How user accounts, rights and ownership work in Linux
Create users and set passwords, permissions and ownership in the Linux terminal
Almost all of the user management commands require root access. The superuser, often referred to as root, can do anything anywhere, regardless of any permissions. So how does a humble user do anything that requires root privileges? There are two ways of doing this.
The traditional way is to use the su (for switch user) command, which enables you to become another user, provided you know their password.
Run su in a terminal (it switches to root if you don't specify a user) and it will ask for the root password. Once you've entered this you are root in that terminal session and can do anything you like (cue maniacal laughter).
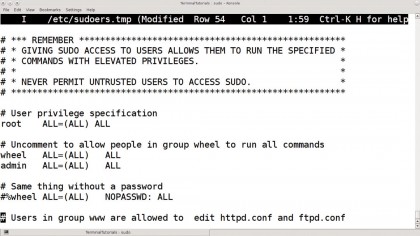
Of course, this is a bit risky, especially if you don't log straight out after doing what you need. It also means that you have to give the root password, and therefore full access, to any user that needs to run a root command. That's why sudo was invented.
The sudo command is used to run individual commands as root (or another user) but doesn't require you to know the root password. Instead, the root user must have enabled you to run some or all commands as root, so it asks for your password.
The normal installation of most distros enables the first user created to have sudo rights to everything, without ever having to log in as root or spread the root password. In fact, some distros have no root password by default and sudo is the only way to run admin commands.
sudo can be used to give individual users rights to execute only specific commands, plus it records every command it runs in the system log, along with who ran it, giving a far more secure and accountable system.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Current page: Becoming root
Prev Page Managing users, rights and ownership Next Page Different filesystems