An enemy in disguise: Why cybersecurity teams are being set up to fail
Software vendors are playing into the hands of cybercriminals

Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
Every year, businesses spend billions upon billions of dollars on software and services designed to shield against cyberattacks. But the game is rigged; the defenders are set up to fail, no matter how much they spend.
The security posture of an organization is determined by a complex web of factors, from the level of cybersecurity training among employees to the sensitivity of the firewall, level of network oversight and ability to stay abreast of evolving malware threats.
However, irrespective of the quality and extent of a company’s defenses, there is one force always pulling in the opposite direction: software vulnerabilities. If an attacker is handed a route into the network on a silver platter, there is little their victim can do to stop them.
“We don’t speak enough about vulnerabilities; there has been a tremendous increase in volume and the situation is close to being out of control,” Laurent Celerier, EVP of Technology and Marketing at Orange Cyberdefense (OCD), told TechRadar Pro.
“Behind each vulnerability is an opportunity for attack, and cybercriminals are moving through the kill chain faster and faster.”
The simple reality is this: businesses are fighting an uphill battle against an ever-growing volume of attacks, dragged down by factors outside of their control.

A problem of incentives
Although cybercriminals abuse various attack vectors to gain access to corporate networks, data from multiple sources indicates that a significant portion (some say the majority) of all cyberattacks can be traced back to a software vulnerability.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The number of detected vulnerabilities is also on the rise. According to OCD intelligence, more than 17,000 bugs were discovered last year alone. A portion of this rise can be attributed to an improvement in detection capabilities, but the trend is concerning nonetheless.
There is an extent to which vulnerabilities are inevitable; the price of doing business in the world of software development. Some modern apps are comprised of many millions of lines of code, contributed by hundreds of different developers, so mistakes are bound to happen.
The dependence on open source components has also increased the likelihood of bugs making their way into applications. The fact the code is available for anyone to dig through doesn’t necessarily mean it has been subjected to sufficient scrutiny.
However, there are certain steps stakeholders can take to mitigate risk associated with vulnerabilities. For example, IT departments could focus on optimizing patch management processes to the greatest possible degree, ensuring devices and servers remain vulnerable for the shortest possible period. Software vendors could also play their part by committing to a more rigorous update verification process.
In practice, though, things are rarely so straightforward. In a world in which attracting custom depends on the ability to innovate faster than the competition, vendors cannot afford to linger over the checks and balances for too long, while internal IT teams are frequently stretched to capacity.

“At this stage, the IT ecosystem is not incentivized to bring to market better software, because they are all in competition and need to move fast. This means they publish solutions that are not of sufficient quality,” said Celerier.
“What’s more, most of the cost for managing vulnerabilities falls on the customer, who has to test the new version and stop production to deploy the patch, which takes time and expertise.”
To help resolve these issues, Celerier says a culture of zero tolerance for poor-quality software releases needs to be established. But equally, he concedes that a heavy-handed approach could easily backfire.
“There is a need to shame vendors for putting out poor products, but this tactic has collateral damage: it could end up with people not reporting vulnerabilities,” he explained. “It’s quite tricky.”
In a separate interview with TechRadar Pro, this problem was raised from a different perspective by Sudhakar Ramakrishna, CEO of SolarWinds, which in 2019 suffered what turned out to be one of the most serious cyberattacks in history.
“There is still a lot of victim shaming that happens, so companies often end up fixing problems without saying anything about them. There is definitely hesitation to speak up,” he told us.
A situation in which software vendors are rebuked for the poor quality of their releases and companies scolded for falling victim to attack is likely to produce a culture of cover-up that would only aggravate the problem.
The wrong focus
Another way in which the security industry and IT professionals are handing the advantage to the attackers has to do with the focus of investment.
Typically, cybersecurity companies operate across small segments of the cybersecurity chain, leaving the rest to other vendors. For example, an organization might provide detection and response services, but not the facilities necessary to protect against attacks in the first place.
Hugues Foulon, CEO at OCD, told us that a failure to divide security investment across the chain in an appropriate way is contributing to the ease with which hackers are able to execute attacks.
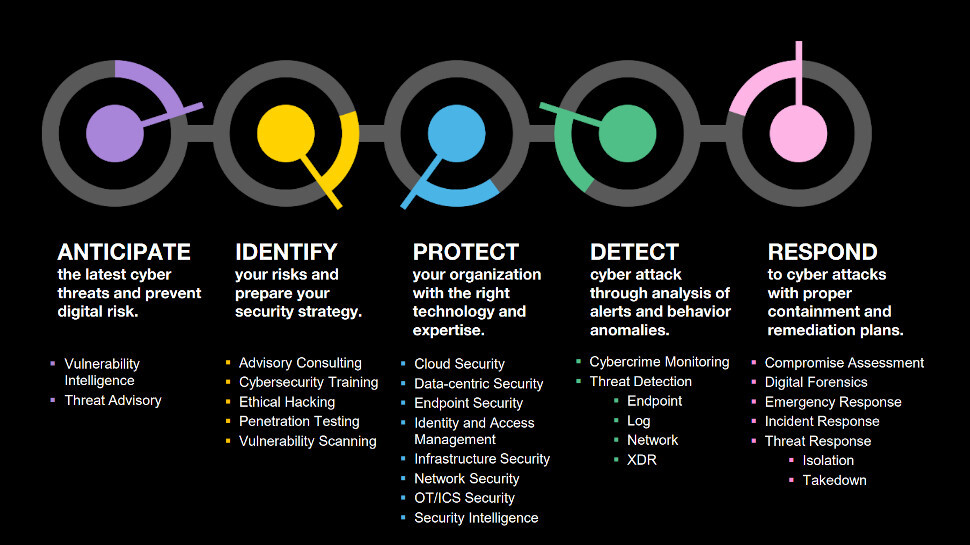
Instead of investing heavily in the ability to anticipate new cyber threats and respond to attacks when they occur, most companies sink the majority of funding into technologies designed to protect. “The curve is backwards,” he explained.
“The threat of today is not the same as the threats of last year, so it’s always important to be aware of evolutions in the threat landscape. Based on threat intelligence, we need to anticipate what might happen, and if an attack takes place, be able to put a remediation plan in place as soon as possible.”
The focus of resources and investment among security vendors might also be allocated in a more optimal manner, suggested Foulon, especially with regards to emerging technologies like artificial intelligence.
“To be completely honest, a lot of people are talking about AI in cybersecurity, but the reality is quite different. We are more humble at OCD - we’re talking mostly about process automation,” he said.
“Yes, there is AI, but it’s not at this stage priority number one [for OCD]; the level of maturity is low. This is not what our competitors are saying, but I doubt they are doing what they are claiming to the outside market.”
The allocation of funding is a difficult question across all quarters of all businesses, but where cybersecurity is concerned, the stakes are particularly high. With the cost of data breach remediation climbing to an all-time high, the consequences of a failure to invest appropriately are self-evident.
Is there a solution?
The combination of risk created by software flaws and the inefficient allocation of funding has left businesses more vulnerable to attack than perhaps they should be.
Most worryingly, market forces have created a situation whereby attempts to shore up defences are undermined by factors beyond the victim’s control. Until economic incentives are realigned, software vendors will have little cause to tighten up their patch verification practices.
Prompted for a solution to this problem, Celerier suggested that new regulation is needed to compel vendors to prioritize security when developing software updates. “In France, we love regulation,” he quipped.
He also suggested that the move away from on-prem will go some way to easing the patch management problem naturally, because pushing an update to the cloud is much simpler than asking IT teams to perform a manual install across thousands of servers.
More generally, OCD also believes it is important for security partners to cover off each step in the cybersecurity chain - from identifying areas of risk, through to shielding against attack and incident remediation. This way, businesses need to liaise with only one third-party, reducing logistical complexity and minimizing the likelihood of an attack slipping through the cracks.
A prospective customer might be justified in questioning whether it is truly advantageous to work with a single jack-of-all-trades, rather than multiple specialists. But OCD says the proof of its model is there for all to see.
Not only does the company rely on its own products to shield its internal network - “in the IT department, we drink our own champagne,” said Celerier - but also boasts an unblemished track record for blocking one of the most potent threats: ransomware.
There may be no “magic bullet” solution for the cybersecurity conundrum businesses face, OCD concedes, but a commitment to engaging proportionately with every possible tool at the defender’s disposal is an important first start.
- Shield your devices against attack with the best antivirus services around

Joel Khalili is the News and Features Editor at TechRadar Pro, covering cybersecurity, data privacy, cloud, AI, blockchain, internet infrastructure, 5G, data storage and computing. He's responsible for curating our news content, as well as commissioning and producing features on the technologies that are transforming the way the world does business.