Mac chips have another major security flaw
T2 chips can be compromised using a modified USB-C cable
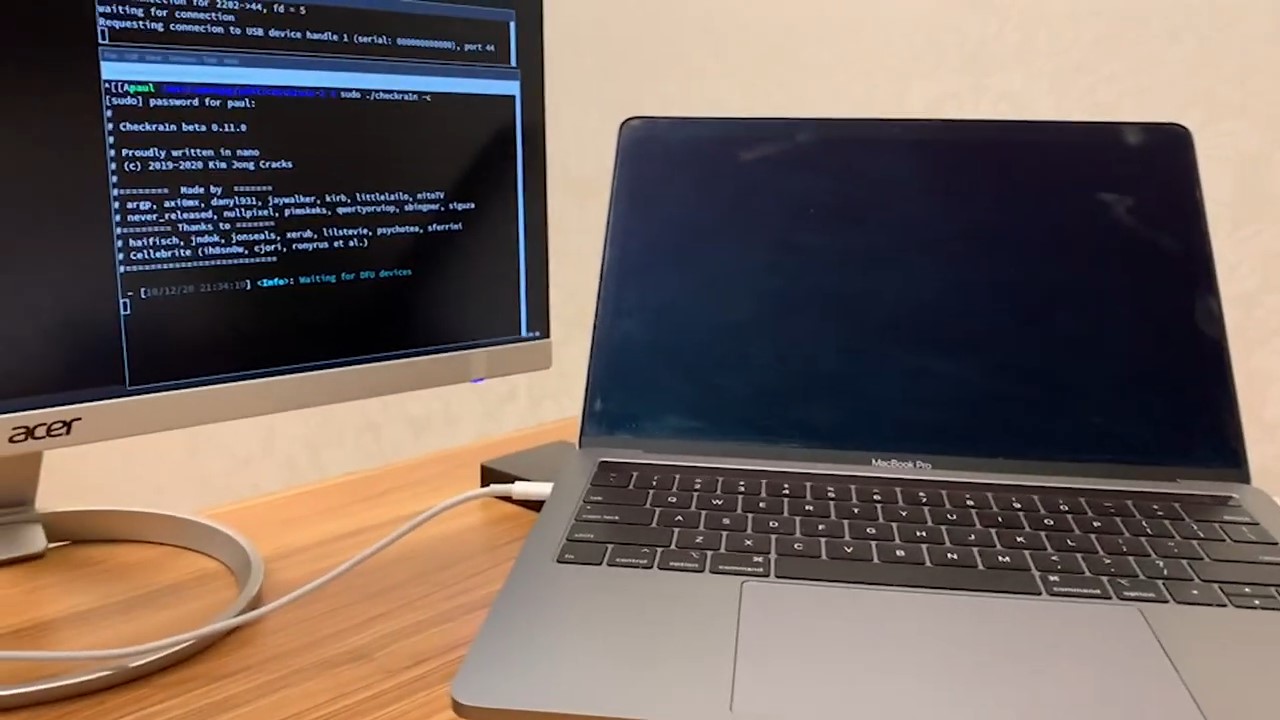
After revealing that it has found a way to take over the security chip in modern Macs, the T2 exploit team has now demonstrated that it can do so without user intervention by using a modified USB-C cable.
Members of the ad-hoc team go by the name Team t8012 which is a reference to Apple's own internal name for its T2 security chip that the company has been incorporating into all of its devices since 2018.
In addition to showing off its new USB-C Debug Probe which is now available for preorder, the T2 team has also released a video demonstrating exactly how it is able to take over Apple's Mac computers. In the video, a team member is seen plugging a USB-C cable into a Mac and running checkra1n on it.
- We've put together a list of the best antivirus software around
- These are the best security keys for protecting your credentials
- Also check out our roundup of the best secure routers
The target machine goes to a black screen while a connected computer shows that the operation was successfully performed. However, a second computer isn't needed for this attack as it is performed using a chip inside the modified USB-C cable. The T2 team also released a second video showing how it was able to alter the familiar white Apple logo seen during startup.
USB-C Debug Probe
In a blog post titled “Plug'nPwn - Connect to Jailbreak”, the T2 team explained how it was able to create a modified USB-C cable to compromise Apple's T2 security chip and install a keylogger, saying:
“By creating a specialized device about the size of a power charger, we can place a T2 into DFU mode, run checkra1n, replace the EFI and upload a key logger to capture all keys. This is possible even though macOS is un-altered (the logo at boot is for effect but need not be done). This is because in Mac portables the keyboard is directly connected to the T2 and passed through to macOS.”
9To5Mac's Ben Lovejoy spoke with Team t8012's Rick Mark who explained to him that he decided to participate in the T2 research as he believed it was possible to take over a Mac and that the same methods used by the T2 exploit team might already be in use in the wild.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Although an attacker would need physical access to a Mac computer to compromise its security using a modified USB-C cable, Mark suspects that nation-states and possibly even organized crime are already using this method for targeted attacks.
Team T2's USB-C Debug Probe is currently available for preorder for just $49.99 and we'll likely hear more once its in the hands of security researchers who can confirm its full capabilities.
- We've also highlighted the best endpoint protection
Via 9To5Mac
After working with the TechRadar Pro team for the last several years, Anthony is now the security and networking editor at Tom’s Guide where he covers everything from data breaches and ransomware gangs to the best way to cover your whole home or business with Wi-Fi. When not writing, you can find him tinkering with PCs and game consoles, managing cables and upgrading his smart home.
