Ghost in a car shell: Engineers make self-driving vehicles 'hallucinate' at will — MadRadar is worrying proof-of-concept that should get automotive companies on alert
It can make cars 'see' vehicles that aren't there, or hide ones that are
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
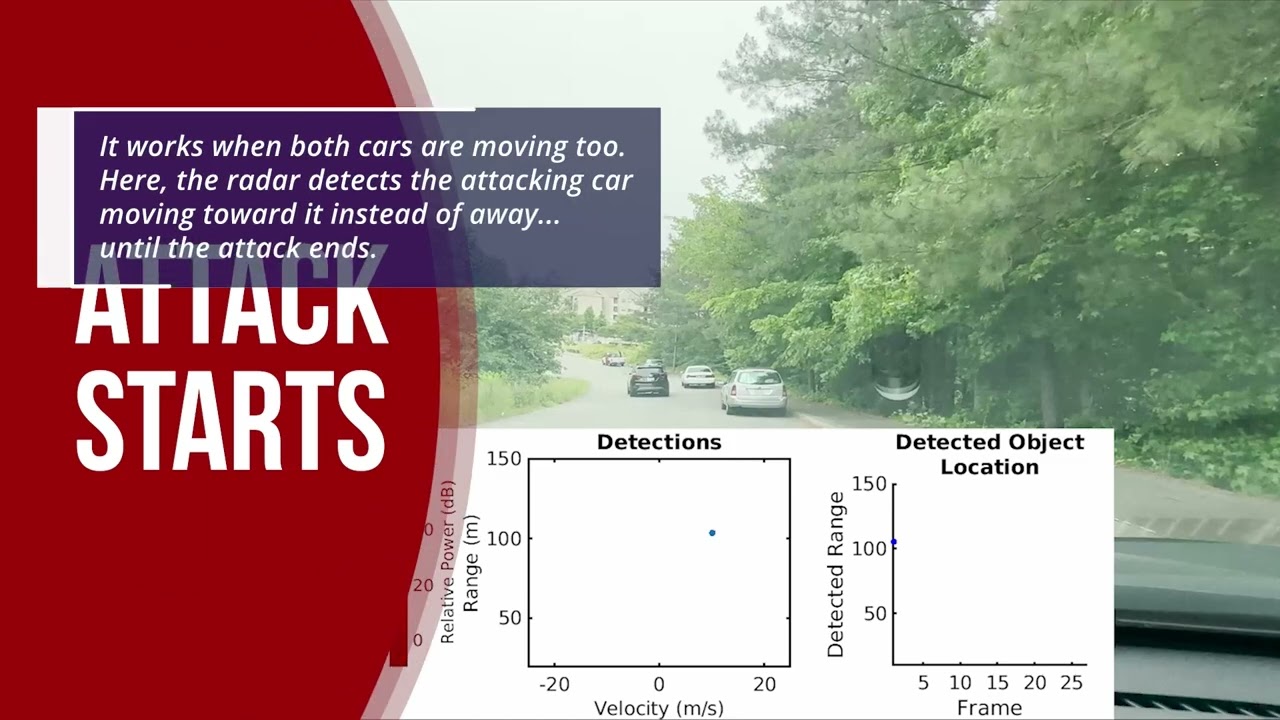
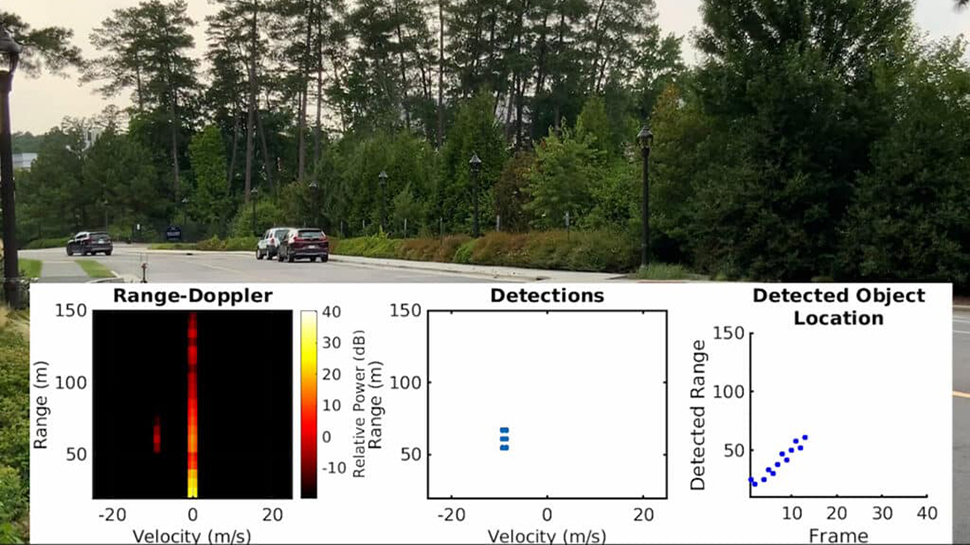
Engineers at Duke University, Durham, North Carolina, have developed a system capable of manipulating automotive radar sensors, and making vehicles ‘hallucinate’ a range of scenarios. These include hiding the approach of an oncoming vehicle, making it look as if a real car has suddenly changed direction, or creating a non-existent phantom car.
Named MadRadar, this system performs tasks quickly and doesn’t require prior knowledge of the specific radar settings of the targeted vehicle.
"We can make a fake vehicle appear out of nowhere or make an actual vehicle disappear in real-world experiments," Miroslav Pajic, the Dickinson Family Associate Professor of Electrical and Computer Engineering and lead of the team behind MadRadar said in a statement.
Real-world case studies
Radar is crucial for modern vehicles equipped with assistive and autonomous driving technologies to detect nearby moving vehicles. The variety of makes and models on the road means vehicles have slightly different operating parameters, traditionally making radar spoofing tricky.
However, MadRadar overcomes this hurdle by identifying a vehicle's radar parameters within a quarter of a second and then initiating its own radar signals to deceive the targeted radar system.
Described as a 'general black-box radar attack framework for automotive mmWave FMCW radars', MadRadar can estimate the victim radar's configuration in real-time and then execute an attack based on the estimates.
The research states, “We evaluate the impact of such attacks maliciously manipulating a victim radar's point cloud, and show the novel ability to effectively `add' (i.e., false positive attacks), `remove' (i.e., false negative attacks), or `move' (i.e., translation attacks) object detections from a victim vehicle's scene. Finally, we experimentally demonstrate the feasibility of our attacks on real-world case studies performed using a real-time physical prototype on a software-defined radio platform."
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The researchers plan to detail their work at the Network and Distributed System Security Symposium 2024, in San Diego, California. The paper is currently available on the arXiv preprint server.
The researchers emphasize that the existence of MadRadar underscores the urgent need for manufacturers to enhance the security measures of their radar systems to protect against potential misuse.
"We’re not building these systems to hurt anyone, we’re demonstrating the existing problems with current radar systems to show that we need to fundamentally change how we design them," Pajic concluded.
More from TechRadar Pro

Wayne Williams is a freelancer writing news for TechRadar Pro. He has been writing about computers, technology, and the web for 30 years. In that time he wrote for most of the UK’s PC magazines, and launched, edited and published a number of them too.