TechRadar Verdict
Traditional VPNs are outdated, and Twingate offers a more secure and efficient solution for remote access to corporate resources. It offers a modern Zero Trust Network Access solution package as a secure and efficient alternative to traditional VPNs, focusing on ease of use, scalability, and robust overall security for remote access. Twingate simplifies the deployment of connectors for remote client access, offering redundancy and load balancing, with the ability to deploy on various platforms, starting with an Ubuntu Linux VM. With its flexible access policy configurations and comprehensive activity logging, Twingate is ideal for businesses in regulated industries like legal, finance, and healthcare. Despite its advanced security features, the platform offers a simple, intuitive interface that allows quick deployment without requiring specialized technical expertise. This balance between detailed control and user-friendly design makes it a great option for companies that need to manage secure access while complying with strict industry regulations.
Pros
- +
Simple deployment
- +
Zero-trust security
- +
Robust user management
Cons
- -
Slightly more complex setup for first-time users
- -
Free plan limited to small teams
Why you can trust TechRadar
Features
Built on a zero-trust architecture, it ensures secure access by requiring authentication at each step, minimizing the attack surface. The platform is cloud-native, making it highly scalable and adaptable to modern business needs, which means it's not just a VPN client but a comprehensive security package aimed at businesses and organizations.
Twingate supports device authentication and integrates with single sign-on (SSO) providers like Okta and Azure AD, which simplifies identity management across distributed teams. Besides this, Twingate offers a range of integrations with mobile device management and endpoint protection vendors. You can find the list of their extensive integrations on their site.
Unlike traditional VPNs that rely on a single point of failure, Twingate separates identity, control, and data planes, ensuring higher resilience and security. All user connections are encrypted end-to-end, while user access is granted (or denied) in real-time based on contextual information such as user identity, device security status, time of login, and the user's or device's geolocation. This data is used in conjunction with admin-defined access policies to ensure secure and tailored access control policies.
Speaking of defining policies, all of this is done through the admin console, which is intuitive and features a modern UI. From this web-based management console, admins can get granular, viewing reports and resource usage, and add or remove users. The granularity extends to configuration on a per-use, per-device, and per-resource basis. This allows administrators to enforce strict access controls by applying the principle of least privilege, reducing the risk of unauthorized account access. It also ensures compliance with regulations that mandate higher levels of security for sensitive or privileged accounts.
Twingate tracks all network activity, logging each user's access attempts and providing detailed insights into which resources were targeted. For reporting and logging purposes you can also integrate with logging platforms like DataDog, Elastic, and Splunk for enhanced reporting capabilities. Yet, the platform itself has enough capability for reporting without a need for integrations, unless you have specific needs and requirements.
Pricing & Plans
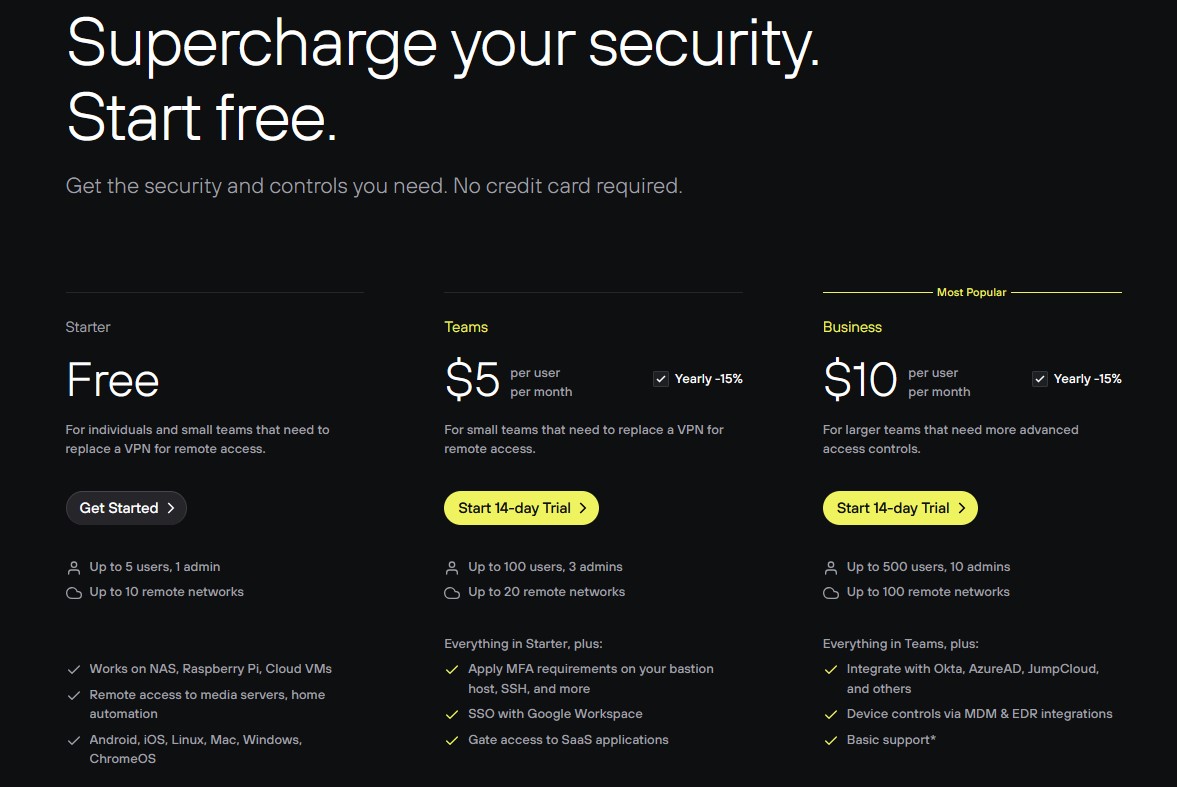
Twingate offers flexible pricing plans with the entry-level Starter plan costing nothing and allowing up to 5 users and 10 remote networks, making it ideal for small teams or those wanting to explore the platform without a financial commitment. For growing teams, the Teams plan is priced at $5 per user per month, supporting up to 100 users and 20 networks, along with a 14-day free trial and a money-back guarantee.
For larger organizations, the Business plan is priced at $10 per user per month, offering support for up to 500 users and 100 networks. It includes more advanced features such as enhanced integrations and management options, making it suitable for companies with more complex security needs. This plan also ensures scalability, with options to expand as the organization grows.
Finally, the Enterprise plan offers tailored pricing and features based on specific business requirements. Companies interested in this plan will need to contact Twingate’s sales team to create a customized package. The Enterprise plan is designed for businesses with extensive remote access needs, offering the highest level of flexibility, support, and integration capabilities.
Note that if you opt to try out Twingate via the free plan, you will be limited in terms of integrations and DNS capabilities, but all of this is covered in paid plans.
Performance
Due to its design, Twingate offers faster average speeds compared to traditional business VPNs. The maximum and minimum speeds users experience primarily depend on their internet connection. Factors influencing performance include the type of traffic generated, with Twingate using split tunneling to route only business-related data through its network, encryption protocols, and overall network conditions. This ensures efficient data flow and minimizes latency for business activities.
Furthermore, the cloud-based admin console worked to perfection during our test, without any hiccups. We did not experience any slowdowns or crashes.
Privacy & Security
Twingate uses AES-256 encryption and SSL/TLS protocols to secure data transmissions, safeguarding business information from cyber threats. Additionally, it integrates multi-factor authentication (MFA) and single sign-on (SSO) capabilities. The aforementioned split tunneling feature routes business traffic through encrypted “tunnels” while keeping non-essential data flowing through the VPN. Moreover, the fact that Twingate utilizes the Zero Trust approach, means that strict verification protocols require verification of every user and device before granting access, ensuring that only verified entities can interact with sensitive resources.
What’s more, it enables companies to implement the necessary security controls to comply with various regulatory standards such as CPRA, GDPR, PCI DSS, and SOC 2.
Support
Twingate provides support through a ticketing system, messaging, and email. While assistance might not always be immediately available, their comprehensive guides and FAQs are particularly useful for addressing common issues. These resources offer detailed instructions, making it easier to troubleshoot independently. Overall, the written materials and support options can be helpful, but availability may vary depending on your needs and the timing of your request for assistance.
Alternatives
An equally attractive offering can be found with NordLayer Business VPN, which also offers a complete security package, complex security protocols, and a ZTNA approach. We enjoy the UI of NordLayer a bit more, but that is more of a personal preference. However, there are no free plans and you will have to pay a bit more per user. With that, you do get a bit more compared to Twingate though. Its proprietary VPN protocol is quick and secure and you can count on speeds of up to 1Gbs regardless of the pricing plan you go for. It is important to point out that additional features like auto-connect, ThreatBlock, and the Cloud Firewall do set a high bar for the competition, which is why you should consider it if you need more complex security.
Another potential alternative is the Check Point VPN Solution, which is geared more toward larger enterprises that are not afraid to break the bank to get premium solutions. Of course, to be fully covered here, we would recommend going with the hardware + software combo offered by Check Point, since this will ensure you get a ZTNA approach and have access to all of the bells and whistles. The admin console is powerful, with granularity extending from the setup into reporting and across all touch points. While it is powerful, for newer entrants into the field it can be a daunting task to set up the entire system. Pricing is not publicly available, as it depends on the size of your company and the specific needs that you have. But be sure it is not the cheapest solution in the market, but with the offering it has, it cannot be.
Final Verdict
With all that has been said, we can conclude that Twingate is an effective and efficient zero-trust network access solution. If you’re an organization or business looking to secure corporate resources, yet you want to have a remote workforce easily and securely access your resources without causing too much user friction, then Twingate may be the right tool for you.
High granularity, will surely expedite and secure work for organizations in highly regulated industries, which is one area that the company is aiming at. Another benefit is that this complexity doesn’t translate into a complex and clunky UI but an easy-to-use and highly intuitive cloud environment.
Sure, it is not the best option in the market, but it does tick most of the boxes while offering easy scaling which will not break the bank. What’s equally important, you can have your IT department spin up the free version, test out the performance, and see whether it is the right fit for you before deciding to scale up.
Sead is a seasoned freelance journalist based in Sarajevo, Bosnia and Herzegovina. He writes about IT (cloud, IoT, 5G, VPN) and cybersecurity (ransomware, data breaches, laws and regulations). In his career, spanning more than a decade, he’s written for numerous media outlets, including Al Jazeera Balkans. He’s also held several modules on content writing for Represent Communications.