TechRadar Verdict
G Data was a pain to set up, and despite claims of using AI and machine learning to hunt for threats, it failed to detect and prevent a malware infection. But hey, at least it’s easy to register and use.
Pros
- +
Clear interface
- +
Easy registration
- +
Self-hosting management server
Cons
- -
Grueling setup
- -
Failed to spot an intrusion
- -
No pricing models displayed beforehand
Why you can trust TechRadar
The G Data Endpoint Security Solution is a business product built by the German cybersecurity outlet G Data CyberDefense AG. The company has been around since 1985, but has mostly lived in the shadows of the likes of Avast, or Bitdefender.
Today, we’re taking a closer look at the company’s endpoint protection (EPP) offering, to see if it can stand shoulder to shoulder with the best endpoint protection software out there.
If budget is your number one concern, and would like to know - at least broadly - how much this product will cost your business, I’ll have to disappoint you. The main product page does not detail any pricing plans, and instead invites you to either arrange a consultation, or test the trial version for free.
To be fair, G Data is not the only endpoint security solutions provider that does this, but having a basic pricing model is always helpful when deciding if a product is a good fit for an organization or not.
The good news is that testing the software is quite easy. All you need to do is fill out an online form, and you’ll be given a download link to the trial version, paired with temporary login credentials.
G Data Endpoint Protection Business: Key Features
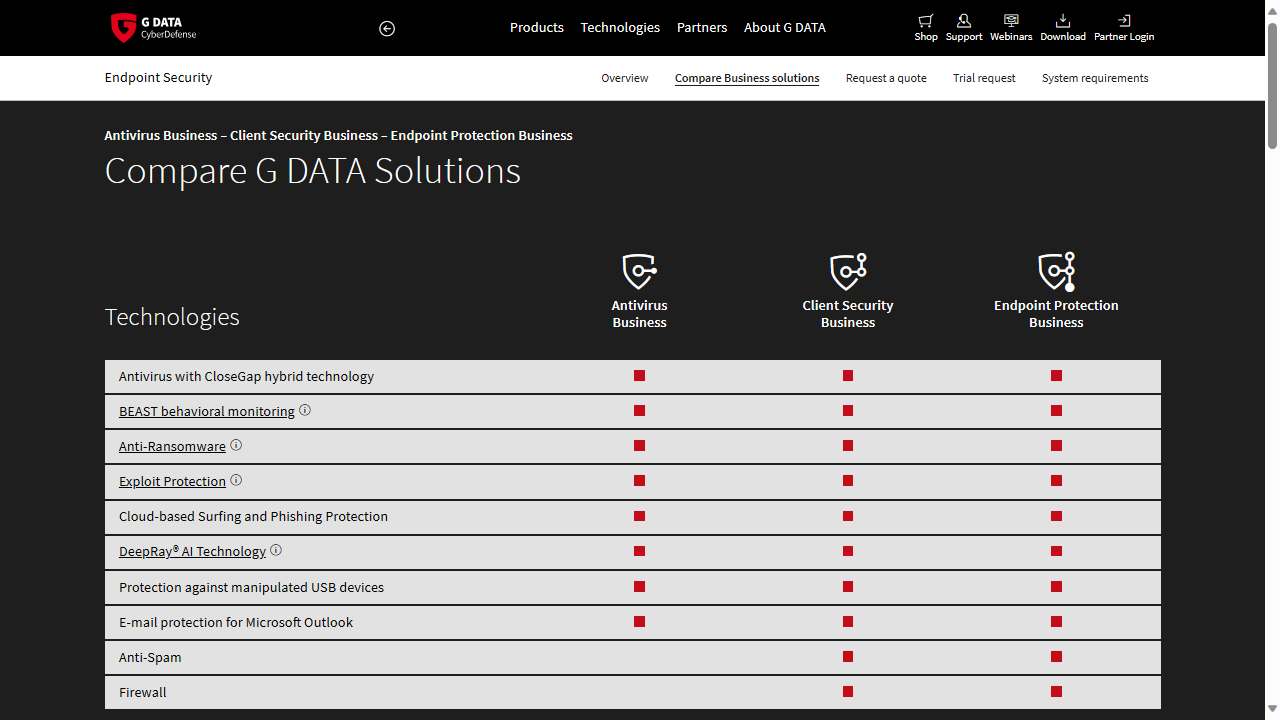
G Data Endpoint Protection Business’ key features include central management, mobile device management, anti-spam, a dedicated firewall and policy management. There are also optional add-ons for “Mail Server & Proxy Security”. We were pleasantly surprised to see the product page actually providing a detailed comparison of the different offerings, more than what competing companies are doing.
That being said, the Endpoint Protection Business includes the company's 'BEAST' behavioral monitoring which, according to G Data, displays all system behavior in a graphical interface. That should allow you to better detect any malicious processes on the network.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The EPP solution also uses G Data's “DeepRay AI Technology”, apparently leveraging artificial intelligence and machine learning to detect malicious files faster.
Email protection is also available (albeit just for Microsoft Outlook), as is anti-spam technology, protection against corrupted USB drives, and a dedicated firewall.
G Data Endpoint Protection Business: Installing the solution
Like we said earlier, getting the download link is a simple procedure, and that shouldn’t be taken lightly, since many endpoint security platforms either don’t offer a free trial, or demand payment information upfront. However, there is a catch. The product isn’t available as a cloud console, which means you’ll need to install it on your own server.
That means having a server in the first place that can handle managing as many endpoints as you have, and then downloading a 4.7GB compressed archive. This isn’t necessarily a bad thing, especially if your organization works with sensitive data. By setting up your own management server, you don’t have to trust your endpoint information with a third party.
The installation process was quick and seamless. Be careful to switch the language to English at the beginning of the installation process, since the default one is German. Also, the installer will prompt you to choose if you’re setting things up on the main server, or a secondary/subnet server.
After that, you’ll be asked to choose the database installation method. Those with less than 1,000 clients, the installer recommends using Microsoft SQL Server 2014 Express. You can also configure a connection to an existing database.
The rest of the installation process took around 10 minutes in my test.
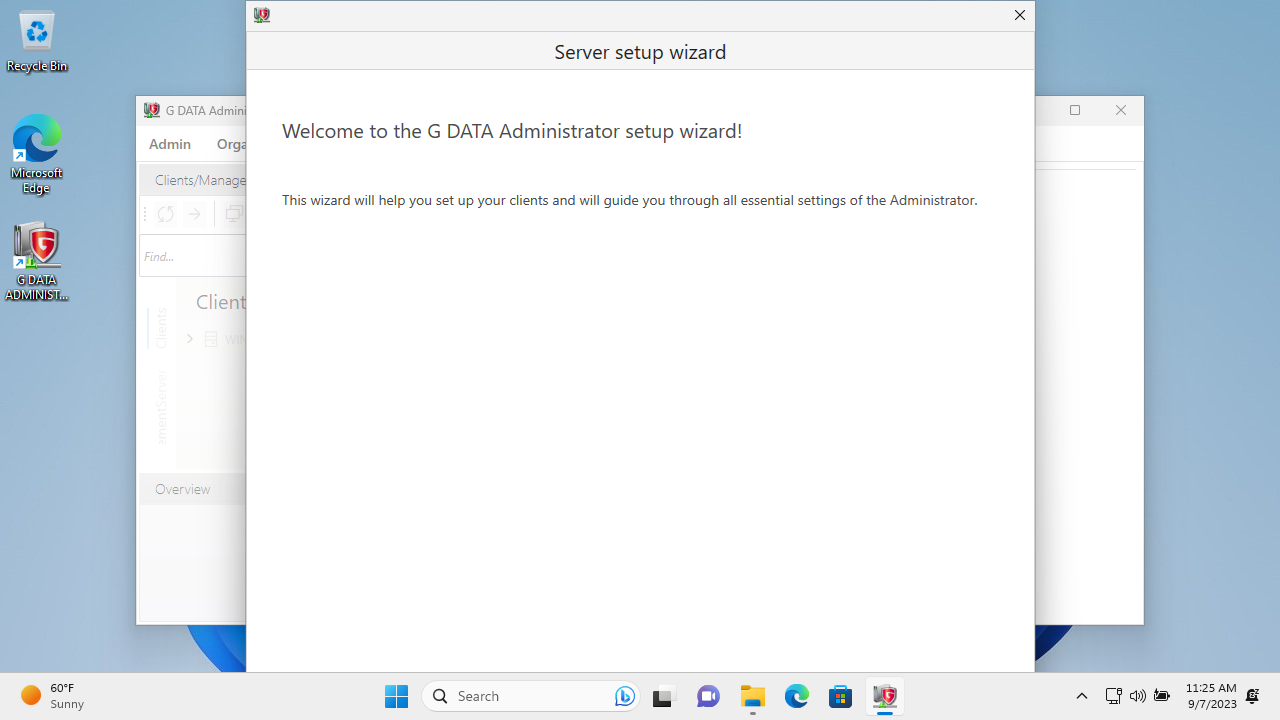
After logging into the Management Server, the “G Data Administrator Setup Wizard” launched, which is used to allow IT teams to install G Data’s security client on different endpoints. It was surprising to see that after restarting the PC, G Data’s Agent Software didn’t launch automatically in the system tray, and after firing it up, the client was shown as disconnected.
Reinstalling the tool on a clean test machine running Windows 11 solved all these problems, though.
G Data Endpoint Protection Business: Running the tool
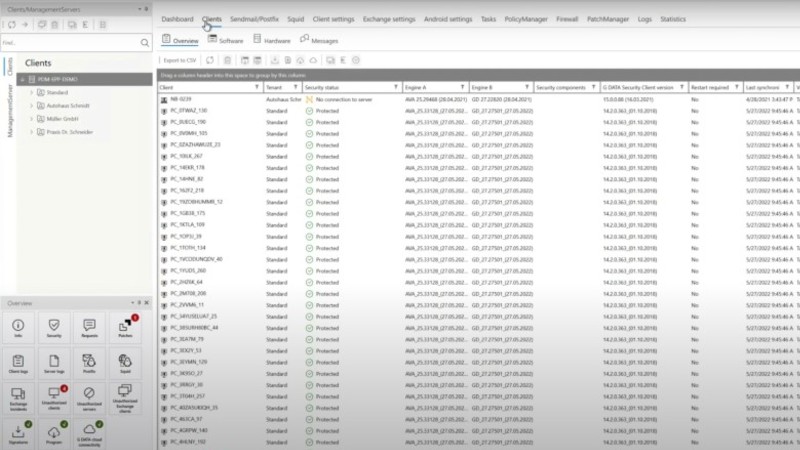
Once the client was installed, we were met with another surprise - there was no interface on the client side. The system tray icon comes with a short menu for running updates and reading more information about the app.
The management interface was a more pleasant surprise, though. The main page (Dashboard) offers a list of security events that are easy to follow, and things like client connections, warnings, and status reports, are all in the form of an infographic, making them easy to read and digest. In the Overview page, you’ll find a list of launcher icons for different features, such as “Security”, or “Client Logs”.
G Data Endpoint Protection Business: Testing for efficiency
We gave G Data’s EPP two trials - one with a fake malware, and one with an actual malware. In the first test, we tried to download a fake EICAR virus in a compressed .ZIP format, but was unable to extract the file. G Data Security Client detected the malicious file and changed its permissions so that we were unable to interact with it any further.
The strange thing is that we were never notified. Only after logging into the Management server and reviewing the security logs were we able to see what happened. There is no pop-up, or alert, on the client side, and the file wasn’t quarantined.
All things considered, we concluded that the product passed the first trial.
In the second trial, we tried copying a real computer virus, grabbed from the wild wild web, and placed into the machine’s “Downloads” folder. The idea was to see if the endpoint security solution can detect files based on suspicious behavior, not just cross-reference them with a database of known malware.
Unfortunately, the product failed, as we were able to successfully run the malware. To make matters worse, there were no alerts in the Management Server. The built-in Windows real-time protection would have caught the malware but unfortunately, the G Data client disabled it during installation.
G Data Endpoint Protection Business: Final verdict
While we were installing G Data programs, there was a splash screen saying "Trust in German Sicherheit' (Security)".
If you’re expecting the stereotypical German organization, or attention to detail, we suggest you look elsewhere, as there are too many things going wrong here. Knowing at least a basic pricing model in advance would help a lot. The setup process is too cumbersome, and it took us a few stabs just to get it working. But most importantly, real-time detection is limited.
On the bright side, being able to install the management platform on an on-prem server has its security benefits. The registration process leading to a trial download link is also relatively painless.
Overall though, we believe there are better alternatives out there.
We've featured the best cloud antivirus.
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.