Bring your own security: protecting business data on every device
Developing security protocols for BYOD and WYOD
Does your business allow its employees to use their own phones and tablets at work? The so-called BYOD (Bring Your Own Device) and now WYOD (Wear Your Own Device) trend has continued to expand, as employees use their personal devices for work and play. In 2018, 50% of North American businesses have BYOD policies, and 69% of IT decision-makers are pro BYOD.
What this has meant for business owners is a revisiting of their security policies, and the protocols in use to ensure these devices, and the information they contain, are always secure. This is vital, as Kaspersky Labs has already identified one million pieces of mobile malware that can compromise smartphones.
Gartner comments: "BYOD does increase risks and changes expectations for CIOs (Chief Information Officers). Unsurprisingly, security is the top concern for BYOD. The risk of data leakage on mobile platforms is particularly acute.
"Some mobile devices are designed to share data in the cloud and have no general purpose file system for applications to share, increasing the potential for data to be easily duplicated between applications and moved between applications and the cloud."
There are a number of issues to be considered when managing the security of BYOD across your organization, including:
1. Having no policy regarding the downloading and installation of apps
There are now millions of apps to choose from. Having no policy regarding which apps can and can't be installed opens any device to potential attacks from malware, such as a banking Trojan that hid as a Super Mario app. Create a blacklist of apps that employees should never install on their phones.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
2. Privacy versus monitoring
The ability of every mobile device to be tracked can raise privacy issues where BYOD is concerned. Few employees will wish their location to be tracked and monitored when not at work. However, businesses need to know where each device is, with geofencing setting parameters that state a device will only be monitored during office hours.
3. Monitor business usage
As a device could be used for personal and business calls and data exchange, it's important to track usage to ensure costs to the business are allocated correctly. This includes when the devices are used overseas to avoid excessive roaming charges.
4. Choice of device
The whole philosophy behind BYOD is that workers can choose their own device to use. However, security policy must dictate that this can't include jail-broken phones, for instance, or any other device that has not been authorized. Your security policy should include a list of devices that are approved, a variant on the BYOD policy known as CYOD – Choose Your Own Device.
5. Information is security
A security policy that isn't clearly communicated is of little use, so train your staff to ensure they're aware of their responsibilities under your BYOD security policy. And this isn't a set up and forget exercise; monitor how BYOD develops across your business, and modify your security policy accordingly.
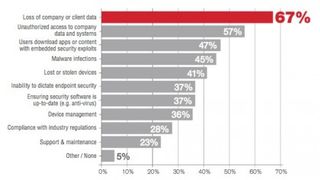
In its BYOD security report [PDF], EY advises: "The risk of the device itself should be assessed as a part of the company's risk assessment framework. In some organizations a tiered device architecture may be viable to deal with varying degrees of risks tied to job functions.
"For instance, devices that are being used to present sensitive financial data to the board through a custom app will invariably be more sensitive to theft or accidental loss than a mobile device with access to calendar and email updates."
Intelligent defence
With businesses entering a possible post-PC era, ensuring that every device used by your employees has adequate levels of security is vital. What's more, as workforces continue to become more mobile and geographically dispersed, the use of mobile devices will expand; they'll account for 73% of Internet consumption in 2018.
Security policies must take account of this expansion, yet enable workers to use the same device in their private lives, as well as at work.
IT managers and CIOs need to look at how their existing security policies can be amended to maintain high levels of data security with BYOD. A policy can be modified in several ways:
- A virtual desktop infrastructure (VDI) can be used to allow BYOD devices to securely access business servers without any cross-pollination of data that could include malicious code.
- Decisions should be made on the level of access that devices will have to a corporate network. Businesses want to allow BYOD, but limits should be set and communicated to users.
- The storage of sensitive data on personal devices can be allowed, but within limits set after consultation across users to strike a balance between day-to-day needs for data access, and the overall business security policy that includes compliance with data-protection regulations.
- Mobile device management (MDM) may at first glance seem to be the solution to security issues, but IT managers and CIOs should look closely at how MDM can be used to control a device environment that includes BYOD.
- It's important to maintain endpoint security within a BYOD environment. Remote wiping of data, and on-board antivirus protection, become essential, as it's easy for an infection to spread from a user's home network.
- Using a private cloud environment to protect BYOD users and provide a single management console for IT managers should also be considered.
Pulse Secure further notes: "Where organizations have attempted to embrace BYOD with MDM suites or capabilities, they are often met with resistance from users concerned that their personal devices are falling under the control of their enterprise admins.
"[We] should expect to see a shift from enterprises trying to manage and secure an entire mobile device via MDM to one of employing workspaces to secure only portions of the device that access and store corporate data.
"This shift will be an attempt to reduce tensions between enterprise admins and the personal device owners over who owns what data and what ability the enterprise has to secure data and lock and wipe devices at their discretion."
Risks and rewards
To gain an insight into the current state of BYOD security, TechRadar pro spoke with Garry Sidaway, SVP Security Strategy and Alliances at NTT Security, on a number of issues including the core security risks facing businesses and the advantages (or disadvantages) of wearables.

TechRadar pro: Are businesses paying enough attention to the security risks that BYOD/WYOD present to their organizations?
Garry Sidaway: Most companies have put in place controls and processes to manage BYOD, in particular mobile devices like phones and tablets, but wearables and connected devices aren't typically considered in an organization's risk management strategy.
As more and more devices are connected, the security implications are massive. As always, understanding the real risk and putting risk in context is essential.
TRP: What are the core security risks that BYOD/WYOD present to businesses?
GS: The risks associated with BYOD/WYOD are the potential ingress and egress of information. Monitoring the current logs with the existing connected devices and security technologies is already becoming a huge challenge to businesses but, when you start to include unusual devices such as watches and TVs, the volume of data and false alerts could potentially be overwhelming.
This is before you even consider the skills required to regularly monitor and analyze such data.
TRP: Can businesses take any practical steps to minimise the security exposure that wearable devices present to their companies?
GS: Putting the risk in context is essential, and also to put in place the necessary policies which should be an extension of plans already in place for BYOD. These should then be enforced with network and access control systems, extending protection to wearable devices which will typically be connected over Bluetooth or wireless.
Finally, look towards analysing logs effectively and efficiently which can be achieved through working with a Managed Security Services Provider (MSSP) who covers such devices.
TRP: Is there a fine balance to be struck with the advantages that wearable devices bring to businesses and their employees, and the organization's need to protect sensitive information?
GS: As always with advances in personal innovation and business, there is a fine balance. Where the initial reaction to BYOD was negative from the security department, we have seen that businesses can benefit once wearables have been analyzed and the risks understood.
TRP: What do you think wearable device security looks like?
GS: Wearable devices will typically connect through wireless connections and as such can be managed through traditional network access controls. The focus should also be placed on effectively managing the increase in log traffic.
Most of these devices will not be looked upon as a security risk but they can (and will) be exploited as any other connected device. TVs with microphones, personal monitoring and privacy, cars and fridges with no protection, are all potential entry points in an organization's infrastructure.
But ensuring that these risks are put in context and understood before simply banning them is essential, as businesses can enable innovation and personal efficiency.
Conclusion
There's little doubt that BYOD/WYOD will continue to impact on every business. As more sensitive information moves to consumer devices, your business needs a robust and flexible security policy to ensure data, networks and the transmission of this sensitive information is safe and secure.
Most Popular


