TechRadar Verdict
Xcitium Advanced can be very proud of the platform they've created in that it's easy to register and set up, plus client deployment can be done in under a minute. Threat detection isn't quite as proactive as we'd like but this can be improved through using the right device profiles.
Pros
- +
Quick setup
- +
Advanced Security features
- +
Linux client
Cons
- -
Inconsistent threat detection
Why you can trust TechRadar
Xcitium (formerly known as Comodo Security Solutions) has been around for over 25 years. They made headlines in 2010 by openly challenging cybersecurity giant Symantec's claim that paid antivirus programs are better than free antivirus software - Comodo/Xcitium was right and to this day there's not much evidence that paying more gives users significantly better antivirus protection.
Given this company had the courage to go toe to toe with the big names in security software, we were eager to try out their 'Xcitium Advanced' Endpoint Protection platform. The main product page claims that it offers both EPP (Endpoint Protection) and EDR (Endpoint Detection and Response) using a range of advanced detection and prevention features. The platform has even earned the seal of approval of independent review website av-test.org.
This begs the question : has Xcitium created one of the best endpoint security software solutions that could even put the big names in the industry to shame?
Xcitum Advanced: Plans and pricing
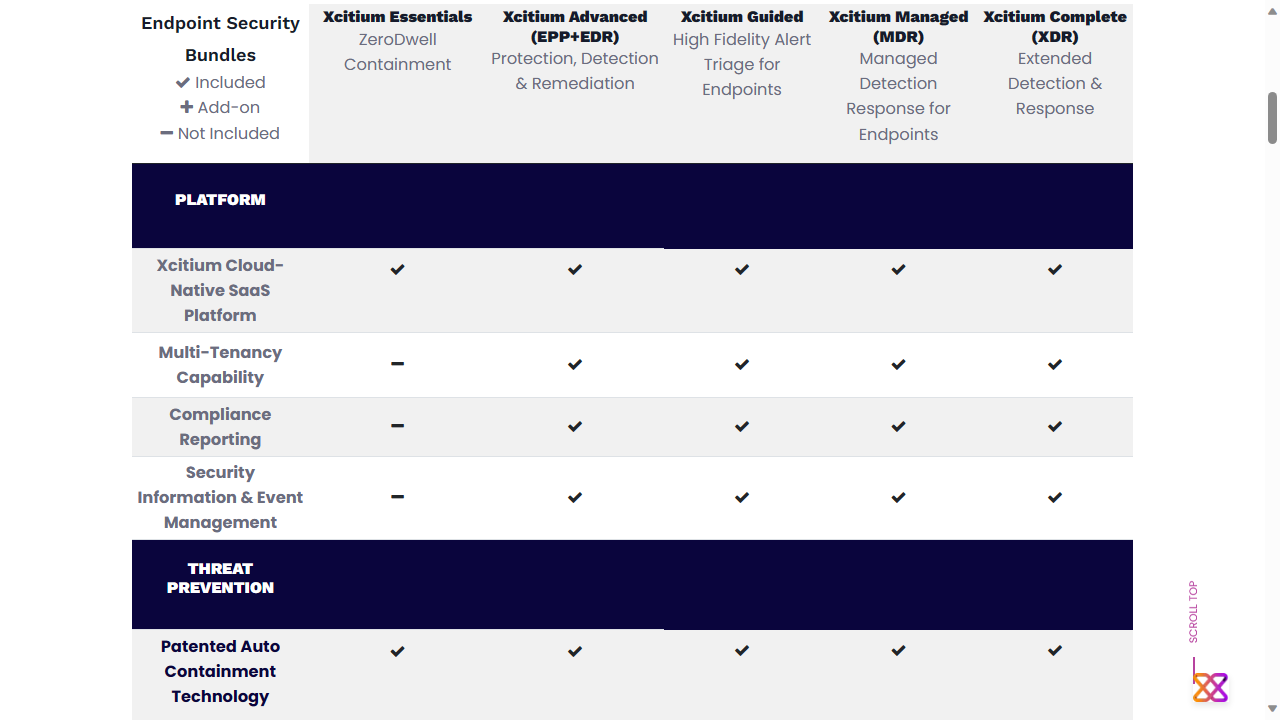
Xcitium offers a range of platform products, including Xcitium Managed for MDR (Managed Detection and Response) and Xcitium Ultimate for XDR (Extended Detection and Response).
Xcitium Advanced itself doesn't appear to offer any staged tiers of service, so subscribers can benefit from all the advertised EPP/EDR features. Unfortunately if you're looking for specific pricing for your organization, you'll need to contact Xcitium's sales department directly as there's no pricing table on the product page.
The company do however, allow you to request a custom demo of the product. Xcitium also has a registration page for interested parties to create a new account in order to request a trial version of products.
Xcitum Advanced: Features
According to the registration e-mails we received the motto of Xcitium Advanced is "Unleash the Power of Zero". In other words, users of the platform can look forward to zero data breaches or other threats.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
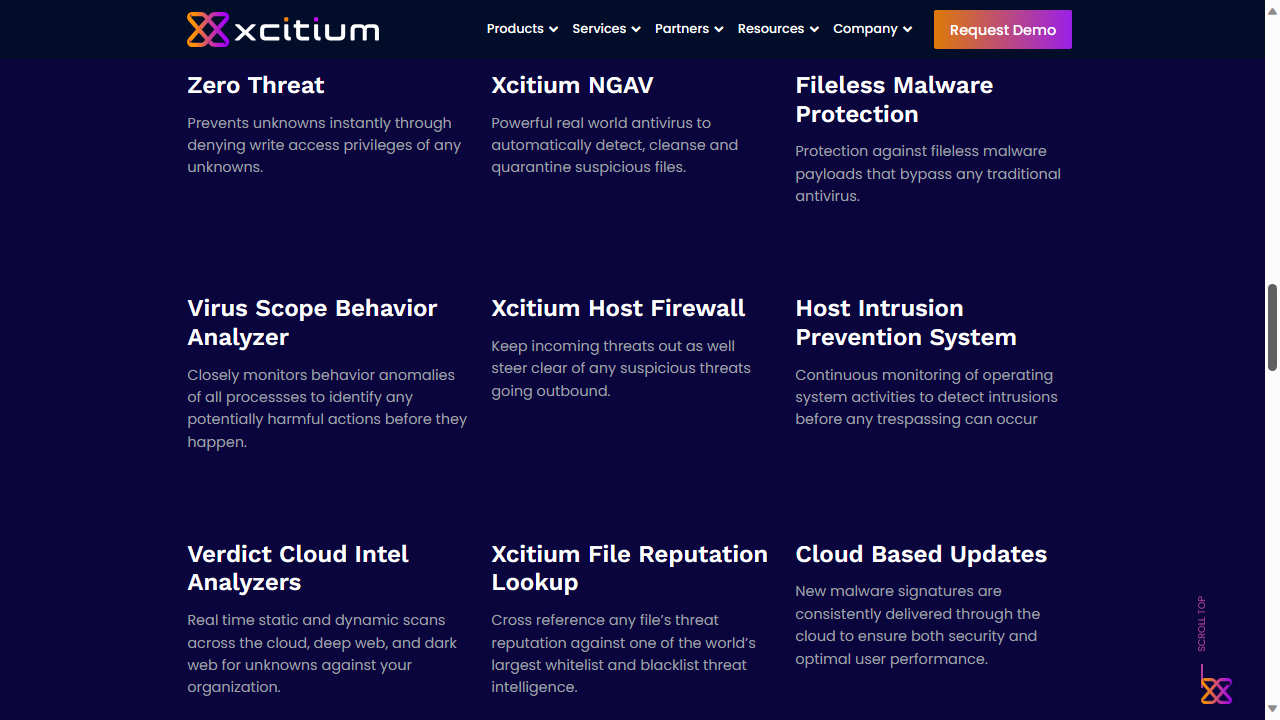
Chief benefits of the platform included advanced endpoint security Anti-Virus (AV), Viruscope (NGAV), endpoint detection and response (EDR), Host Intrusion Prevention System (HIPS), a Firewall (FW), and endpoint management (EM) capabilities.
The company claims their platform is a cut above the rest in threat prevention via 'ZeroDwell Containment'. This is actually a standalone product which forms part of Xcitium Advanced and incorporates a number of features. In the company's own words, these include:
"...Advanced EDR service delivery from the Xcitium Threat Research Labs (XTRL), and the Verdict Cloud engine, a file safety determination service used to assess isolated files and objects to EDR provide a malicious or safe verdict about contained Unknowns."
The aforementioned 'Verdict Cloud Engine' deserves special mention, as it purportedly publishes results published globally in real-time for all Xcitium Advanced EDR customers to reduce threats across the board.
The product's data sheet also provides an excellent summary of Xcitium Advanced features, including fileless malware detection, which can prevent threats found in areas like RAM instead of data files.
The platform also has a highly-configurable alerts policy (we were very pleased to see the option to receive email alerts during our tests). These include notifications about the aforementioned fileless attacks, advanced persistent threats (APTs), and privilege escalation attempts.
Special mention should also go to the 'Virtual Desktop' feature for those users who install the 'Security' add-on for the endpoint agent (see below). Naturally this provides an excellent way to view and work with files with minimal risk to the host operating system.
Xcitum Advanced: Setup
The good people of Xcitium were kind enough to provide TechRadar with a trial version of Xcitium Advanced, which we were able to access through a simple sign up portal.
We were very impressed to see that immediately after creating an account the platform encourages users to set up 2FA (two-factor authentication) and even recommends suitable authenticator apps.
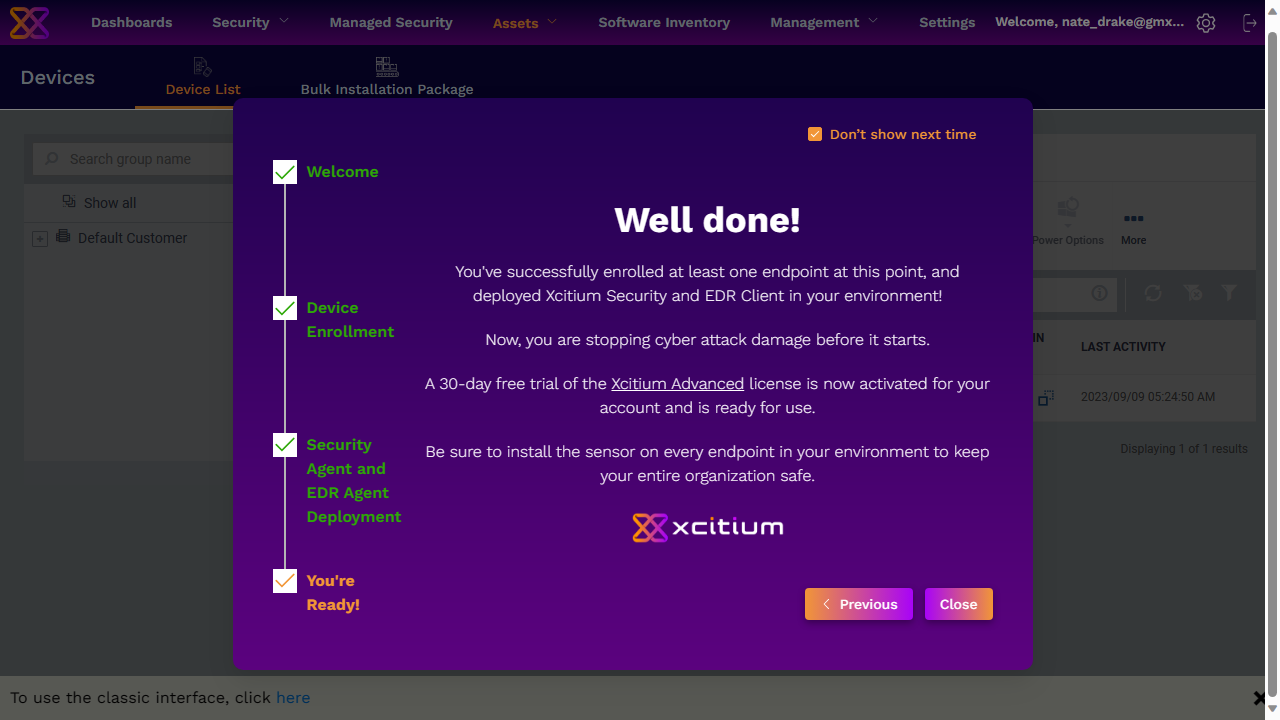
Users are then asked to create their own subdomain, which is used to access the Xcitium cloud console. On first launch the console displays a helpful wizard, which provides a download link for agent software. Xcitium Advanced supports endpoints for Windows, Mac and Linux. We were astonished how quickly the helpful wizard installed the agent on our test machine, as we had it up and running in less than 30 seconds.
Once this is installed, the wizard also encourages you to install additional packages to provide better security & EDR protection.
Xcitum Advanced: Interface
Our first experience of the Xcitium Advanced interface proper was when we were invited to install the additional Security and EDR packages, via the 'Device List'. We were especially impressed to see the main options for endpoints such as 'File Transfer'.
You can also click on device names to view more detailed information about endpoints, though the device list also contains a handy summary of highlighted icons to show which features are enabled e.g. AV = antivirus.
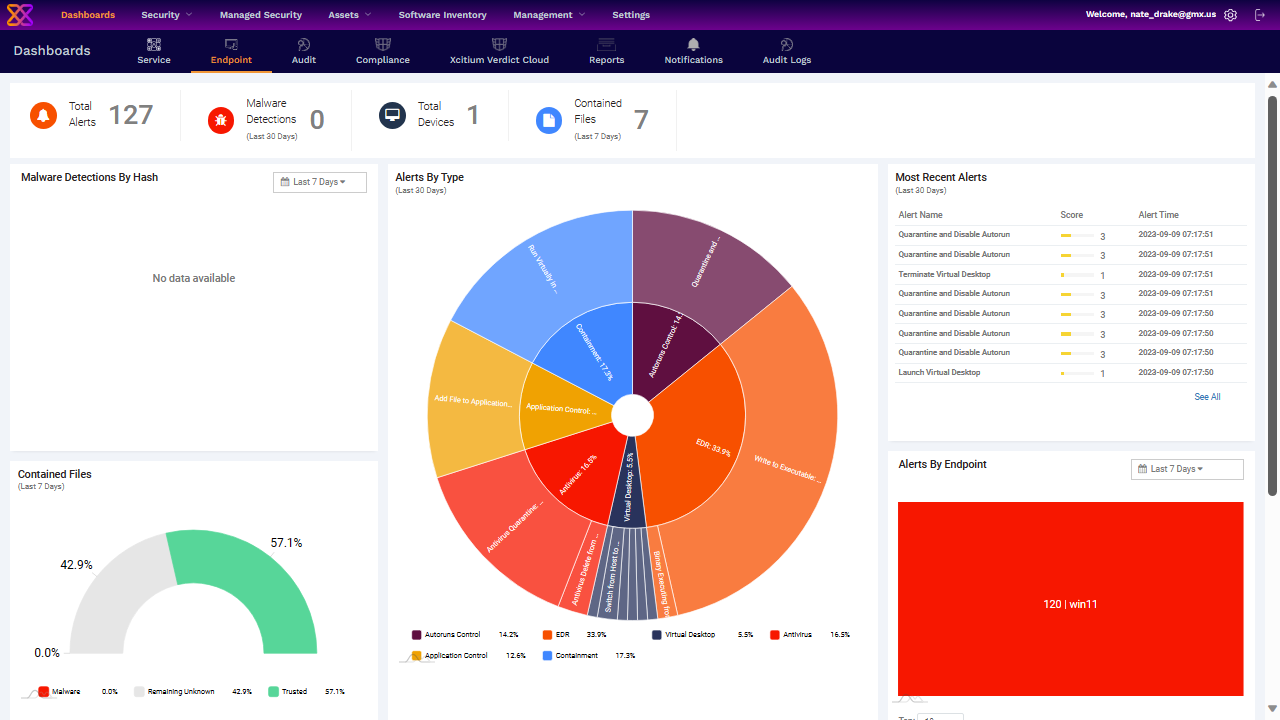
As TechRadar readers know, we believe the most important aspect of any UI is the main dashboard and we weren't disappointed by Xcitium Advanced's main screen. In fact, the platform has a number of endpoints for various features like services, auditing and endpoints themselves.
We were delighted to see that the endpoint dashboard displays alerts at the very top of the screen and even provides a helpful pie chart breaking down alerts by category. Other infographics display helpful information on contained files and detections per endpoint.
Special mention should also go to the 'Software Inventory', the 'Global' section of which lists all installed programs on endpoints. Users can quickly click to select apps and then to uninstall or export details in CSV format.
Our only small criticism here is that the 'Notifications' area only contained information relevant to the installation of Xcitium itself - we had to look elsewhere to find details of actual alerts. In fairness, users can view more details about these by clicking into alert notifications via the dashboard.
Xcitum Advanced: Performance
When reviewing endpoint security platforms our first test is always to attempt to download a fake computer virus, provided by the good people of EICAR.
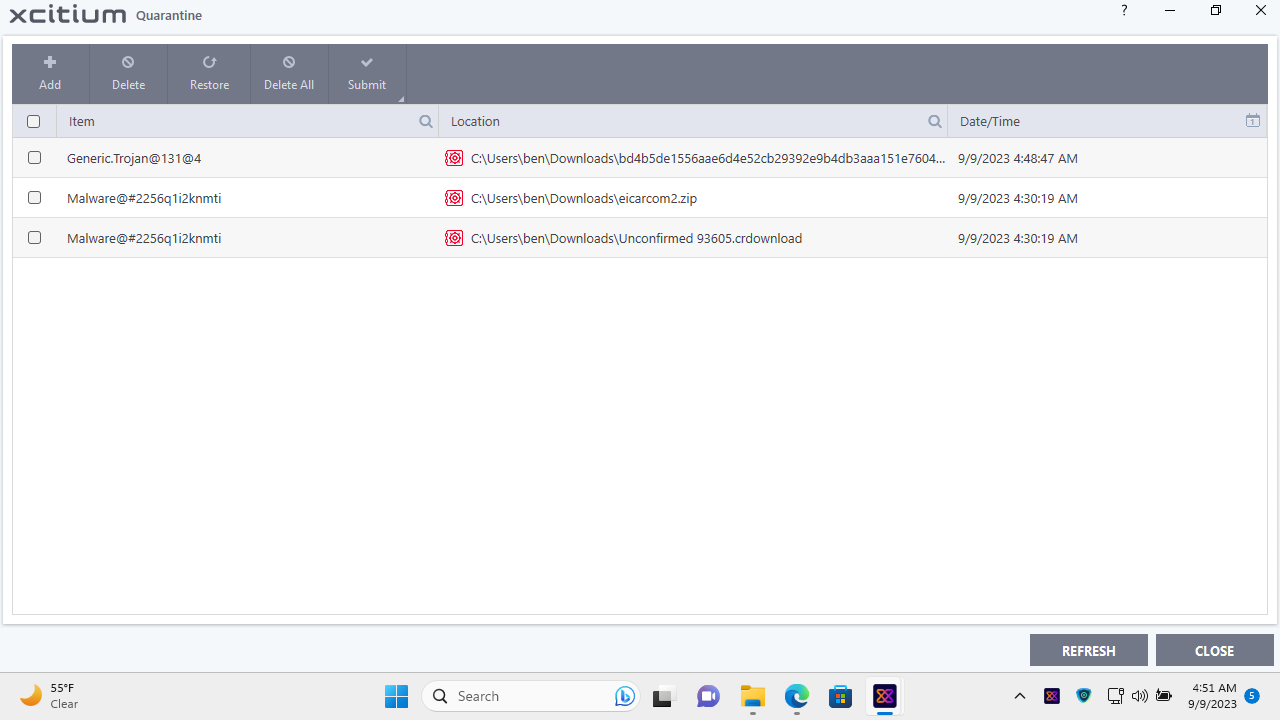
We checked that the Antivirus and security features were enabled on our endpoint before visiting the website containing the malware. Each time we tried to download the file in compressed (ZIP) format, we found that the Xcitium agent had altered the file permissions so that the test virus couldn't be saved to the 'Downloads' folder.
The agent didn't show any notification of this but when we opened the cloud console, we saw the file had been quarantined and an alert was generated.
Our next test was to try to copy a recent, real computer virus we'd caught in the wild onto the test machine's "Downloads" folder. We do this to check that an endpoint security platform can detect and prevent threats based on a program's behaviour, not just by comparing file signatures to an online database.
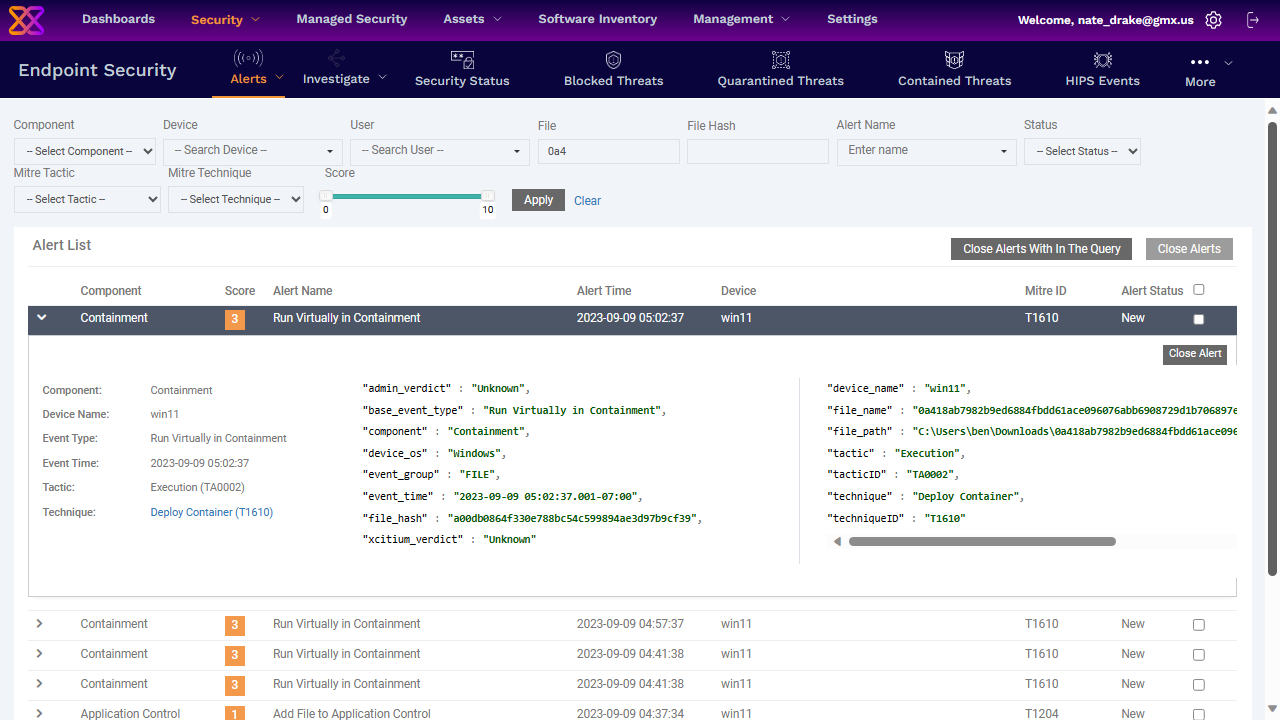
Xcitium Advanced didn't fare as well with these tests. We were able to copy the malware (a trojan virus) to the 'Downloads' folder without triggering any alerts from the platform. We decided to right-click the file to run a scan with Xcitium antivirus but no threat was found. The agent also offers the option to run the file in an Xcitium container. We did this but the cloud console log seemingly showed the file as safe.
We were troubled by this, so returned to the console to check the device policies. We enabled the 'Comodo Containment' profile, then ran the tests again with a new, real computer virus. This time the agent did detect and quarantine it, as shown by the cloud console logs.
This is strong proof that Xcitium Advanced can detect and prevent threats based on file behavior, though it's clear the security settings may need some tweaking to gain the full benefits of protection as we were able to run the original real trojan virus and infect our test machine without the agent detecting any issues.
Xcitum Advanced: Final verdict
Overall, there's much we enjoyed about Xcitium Advanced. We don't take for granted the easy registration and setup, as some platforms will only provide demos rather than let you try the software for yourself. We were especially thrilled that the agent software only took seconds to deploy.
The cloud console is well laid out and the multiple dashboards allow users to chop and change data in any way they see fit. It's a shame we couldn't find more readily available information on pricing but in fairness Xcitium Advanced's sales team is only a phone call away.
When it comes to preventing downloads of potentially dangerous files, this platform passed our tests with flying colors both with the fake computer virus and one which we attempted to download from a known malware website.
As readers have seen, the results were more hit and miss when we tested with real computer viruses that had been manually copied onto our test machine. At the suggestion of Xcitium staff we changed the device profile to 'Windows - Secure', which uses the platform's containment technology but with the same results as before.
As Meatloaf taught us, "Two out of three" ain't bad and it's entirely possible that the trojan we originally used wasn't detected due to incorrect configuration or a temporary error. Still, it's the same virus we used in tests of other endpoint security platforms and is almost always detected and quarantined.
If you're considering this platform, we suggest you work closely with Xcitium to make sure your threat database is up to date and your agent is using the correct security profile.
We've listed the best antivirus software
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.