TechRadar Verdict
As far as Endpoint Security goes, if Carbon Black Cloud can't do it, it's not worth doing. This platform has incredibly powerful threat detection capabilities and provides an easy to navigate interface for protecting your infrastructure.
Pros
- +
Advanced threat detection
- +
Online simulator
- +
Fantastic interface
Cons
- -
Vague pricing model
Why you can trust TechRadar
For over 25 years VMware has been developing cutting edge virtualization software and leading the way in cloud computing. VMware Carbon Black (formerly Bit9) was acquired by the virtualization giant in 2019. The company has a specific emphasis on cloud-native endpoint security solutions.
Its creation, VMware Carbon Black Cloud Workload Protection, provides vulnerability assessment and inventory management for workloads hosted on vSphere ( VMware's own suite of server virtualization products) but VMware claims that this protection can be extended beyond their own workloads to your endpoints such as desktops, laptops and servers.
As such in theory, the platform allows organizations to manage and protect any number of endpoints via a single agent and console.
So, is this platform one of the best endpoint protection software solutions, or is it better to stay carbon neutral? Read on to find out.
VMware Carbon Black Cloud: Plans and pricing
Despite a detailed product page, VMware encourage interested parties to 'talk to an expert' if they wish to deploy VMware Carbon Black cloud meaning their pricing model remains opaque.
This is the missing silver lining from black cloud, as despite its impressive capabilities, most users would expect to see at least a minimum price by way of a guideline.
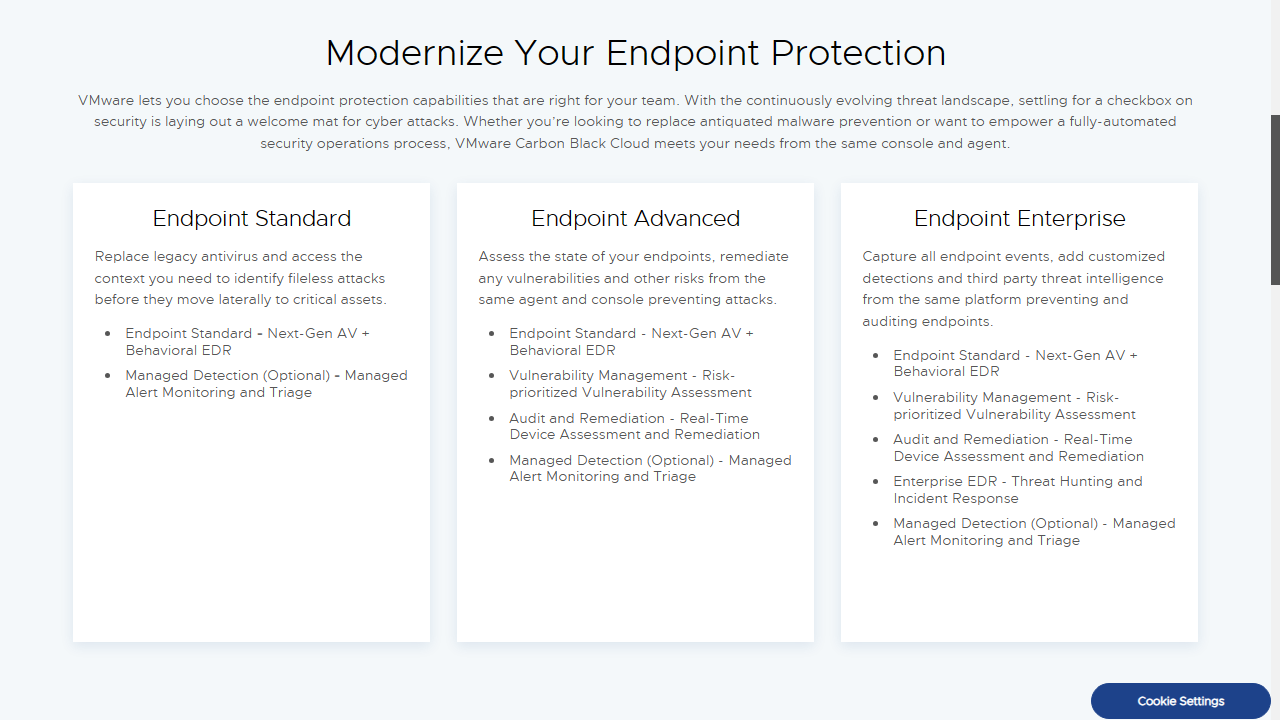
VMware does however list 'Endpoint Protection Bundles', which come in three main tiers.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
'Endpoint Standard' incorporates VMware's 'next-gen' antivirus as well as the platform's Behavioral EDR (Endpoint Detection and Response). There's also an option for managed alert monitoring and triage.
The next level 'Endpoint Advanced' includes all of the above plus risk prioritized vulnerability assessment, as well as real-time device assessment and remediation.
The 'Endpoint Enterprise' tier apparently offers 'Enterprise EDR'. Despite an informative datasheet on this feature, we weren't sure what this offers above and beyond the aforementioned 'Behavioural EDR'. VMware's data sheet for Carbon Black Cloud however does clarify that it supports using threat intelligence and customizable detections.
As always when providers are vague on pricing we encourage readers to contact VMware directly to obtain an exact quote. Although no free trials are offered, VMware offers an excellent "Hands on Lab" where you can try out a simulation of setting up and using Carbon Black Cloud.
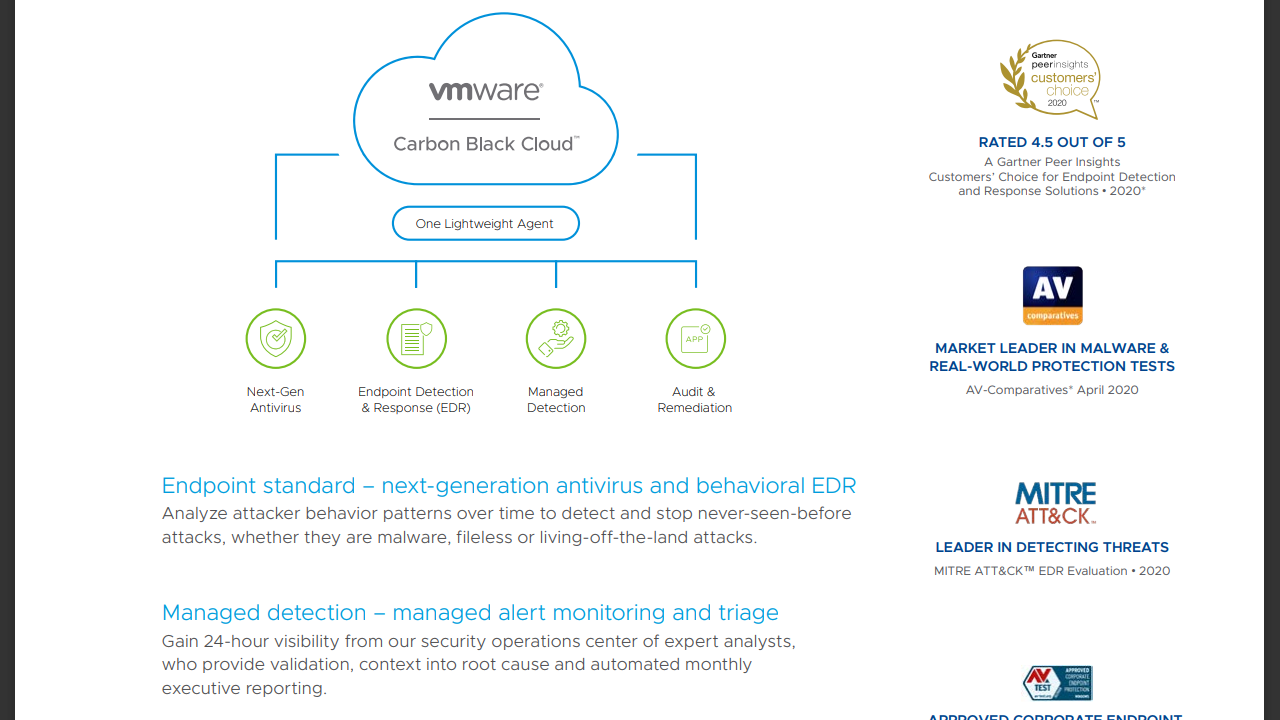
VMware Carbon Black Cloud: Features
VMware's product page drills into more details on how Carbon Black Cloud can keep your infrastructure safe. For instance, the aforementioned 'Next Gen Antivirus and Behavioral EDR' is clarified as being able to "analyze attacker behavior patterns over time to detect and stop never-before-seen attacks, whether they are malware, fileless or living-off-the-land".
This is a bold claim, as LOTL (Living off the Land) attacks are some of the hardest to detect, given that they use an operating system's own tools to launch the attack, so attackers don't have to install any code or scripts.
This protection is available for both Containers and Kubernetes.
The 'Managed Alert Monitoring and Triage' is also clarified as information provided by VMware's own security analysts, who can provide validation and clarification as well as monthly reports.
Carbon Black Cloud also supports "Real-Time Audit and Remediation" - in other words, managers can easily monitor the health of active systems and harden security for workloads as necessary.
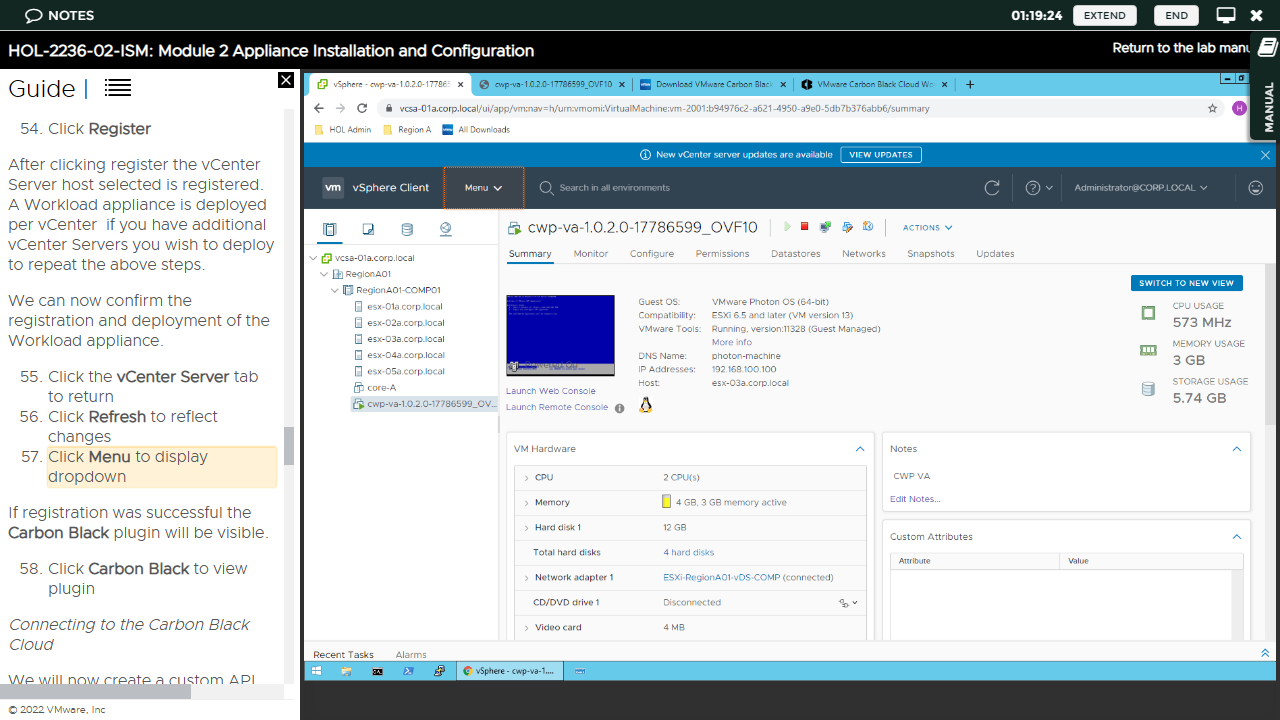
VMware Carbon Black Cloud: Setup
As we mentioned there's no trial version of Carbon Black Cloud but interested parties can sign up for the "Hands on Lab" which uses an interactive tutorial to try out the platform. The simulation covers basic installation, configuration and use.
In order to get started you only need to register a user account and password, after which you can access any of the labs. You can launch the Carbon Black Cloud lab for up to 90 minutes but in practice we found this was plenty of time to become familiar with the platform.
On first launch, users are introduced to the various tiers plus an overview of the Carbon Black Cloud Workload Plug-in, which is designed to provide security for cloud workloads. The lab goes on to explain that the connection between the Carbon Black console and your vCenter Server is managed via a Carbon Black Workload Appliance - this is bundled with the plugin in a single '.ova' (open virtual appliance) file.
This 'Cloud Workload Appliance' is an on-premises based control point, which collects workload inventory data. You can install one appliance for each vServer Center.
To get started users need to download the relevant .ova file from VMware's website, then log in to VMware's vSphere to deploy it via uploading it from their device. This is covered in the online guide.
After uploading, users need to confirm the license agreement and choose the storage type (in this case 'thin provision), before selecting the network that has connectivity to the vCenter Server. The appliance will then begin to import and deploy.
Once this is done, the workload appliance can be powered on to reveal an IP address which users can access via their local browser. This has to be done in order to register it with the vCenter Server. After doing this and signing in, the appliance dashboard will appear. The final step involves configuring SSO (Single Sign On) Registration to create a service account for the appliance to interact with the vCenter SSO server. Users also have to create a custom API to interact with the Carbon Black cloud.
You can repeat these steps for as many vCenter servers as you want to manage, although naturally only one API and secret key can be used per appliance.
VMware Carbon Black Cloud: Interface
Once the "Hands on Lab" has talked users through the setup process, you can start to have more fun via the interactive simulation for the Carbon black plugin. The 'Summary' page gives an excellent overview of CWP (Cloud Workload Protection) via a series of widgets.
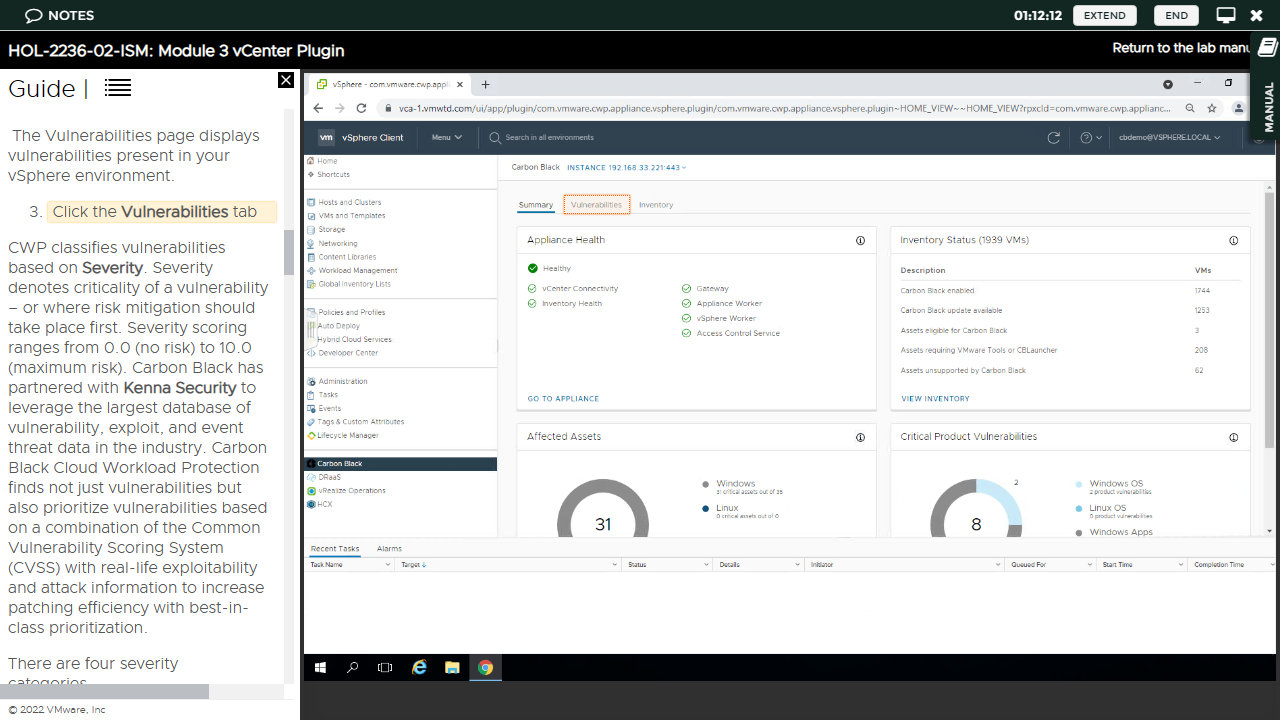
Chief amongst these is the 'Health' section which displays the status of the CWP appliance. The 'Inventory Status' section displays a broad overview for workloads, such as notifying users that Carbon Black is enabled.
The 'Affected Assets' and 'Vulnerabilities' section display how many assets have been compromised in some way, broken down by operating system type.
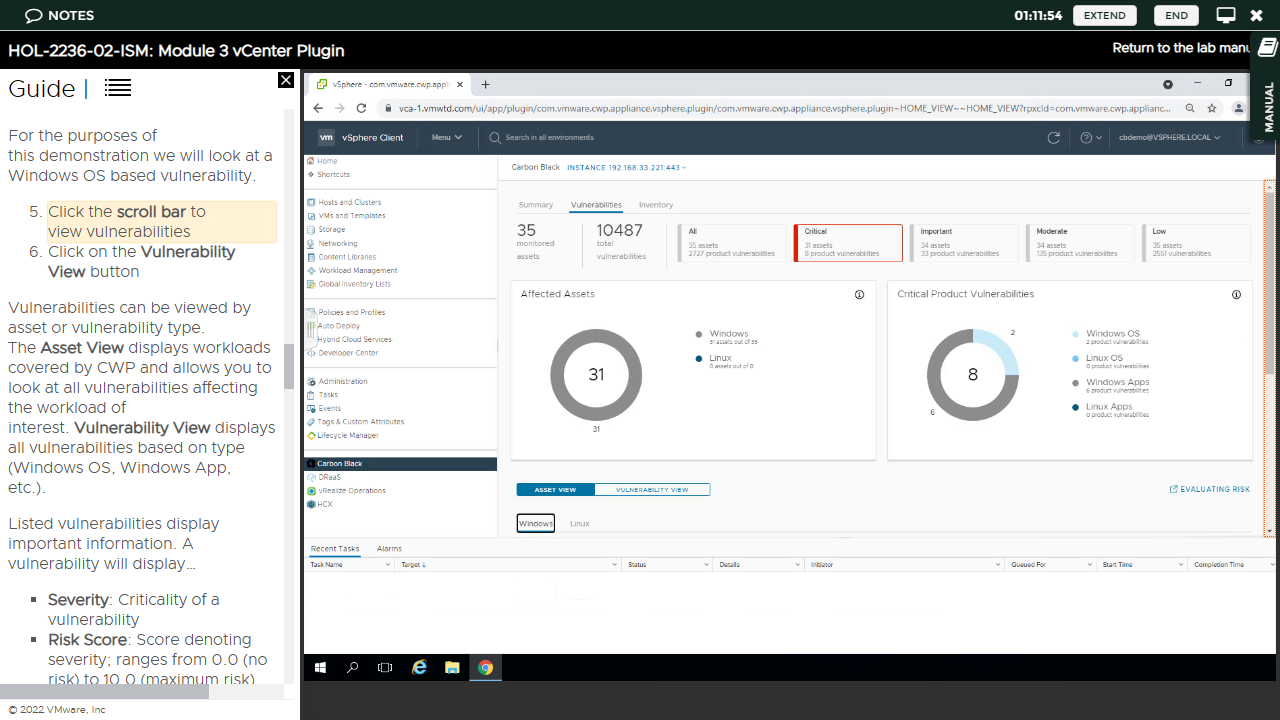
We were especially impressed by the dedicated 'Vulnerabilities' tab, which provides an excellent overview of all discovered threats broken down by type (Critical, Important, Moderate, Low and All).
Specific vulnerabilities also have a specific risk score, which you can view by switching into 'Vulnerability View'. These are well laid out, with a clear indication of key information like the asset name, as well as the OS name and version. You can even click a link to the 'National Vulnerability Database' to view an in-depth description.
The 'Monitor' tab also displays a detailed and easy to follow view of workload vulnerabilities. The 'Inventory' page also provides an easy to read overview of workloads for which you have and have not enabled CWP. (You can move between both lists with a single click).
The importance of a clear and easy to follow interface in this case can't be overstated, as Carbon Black Cloud can potentially be used to manage thousands of endpoints.
VMware certainly deserves bonus points for the fact that it's very easy to see a clear overview of principal assets and vulnerabilities, as well as drill down into specific details with just a few mouse clicks. This is particularly impressive given that some other reviews we found online criticized the interface for being overly complicated, when it's anything but.
VMware Carbon Black Cloud: Performance
When testing endpoint security platforms our usual tests involve attempting to download a fake computer virus using the browser on our test machine, as well as trying to copy a recent, new one we caught in the wild into its 'Downloads' folder to see how the platform reacts.
Given that we could only experience VMware Carbon Black Cloud via a simulation, it wasn't possible to run these tests. However given the platform's advanced threat detection, we're sure it would prove more than a match for simplistic tests like these.
We can comment, however, on the setup process. Frankly without the helpful interactive videos from the online "Lab", anyone but an experienced network security professional would probably struggle to set up and configure the platform correctly. This may be a factor for small organizations who may not have a dedicated in-house network admin capable of navigating the rather involved setup process.
VMware Carbon Black Cloud: Final Verdict
As we've said, the setup pross for VMware Carbon Black Cloud is one of the most involved we'd seen but we're sure its developers would argue this is a reflection of the fact it's designed to manage the security of potentially thousands of devices. Still, this is balanced out by the excellent online lab, which walks interested parties through the process. VMware are also renowned for providing excellent tech support, so
Once set up correctly, there's also no argument that the interface provides an excellent overview of assets, workloads and vulnerabilities without overwhelming users with information.
The only real criticism we can level against the platform is that we'd like to see more details on pricing on the main page. Even if bespoke quotes are necessary for organizations, listing a baseline price could help organizations decide if this endpoint security solution's within their budget.
We've featured the best MDM solutions.
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.