How to protect yourself from cryptomining
Don't let your computer get hijacked
Last year, word spread that popular yet dubious torrent site The Pirate Bay had embedded cryptocurrency mining software on its site, stirring up widespread controversy. If it wasn’t clear then, it is now: The Pirate Bay was exploiting its visitors by hijacking CPUs, or processors, to do the bookkeeping of cryptocurrency networks like those of Bitcoin and Ethereum.
If this sounds like shady practice, it is. We are talking about The Pirate Bay (TPB) after all. In its defense, all the organization had to add was that it was trying to earn revenues to make up for its gradual elimination of advertisements altogether. In effect, it’s a clever way to make money from the swaths of TPB users sporting ad-blocking extensions.
Unfortunately, ‘borrowing’ someone else’s computer to do your bidding is a devious strategy, even if it is a legal gray area. Malicious or not, a website that cryptomines without your consent is worrying to the point that you’d probably look to steer clear of such sites, or take measures to protect your computer.
To that end, here we'll show you how to protect yourself from cryptomining, whether or not the sites you’re visiting ask your permission first.
Use an extension
There are plenty of third-party applications available for a number of different browsers that can be used to defend against cryptocurrency hijacking.
Since Google Chrome is one of the most popular vehicles for perusing the web, we suggest using No Coin and MinerBlock.
Equipped with these utilities, you can essentially block cryptocurrency as easily as you could, say, pop-up ads. Extensions aren’t the be-all and end-all solution, but they are a quick fix for those seeking a moderately effective safeguard while parasitic websites whip up new ways to irritate.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
No Coin and MinerBlock in particular allow users to blacklist and whitelist sites, in addition to giving you the option thwart all cryptomining attempts as they’re intercepted.
Alternatively, you can get to the root of the problem by installing a Javascript-blocking extension like ScriptSafe, though note that it might also obstruct whatever it is you’re trying to accomplish on a website to begin with.
How to use No Coin
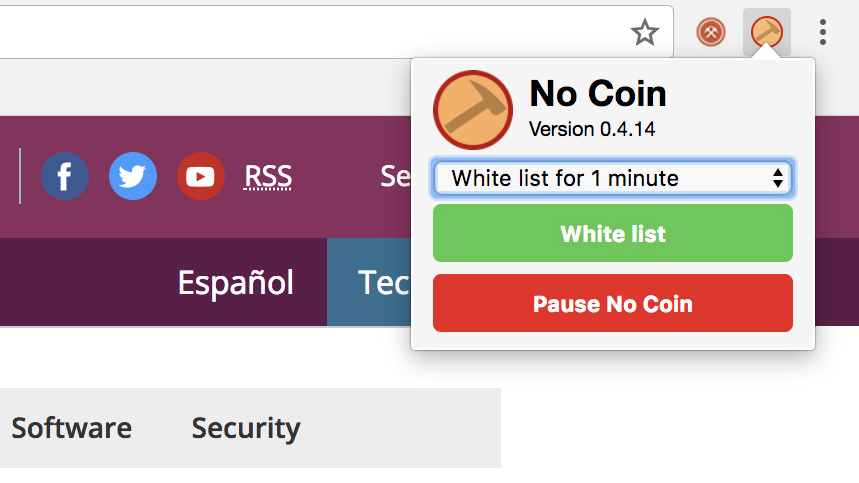
There are few differences between No Coin and MinerBlock. In fact, you really only need one installed at a time in order to achieve solace. Both are extremely easy to use, though we will say that MinerBlock is considerably heavier on features. Meanwhile, No Coin is built into the Opera browser, which may be enough of an incentive to make the switch.
No Coin is a lightweight client that automatically starts doing its job upon arrival. After being installed, it blacklists any and all cryptomining endeavors that it finds. It gives you the option to whitelist all sites for one minute, 30 minutes or permanently, depending on your preference.
You can pause No Coin, too, but that’s where its functionality basically starts and ends – MinerBlock is a little more versatile.
How to use MinerBlock

With MinerBlock you can know just how many entities are trying to use your computer to mine for virtual coins on the internet at any given time.
You can also add certain sites to your whitelist, as you can in No Coin. However, MinerBlock also has a settings button for manually whitelisting sites by their domains and filtering out specific paths. Likewise, you can toggle the block count on or off if you find it’s more distracting than useful.
Both No Coin and MinerBlock are free, although you can donate to MinerBlock on PayPal. Both services appear to be transparent in offering ways to contact their respective developers for feedback regarding updates and changes.
Use antivirus protection
It sounds obvious, and that’s because it is. Virus protection is an absolute necessity. While it’s built into our computers in one way or another, you can also download malicious software (malware) protection such as BitDefender, Kaspersky or any combination of the best free antivirus solutions we recommend.
By doing so, you’ve taken the first step towards eliminating any chance of cryptominers trying to remotely hotwire your computer and take it for a spin. To determine whether your case is bad enough to justify going through the effort of configuring antivirus software, open Task Manager if you’re on a Windows PC, or Activity Monitor if you’re on a Mac.
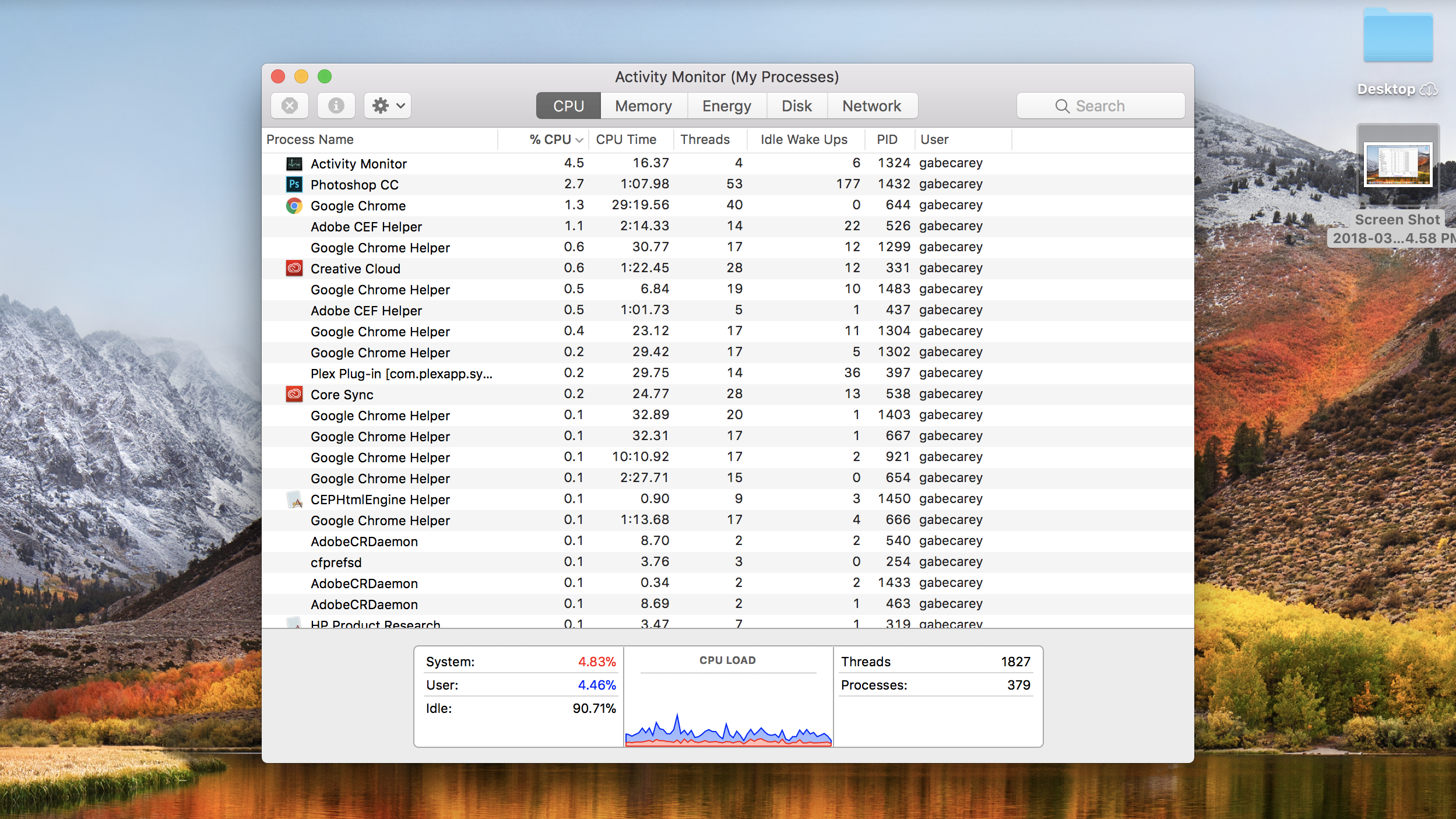
The former can be launched by pressing Ctrl+Alt +Delete, and the latter can by pressing Command+Spacebar and subsequently typing ‘Activity Monitor’. From there, you can view your CPU load, or just how stressed out the computer is, for instance.
Should your system be experiencing heavy loads nearing 100%, something is probably up. Close the application that’s doing the most damage, then open your antivirus program of choice and run a basic scan.
If a suspicious file or program is found to be hindering your system, remove it immediately. If it’s a program, it may even be a good idea to use a total uninstaller like Revo to rid your system of every last trace.
Rules for websites
And what if you operate a website yourself, and are tempted to dabble in a little cryptomining? Legal though it is, the controversy surrounding cryptomining is all about consent and transparency. The more honest your website is at admitting that its using visitor resources to do the blockchain’s book-keeping, the happier your visitors should be.
Better yet, make sure you’re clear about what data is being collected amid the mining. It’s not ideal to have visitors worried that intelligence agencies, for example, are piggybacking off your data-collection algorithm at the same time that you’re hijacking those visitors' CPUs for the sake of earning a profit.
We get that the internet is changing. But it might not be a bad idea to review the Salon.com method – that is, giving visitors the choice between having ads enabled, or suppressing them and instead allowing your site to exploit their unused computing power.
Securing your digital lifestyle doesn’t have to be a tedious or expensive process. You can achieve that in the next 60 seconds by downloading a trial of CyberGhost VPN here, risk-free.
