Using email headers to verify an email’s authenticity and the future of DMARC
Authentication protocols establish the identity of an email

When someone receives and opens an email, they see the parts of the message that most people care about.
In addition to the message content (the body), the recipient will typically see a few header fields, such as From:, To:, Subject:, and Date: that convey basic information about the claimed origin and topic of the message.
Those headers represent just a small fraction of the headers that are part of the message.
- The best email hosting providers
- The 30 most-asked email questions answered!
- Best email clients: Free and paid apps and software
The method for making hidden headers visible will differ depending on the mailbox provider. In Gmail, you can access the email header by clicking on the three dots in the upper right corner of a message and then “Show Original.”
Other providers will have a choice on a menu such as “Show Message Source” or words to that effect.
You’ll know you’ve found the right place when you see lots of text with lines starting with words like “Received:”, “Return-Path:”, and others, including the one we want to discuss “Authentication-Results:”, which will look something like this:
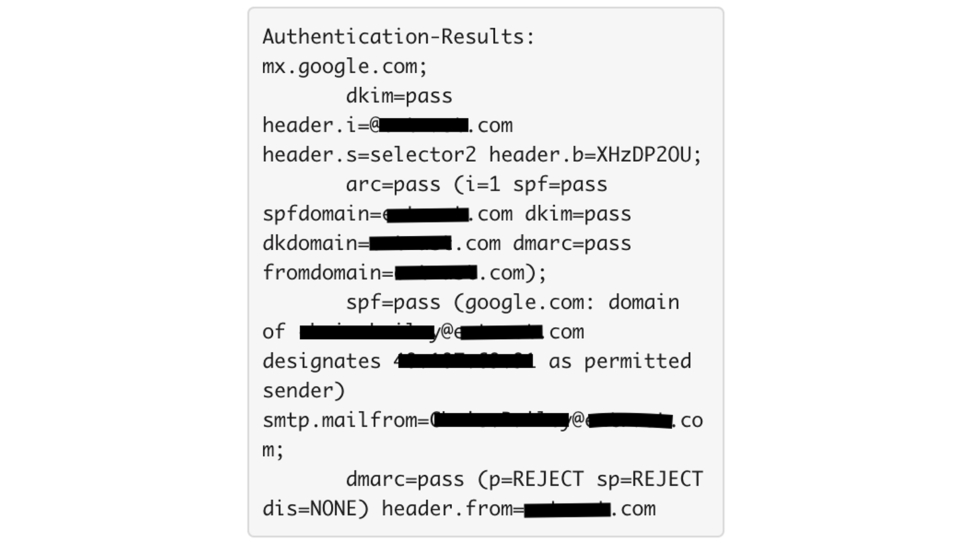
Email authentication protocols, including SPF, DKIM and DMARC, are used to establish the identity of the parties responsible for a given message. Mailbox providers will record the results of the authentication checks done on a message in this header, and here we can see that this message received “pass” verdicts for all three.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The mailbox provider will then use the information recorded in this header and other information it knows about the responsible parties to determine where to place this message in the recipient’s mailbox.
As a user, you may want to take a peek at this header if you’re curious about why a message ended up where it did. Note that fail verdicts here may make the message more likely to be placed in the user’s Junk folder, but pass verdicts are not guarantees of placement in the Inbox.
These protocols reliably establish the identity of the responsible parties. If those parties are known to the mailbox provider to be senders of unwanted mail, it makes the mailbox provider’s decision to put the message in Junk easier.
Senders who are trying to get their authentication practices buttoned up can also make use of the “Authentication-Results” header, but it’s not their best tool for doing so.
For the small sender using one server and one IP address, repeated cycles of "send message, look at Auth-Results header, adjust, repeat" is an approach (albeit a tedious one). However, for anyone sending with any volume, the “Authentication-Results” header is just a grain of sand on the beach of mail that a domain owner sends.
For them, DMARC aggregate reports are much better tools because instead of being overly focused on the minutiae of mail to one mailbox at one provider, domain owners can focus on the bigger holistic view of their entire mail sending program.
With DMARC:
Senders can receive DMARC aggregate reports that aggregate data on the authentication information for every email sent using their domain.
Senders can also request a class of handling for a message that fails authentication. However, enforcement is a critical component of DMARC and as of now, only 13% of DMARC users are at enforcement. Without it, receivers are not provided with directions on how to handle a message that fails authentication, meaning spoofed emails can still make it into the inbox.
For the recipient, DMARC aligns authentication results from SPF and/or DKIM with what the user sees in the “From” field of their email.
As DMARC adoption grows, domain owners can be confident that only approved senders are using their domain, and end-users can be increasingly confident that the message in their inbox is from who it says it’s “From” without any additional digging into email headers — but we are still far from reaching optimal protection.
Where is DMARC headed?
The DMARC standard was released in 2012, and, in early 2020, the number of domains with published DMARC records nearly surpassed one million. This is an increase of 70% over 2019 and 180% from 2018.
Just publishing a DMARC record doesn’t sufficiently protect a domain from spoofing. Yet, of the nearly 1 million organizational domains with DMARC, only 13% are at enforcement and truly protecting domains from impersonation or bad actors.
Today, DMARC is a standard used by 80% of the world’s inboxes and while DMARC interest continues to grow, expertise isn’t keeping the same pace.
What comes next?
Close the gap between published records and enforcement
DMARC contains subtleties that are tricky and tedious for most companies to implement. What’s more, it relies on two other standards, SPF and DKIM, which are themselves tricky to implement and error-prone.
We’ll likely see a shift to more direct information about the technical aspects of DMARC. Already, free tools exist to overcome the often-complicated first step of a DMARC initiative that would typically require manual XML report analysis.
Providing domain owners access to DMARC visibility without the technical burden is just the first step in making DMARC enforcement accessible for everyone.
No Auth, No Entry?
The question on many people’s minds: Will DMARC ever be required? In January 2018, the Department of Homeland Security required federal agencies to implement DMARC on email-sending domains under the BOD 18-01 directive but a government mandate for other industries is unlikely.
However, you may have heard the term “No Auth, No Entry.” No Auth, No Entry refers to a possible future where one or more mailbox providers choose to enforce a policy of refusing any mail that is not authenticated. While there has yet to be a public commitment, domain owners can still reap the benefits of DMARC now and be prepared if this ever comes to fruition.
Leverage DMARC as a foundational element of future email features
DMARC opens doors for other security standards and specifications benefitting all teams from IT to marketing. One example is Brand Indicators for Message Identification (BIMI), the new email specification enabling brand logos to display within supporting email clients. To be eligible for BIMI (and get the 10% increase in email engagement that comes with it), a company’s DMARC policy must be at enforcement.
Forrester estimates a typical, large enterprise can save $2.4 million per year with a DMARC policy at enforcement. Organizations need DMARC to protect email security, company reputation and customers, to increase customer engagement and to save money. DMARC isn’t going away and it will be further prioritized in the coming years.
- Also, here's our rundown of the best ransomware protection money can buy
Peter Goldstein, chief technology officer and co-founder, Valimail.