided by the good people of EICAR. We downloaded the file in compressed (ZIP) format using the Microsoft Edge browser on our Windows 11 test machine. Our first test after activating the 'Acronis Antivirus' plan didn't seem to have any effect but when we switched to 'Cyber Protect Essentials' (which includes real time protection), the file was immediately detected and quarantined.
Our next test involved using a new, real computer virus that we'd caught in the wild. We do this to check that an endpoint security platform can detect malware based on its features and behavior instead of just comparing files against a database of signatures. This time Acronis Cyber Protect passed our test with flying colors, immediately quarantining the file and correctly recognizing it as a 'trojan' virus.
Our final test was to log into the Cyber Protect cloud console to see which alerts had been generated. The 'Overview' section provided a quick summary of the malware files, while the previously mentioned 'Quarantine' area of the 'Protection' section gave a full rundown. From here it's also possible to delete infected files or restore legitimate files that have been incorrectly classed as malware.
Acronis Cyber Protect Cloud: Final verdict
Acronis Cyber Protect Cloud may be difficult to price up but there's much to love about the platform. In the first instance, setup can be done in moments: you can even set your password when you fill in the registration form, so can log into the cloud console right away.
Although the agent software doesn't come with many configuration options, we were also delighted at how easy it was to deploy, as the console immediately took us to the download link on first login.
In our tests threat detection was a little off at first but we put that down to our decision not to deploy the default basic protection settings, which would have stopped the malware in its tracks. We were also impressed to see clear detection alerts in the main cloud console, not to mention an email a short while later that mentioned the infected files as part of the 'Daily Status Report'.
The overall interface is very clear and doesn't overwhelm users with options, though as we said Acronis may want to rethink placing panes on both sides of the screen in the 'Devices' section.
Although there's no custom firewall or e-mail scanning, this can be added via the "packs" we mentioned earlier. We're also impressed that the agent software is supported on a number of endpoint devices, with Linux being the only exception.
Given that there's a free, no-obligation 30-day trial, there's no reason not to take Acronis Cyber Protect for a test drive yourself to see if it meets your organization's needs.
We feature the best cloud firewalls.
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.