China’s PlushDaemon group uses EdgeStepper implant to infect network devices with SlowStepper malware in global supply-chain attacks
PlushDaemon can compromise targets anywhere in the world

Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
- China-aligned PlushDaemon deploys malware through compromised routers
- PlushDaemon deploys LittleDaemon and DaemonLogistics on network devices
- The final payload, SlowStepper, can run commands and deploy spyware
China-aligned hacking group PlushDaemon has been spotted by ESET targeting routers and other network devices with malware to launch supply chain attacks.
The cybersecurity experts note the group has been active since 2018, and has so far deployed attacks against targets in the United States, New Zealand, Cambodia, Hong Kong, Taiwan, and mainland China.
The group deploys the EdgeStepper implant on network devices by exploiting software vulnerabilities, or by using default administrative credentials that have not been changed on the targeted infrastructure.
PlushDaemon strikes routers with malware
ESET researchers studied how the attack unfolded against software input method Sogou Pinyin.
Once EdgeStepper has been deployed, the implant will begin redirecting incoming DNS queries that relate to software updates to a malicious DNS node, which then directs software updates to a malicious IP address used for hijacking.

Rather than receiving a software update from the legitimate node, a DLL file containing the LittleDaemon malware downloader is served from the hijacking node. LittleDaemon then serves the DaemonicLogistics malware dropper which is executed in memory, retrieving the final step in the attack: SlowStepper.
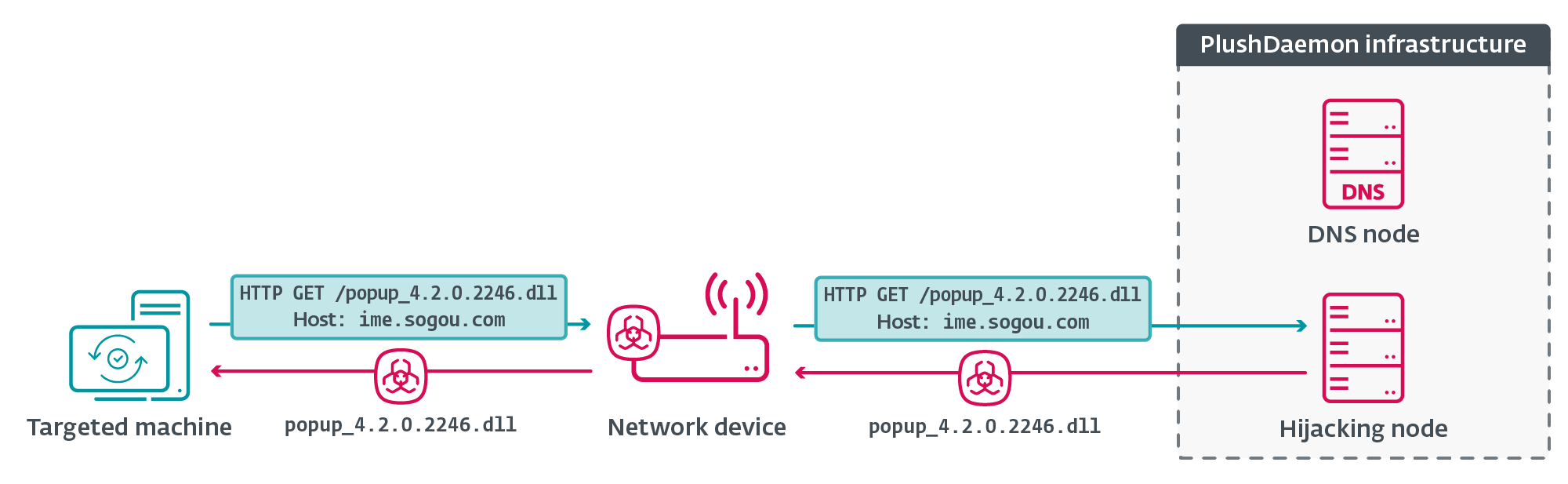
Slowstepper can perform a range of malicious actions, such as pulling system information, deploying Python-based spyware to log keystrokes and steal credentials, or execute files and run commands. Due to the nature of PlushDaemon’s attack vector, the group has “the capability to compromise targets anywhere in the world.”
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
For more information on indicators of compromise and technical details on the malware, take a look at ESET’s Research on PlushDaemon.

➡️ Read our full guide to the best antivirus
1. Best overall:
Bitdefender Total Security
2. Best for families:
Norton 360 with LifeLock
3. Best for mobile:
McAfee Mobile Security

Benedict has been with TechRadar Pro for over two years, and has specialized in writing about cybersecurity, threat intelligence, and B2B security solutions. His coverage explores the critical areas of national security, including state-sponsored threat actors, APT groups, critical infrastructure, and social engineering.
Benedict holds an MA (Distinction) in Security, Intelligence, and Diplomacy from the Centre for Security and Intelligence Studies at the University of Buckingham, providing him with a strong academic foundation for his reporting on geopolitics, threat intelligence, and cyber-warfare.
Prior to his postgraduate studies, Benedict earned a BA in Politics with Journalism, providing him with the skills to translate complex political and security issues into comprehensible copy.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.