TechRadar Verdict
This is spyware for business, the major limitation of this product is that it only works on the PC (Windows and Linux) and Mac, and therefore has no Chromebook or mobile platform support. It also lacks the polish and sophistication of a modern application.
Pros
- +
Stealthy
Cons
- -
PC, Mac and Linux only
- -
It’s a Trojan
- -
Inadequate security
- -
No legal or ethical advice
Why you can trust TechRadar
Based in the US, iMonitorSoft has offices in the UK, Japan and Hong Kong, demonstrating the global reach of its surveillance products.
According to its website, iMonitor EAM is now on more than half a million PCs in 100+ countries, and customers include Volvo, Siemens and Sony, amongst others.
With so many customers already using this product, is this the one that you might consider using to increase productivity and protect against employee-generated threats?
- Want to try iMonitor EAM? Check out the website here
Features
The first major problem we ran into with iMonitor EAM was that the installation package was flagged at a ‘severe’ threat by the antivirus inbuilt into Windows.
A deeper investigation identified this code as a variant of the Tiggre!plock Trojan, and not something most users would want on their computer.
What’s slightly disconcerting is that the installation for the console also has a Trojan, not just the agent component. Some IT staff will quite reasonably wonder why the console needs this invasive code, and we’re not sure why either.
Once the console and database have been created on the admin computer the agent code can be run on the machine to be tracked, and the IP address of the server machine links the two.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
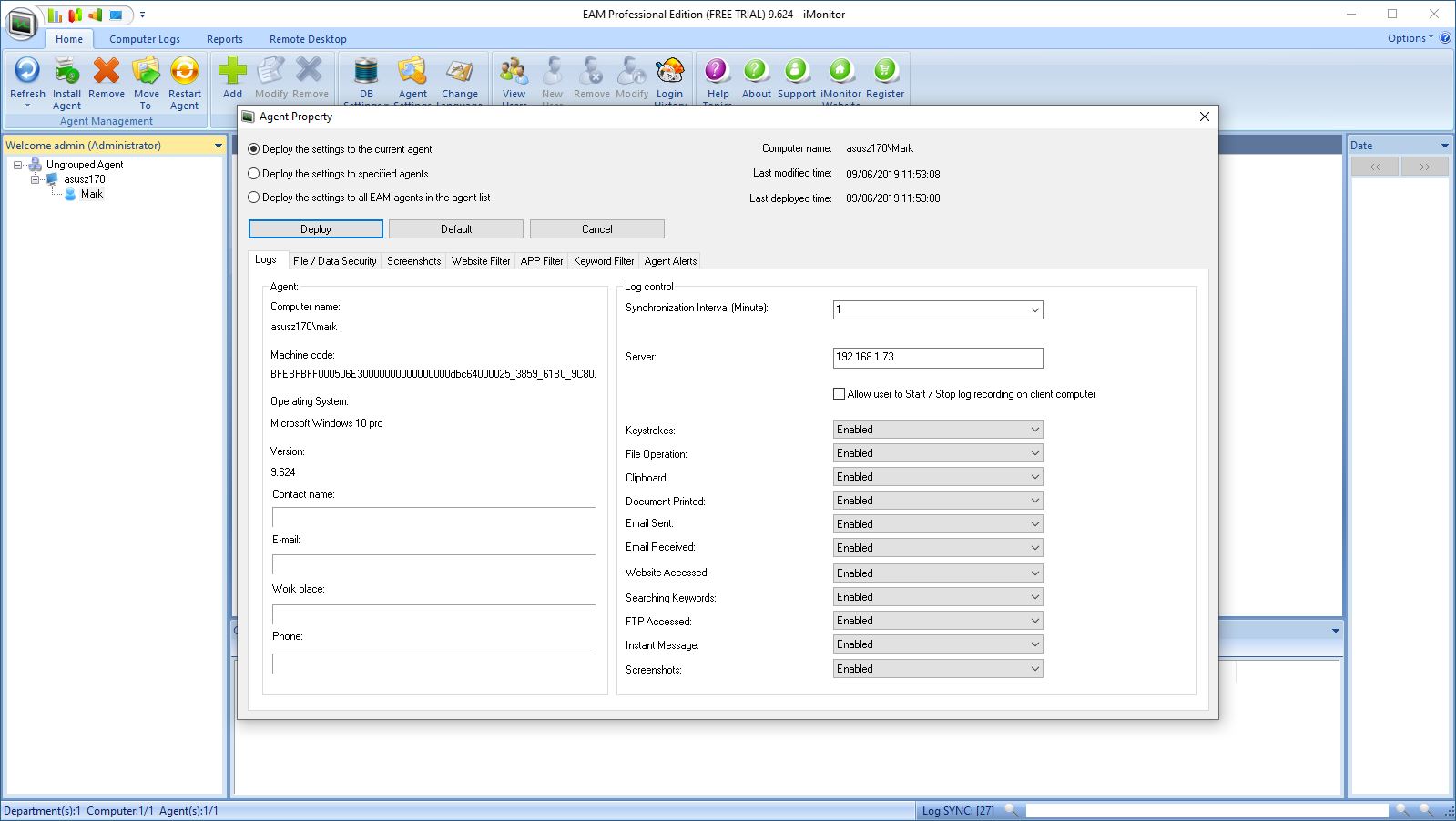
At this point, the agent can be remotely set to capture a wide range of activities that include keystrokes, file operations, clipboard actions, documents printed, email in an out, websites visited and searches, FTP access and instant messages.
There are some limitations to this capture activity, we noted.
For example, in testing we received emails via a Google account and the system accurately logged the title of the email and when it was received. But it isn’t possible to read that email without the Google account password. Having that password and using it without the consent of the account holder would be considered hacking in most regions.
One way around this pitfall is that the system can take screenshots, and these might capture the contents, maybe.
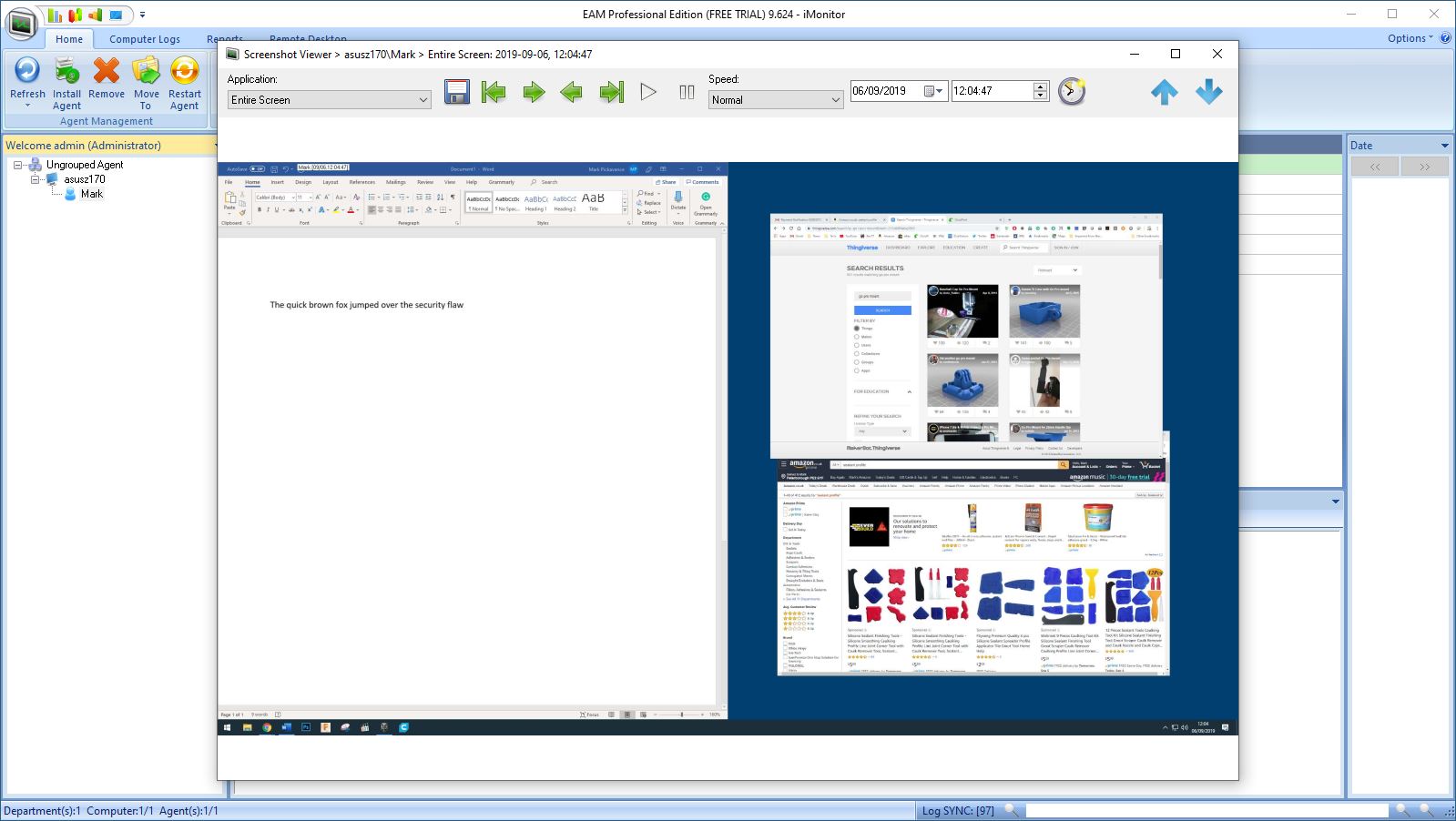
The screen capture feature is probably the best aspect of this system, as it allows a time-compressed playback of all the activity on a machine to be reviewed in a video format.
Another interesting feature that isn’t common on this type of software is the ability to remote desktop to a watched machine from within the console. And, you can send messages to users, lock the screen and even shut down the computer.
These are useful things you might wish to do if an employee is engaged in illegal activity or harassment, and the degree of control here is exceptional.
One rather startling inclusion that many surveillance products have avoided is the ability to access the camera on a PC remotely. There aren’t many countries where this level of intrusion would be considered acceptable, especially if the computer was a laptop and in the home of the employee when the camera is accessed.
Most surveillance software makers have refused to add this feature, even when asked to by government agencies, but iMonitorSoft has included it irrespective of the obvious breaches of privacy it represents.
A limitation that needs outlining is that the agent can only be installed on Windows, Linux or Apple Mac OS X, and therefore Chromebooks and mobile devices aren’t within its scope.
Interface
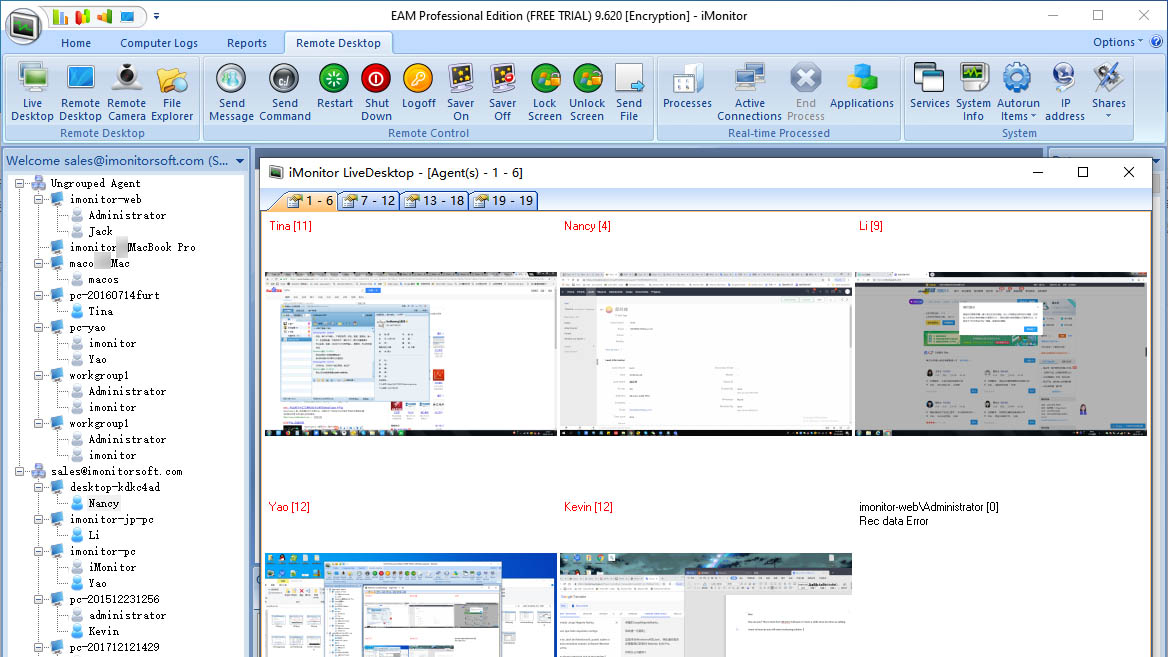
The interface to iMonitor EAM seems to come from a previous era of Windows application design where the toolbar ribbon was in its pomp.
The Computer Logs tab has no fewer than 29 icons across the top, many with dropdowns off them.
We’re not software design experts, but we’ve seen better structural efforts that are easier to navigate.
Our other issue with the interface is that there isn’t any summary for a user or machine to quickly access an overview of the activity.
Digging into a machine and user will provide significant detail about what they’ve been doing, but sometimes this system doesn’t join the dots well.
A good example of this is the key logger that captures whatever happens on the keyboard but fails to detail where these inputs were heading. We typed a line of text into Word, this was captured, but the system offers no context of that event.
It is possible to run reports that give an overview of employees working day, week or month, but the console doesn’t offer these as screen viewable summaries.
Security
One way not to impress a security expert is to give a system a default login of ‘admin’ password of ‘000’, and then not insist the administrator immediately change it.
That’s the approach taken by iMonitor EAM, and it leaves plenty to be desired.
It is possible to change the password, and time limits the access for any console user, but there are no other access control security features, like two-factor authorisation.
The console launcher also remembers the password and login, so anyone with temporary access to the computer it is installed will be able to see all the activities on any agent machines without further hindrance.
But even if the password is changed, all the files the system creates and the database it generates are all entirely unencrypted in a folder on the console machine and can be easily browsed with explorer, notepad and paint.
Given the power inherent in the agent tool, not securing the console or the data it captures in more than a cursory manner is shocking.
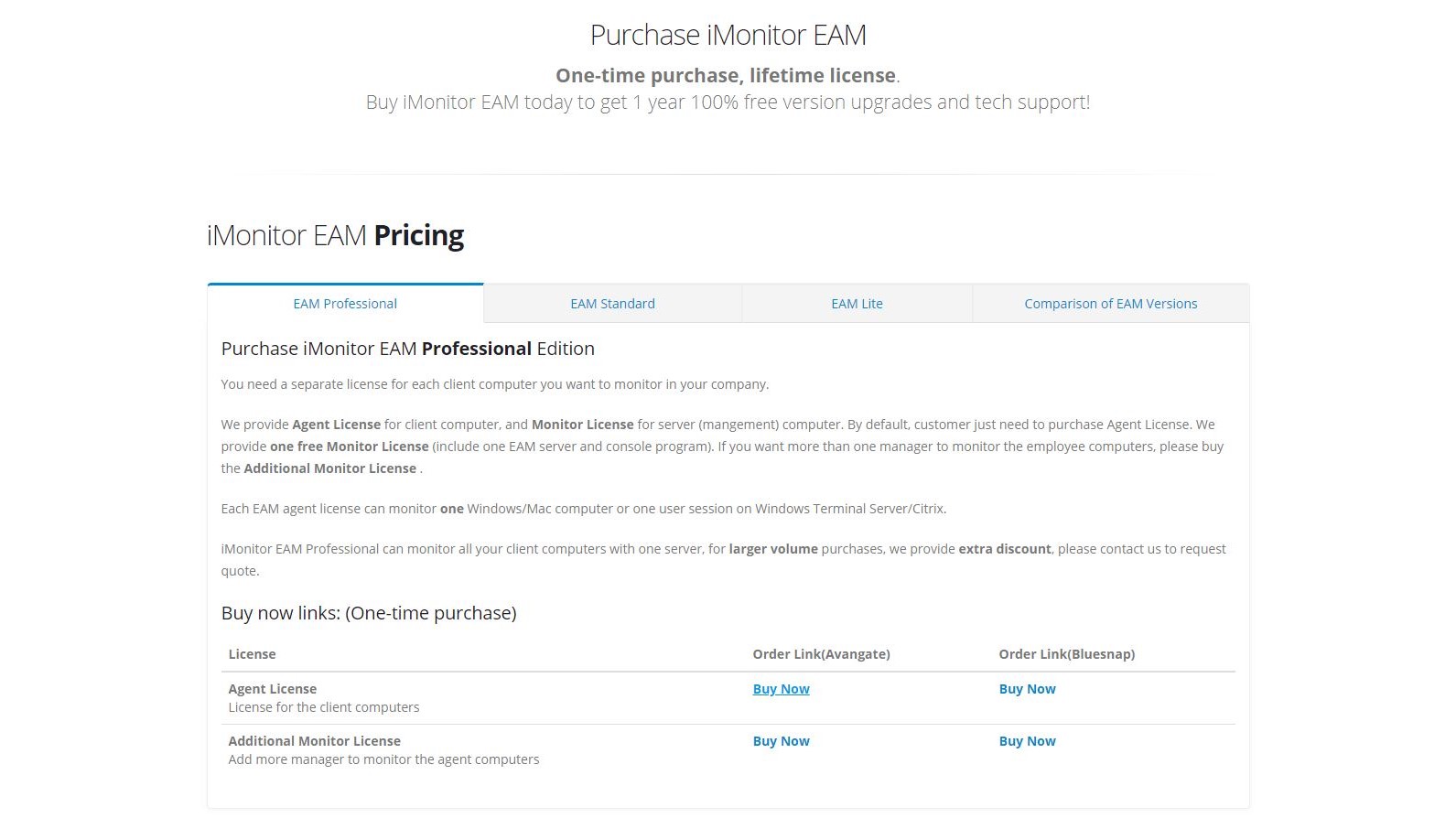
Plans and pricing
The pricing of this product is complicated by the widely different capabilities of each tier, and even limits on the operating systems supported.
Licences are required for both clients and those monitoring them, with different costs attributed to each.
By default, a single monitor license is provided with any purchase of agent licenses (client installs), and you can buy additional monitor installs if you need them.
The license tiers are Lite, Standard, Professional and there is also an Encryption variant that encrypts file transfers in email, on web pages and over IM clients.
Lite, as the name infers, provides the most limited capabilities with no online monitoring mode, and it costs $49.95 (£48.97) per year per client. The minimum number of licenses is three, increasing that cost to $149.85 (£146.92) per year.
Standard licences cost an extra $10 per annum, and Professional cost $79.95, and also provide those in 5 or more units.
If you want the document protection, filtering & blocking modes or some of the other features associated only with the Professional tier, and have an office of 100+ staff, licensing could be a significant yearly expense.
If you want to experience this product for free, a 15-day trial is available to download.
However, iMonitorSoft is one of those surveillance software companies that aren’t hugely interested in the ethics or legality of what happens with its software.
We asked a representative about these things the following boilerplate response was returned;
’In most jurisdictions employee monitoring is legal with no restrictions. However, there may be restrictions on what employee activities you monitor or record. Please consult your legal counsel to ensure you are implementing employee monitoring within the legal and regulatory guidelines applicable to your organization and jurisdiction. iMonitor is fully customizable with respect to its monitoring and recording features to abide by any legal, ethical or regulatory restrictions.’
That first line is a sweeping statement that ignores the reality of employment law in most countries, although we agree wholeheartedly with the part about consulting legal counsel.
Because of the stealth mode functionality, this product is technically spyware, and the legality of that in many locations isn’t cut and dried.
The creators might argue that once licenses are bought and software is deployed, these aren’t things that iMonitorSoft can reasonably be expected to control.
This view might be true, but it is worth remembering that the company who uses the software without the proper controls with be on the end of legal proceedings if it is used illegally or inappropriately on employees.
Final verdict
Overall, this offering is undermined by a software product based on a trojan with a console that’s seen better days and limitations on the platforms that it can monitor.
There are better tools available that don’t need anti-virus to be disarmed to install, and offer better ethical and legal guidance to its customers.
- We've also highlighted the best employee monitoring software.
Mark is an expert on 3D printers, drones and phones. He also covers storage, including SSDs, NAS drives and portable hard drives. He started writing in 1986 and has contributed to MicroMart, PC Format, 3D World, among others.

