TechRadar Verdict
Ping Identity provides peace of mind to users, helping to protect their accounts from security breaches and comply with regulations through their PingOne solutions. With just one secure platform and multiple authentication options, users can access all their applications and services with a single, unified identity. To get started, all users need to do is set up a Ping Identity account and connect it to their existing identity service.
Pros
- +
Scalable (if you use other products from the “Ping family”)
- +
User friendly
- +
Multiple authentication options
Cons
- -
You have to bundle features to get the most out of it
- -
Support documentation needs more work
Why you can trust TechRadar
PingOne is an ideal solution to secure access rights management across multiple devices. It offers a unified console, single sign-on, and connection security with a companion application. Moreover, it can integrate seamlessly with other Identity Access and Management (IAM) systems such as Active Directory, Azure AD, CA Technologies, Oracle, and IBM. Enjoy effortless authentication for all your mobile, tablet, laptop, and desktop devices with PingOne.
Want to try Ping Identity? Visit the website.
Perimeter 81 is a Forrester New Wave™ ZTNA Leader
Ditch your legacy VPN hardware and automate your network security with ZTNA. Secure remote access from anywhere with just a few clicks. Onboard your entire organization in minutes, not days. Learn why Perimeter 81 is one of TechRadar's choices for the best ZTNA security providers. Download the report.
Plans and pricing
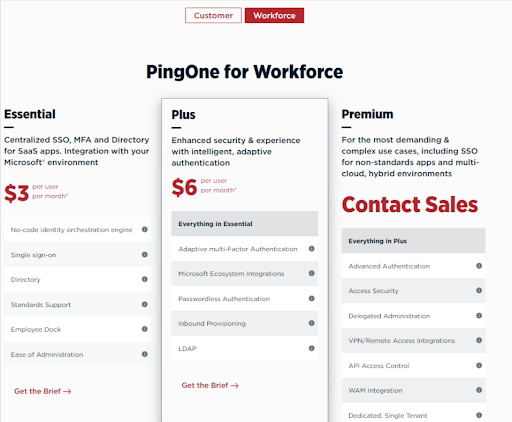
Similar to Okta, Ping Identity has made it very complicated to choose the right pricing plan for your business if you are a small business owner. We start off with the firm’s Workforce plans, where we have three plans, the Essential, which costs $3 per user per month, Plus at $6 per user per month, and the Premium plan, for which you will have to go through the sales department to get a custom offer. The main differences between the plans relate to the functionalities the users have at their disposal, with SSO coming in as standard even with the lowest plan offering.
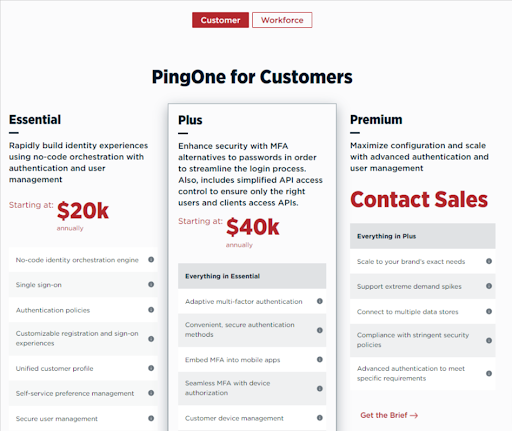
Next, Ping Identity offers their Customer pricing plans, which also have three levels. The Essential plan costs $20,000 annually, the Plus $40,000 annually and for the Premium you will have to contact sales.
Both Workforce and Customer plans have the option of 30-day trial, which could help you choose the right plan for you and your company.
Features
PingOne offers powerful Multi-Factor Authentication capabilities, which include passwordless authentication, eliminating the risk of attack and removing the frustration of memorizing multiple passwords. Adaptive to the situation, it can utilize frictionless, behavioral, and contextual factors such as IP address, geolocation, and timestamps to determine any potential risks. Plus, their Single Sign-On feature allows users to access multiple applications with one single set of credentials, saving admins time by lessening password reset requests and discouraging the use of weak or recycled passwords.
Risk management also plays a key role, as it integrates with authentication flows and policies to track and notify any events during user sessions. It rates, and groups risk signals, displaying any risk associated with the user's device and delivering a risk score. Thus, administrators are better equipped to make the best decision for granting access with the help of Ping's intelligent authentication providing risk signals and evaluates user behavior according to context.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Interface and in use
For the user, PingOne couldn't be simpler. With one click of the URL provided, usually in the form of an icon on their desktop, they'll be in the PingOne cloud. For the first-time user, the connection procedure is quick and easy, and afterward, their desktop is populated with the apps to which their organization has given them access to. System administrators can also set up groups and link with Active Directory and a range of other settings to cater to their organization's needs.
Accessing cloud-based applications is a simple process: the user clicks on the icon of the desired application on their desktop and is taken directly to PingOne, where they are securely authenticated. For extra security, strong authentication can be used. After this, a token exchange happens to confirm the user's identity, and they'll be connected to the application. It's all seamless and invisible to the user.
Support
The support the company offers is comprehensive, starting off with business phone numbers that will link you directly to customer support. If you are not a “phone person,” you can create a case for the firm’s support team to follow up on. A step up from some of the competitors is an offer for various certificates when it comes to using PingOne that users can pursue.
A detailed documentation section is available, but the documents tend to be heavy on technical jargon, which makes them harder to use for non-tech people. But fear not; there is a community forum with a few moderators where you can get answers to your questions. And finally, there is a Q&A section on the site, rounding out the comprehensive support users get.
Security
At Ping, Information Security Management System (ISMS) is based on top industry standards, including ISO 27001 and NIST 800-53. The commitment to security is evidenced through the ISO 27001 certification, which the company has held since 2018. Every year since 2013, Ping Identity has been getting Identity as a Service (IDaaS) evaluation via SSAE 16 SOC2 Type II certification. There are also third-party assessors who audit products and control the environment to make sure security measures are working as intended.
The competition
Okta is a formidable rival, offering an abundance of features often hidden within its various pricing plans. Requiring more technical expertise, Okta provides an analogous service and in some areas, even superior choices when compared to PingOne.
In contrast to both PingOne and Okta, Twingate offers much less yet stands out with its granular security configuration and lower prices.
Final verdict
PingOne Cloud Platform is an advanced, cloud-based product with exceptional security and management protocols delivered on a single, highly-scalable platform. Seamlessly integrated with other software, it fits into existing workflows with ease.
No passwords are necessary thanks to its frictionless sign-on capabilities, meaning added risk-mitigation. For enterprises with broad customer usage, like retail, and businesses needing the highest level of identity security for compliance or confidentiality - like government, financial services, and healthcare - PingOne Cloud Platform is the ideal solution.
- Check out our best business VPN
Sead is a seasoned freelance journalist based in Sarajevo, Bosnia and Herzegovina. He writes about IT (cloud, IoT, 5G, VPN) and cybersecurity (ransomware, data breaches, laws and regulations). In his career, spanning more than a decade, he’s written for numerous media outlets, including Al Jazeera Balkans. He’s also held several modules on content writing for Represent Communications.

