Sponsored by Paessler
What is Syslog and why does it matter?
Unified log management for your network infrastructure
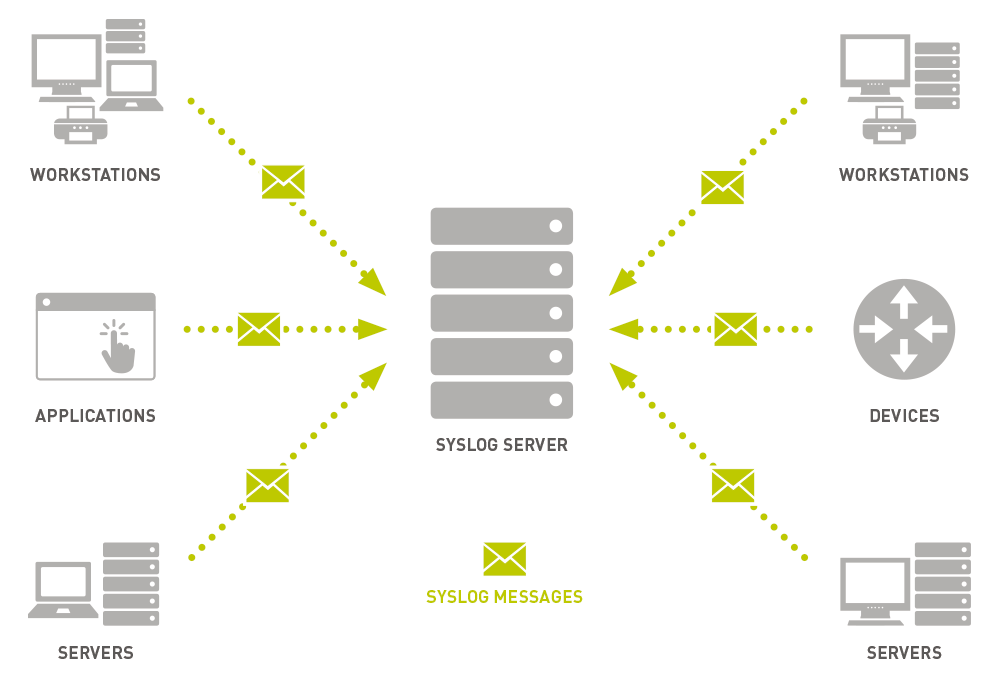
You're staring at a screen full of error messages. Your network is acting up. Servers are throwing warnings. You need answers fast.
But when logs are scattered across dozens of devices in different formats and locations, troubleshooting is next to impossible. This is where Syslog comes in. System administrators, network engineers, and IT managers need centralized visibility to parse through errors.
Syslog standardizes messages across all your devices and software, so you can have a bird's eye view of your entire network.
Get the unlimited trial version for 30 days, absolutely free
For a limited time, new users can head over to Paessler’s website, navigate to the PRTG Network Monitor solution, and click “Free Trial”. They will be redirected to the download page, where they will receive a unique, freshly generated license key. The download will start automatically, and installation can be completed in just a few moments.
Techradar Pro Approved Sponsored Offer
Syslog meaning with examples
Syslog is a standard protocol for message logging that allows devices and applications to send log messages to a centralized server.
It separates the software that generates messages from the system that stores them, creating a unified system for log management across your infrastructure.
Think of Syslog as your network's central post office. Instead of each device keeping its own logs locally, they all send their messages to one place where you can monitor everything together.
This protocol was originally developed for Unix systems in the 1980s but has since become the universal standard for logging across Linux apps, Windows, network devices, and applications.
Most network devices like routers, switches, and firewalls support this protocol out of the box. It standardizes how log messages are formatted, making it easier for administrators to interpret events from different sources using the same tools and processes.
For example, your company firewall software detects a security breach at 2:47 AM. The firewall immediately sends a Syslog message to your central logging server.
This message includes the timestamp, device IP address, severity level (critical), and detailed information about the intrusion attempt.
Your security team receives an instant alert and can investigate the incident using centralized logs that show the complete attack timeline across all network devices.
How does Syslog work? Protocols, servers, clients, and more
Syslog operates on a straightforward client-server architecture. The process begins when applications, systems, or devices generate log messages based on predefined events or conditions.
These messages typically include essential details like timestamps, source information, and descriptive content that helps administrators understand what happened.
The Syslog client (also called the sender or agent) takes these generated messages and forwards them to a designated Syslog server using the Syslog protocol.
This forwarding happens automatically in real-time, ensuring you get immediate visibility into system events as they occur. The server receives these messages, processes them according to configured rules, and stores them for analysis and monitoring.
What makes Syslog powerful is its three-layer architecture. The content layer contains the actual event information, the application layer handles message routing and interpretation, and the transport layer manages how messages travel across your network.
This separation allows different components to be updated independently while maintaining compatibility across diverse systems.
Syslog protocols
Syslog supports both UDP and TCP protocols for message transport, each serving different needs in your infrastructure.
UDP on port 514 is the traditional choice and remains the default for most implementations. It's fast and efficient, making it ideal for high-volume logging environments where speed matters more than guaranteed delivery.
However, UDP's connectionless nature means there's no guarantee that messages will reach their destination. If network congestion occurs or the Syslog server is temporarily unavailable, some log messages might be lost.
This is acceptable for many use cases, especially when dealing with informational messages or when some data loss is tolerable.
TCP provides reliable message delivery with acknowledgment and error correction, though it operates on different ports (commonly 601 or 1468).
Modern Syslog implementations like rsyslog and syslog-ng support TCP configuration, giving you the option to choose reliability over speed when needed.
Some organizations configure devices to send messages to multiple Syslog servers for redundancy, ensuring critical logs are never lost.
Syslog servers
A Syslog server is the central hub that receives, processes, and stores log messages from across your network.
These servers can be physical machines, virtual machines, or cloud-based services specifically designed to handle large volumes of log data. The server continuously listens on designated ports for incoming messages from Syslog clients.
The core components of a Syslog server include the listener that collects network messages, a database or file system for storing logs, and management software for filtering and searching through the data.
Modern Syslog servers can handle thousands of messages per second, automatically parsing and categorizing them based on source, severity, and content.
Advanced Syslog servers offer features like log rotation, compression, and automated archiving to manage storage efficiently.
They also provide filtering capabilities that let you drop irrelevant messages, redirect specific types of logs to different locations, or trigger automated responses based on message content. This flexibility is crucial for organizations that generate massive amounts of log data daily.
Syslog clients
Any device or application that sends log messages to a Syslog server functions as a Syslog client. This includes network equipment like switches, routers, and firewalls, as well as servers, workstations, and specialized devices like intrusion detection systems and IoT sensors.
The client's job is to generate properly formatted Syslog messages and transmit them to the designated server.
Syslog clients can be built into the device's operating system or added through specialized software agents. Most Unix-like systems have native Syslog support, while Windows systems typically use third-party agents or built-in event forwarding capabilities.
Network devices usually include Syslog functionality in their firmware, allowing you to configure logging destinations through the device's management interface.
The configuration process involves specifying the Syslog server's IP address, choosing the transport protocol (UDP or TCP), and setting the types of events to log.
Many clients allow you to configure multiple Syslog servers for redundancy and can filter messages based on severity levels or facility codes before transmission. This client-side filtering reduces network traffic and ensures only relevant messages reach your central logging infrastructure.
Syslog messages: explained
Syslog messages follow a standardized format that makes them readable across different systems and platforms.
The message structure includes several key components: a priority field that combines facility and severity information, a timestamp indicating when the event occurred, the hostname or IP address of the source device, and the actual message content describing what happened.
There are two main Syslog message formats in use today. The original BSD format (RFC 3164) uses the structure timestamp hostname: message, while the newer IETF format (RFC 5424) includes additional fields like timestamp hostname process[pid]: message.
The newer format provides more detailed information about the process that generated the message, making it easier to trace events back to their source.
The priority field deserves special attention because it encodes both the facility (source type) and severity (importance level) into a single numerical value using the formula: Priority = (Facility × 8) + Severity.
This mathematical relationship allows Syslog receivers to quickly determine both where a message came from and how important it is, enabling efficient filtering and routing decisions.
Syslog facility codes
Facility codes identify the type of system or process that generated a log message. These codes help administrators understand the source of events and configure appropriate handling rules for different types of messages.
The facility system originated from Unix processes but has been extended to cover modern applications and services.
The standard facility codes include:
- 0 (kern) - Kernel messages from the operating system core
- 1 (user) - User-level messages from applications and processes
- 2 (mail) - Mail system events and errors
- 3 (daemon) - System daemon messages from background services
- 4 (auth) - Security and authentication-related events
- 5 (syslog) - Messages generated by the Syslog daemon itself
- 6 (lpr) - Line printer subsystem events
- 7 (news) - Network news subsystem messages
- 8 (uucp) - UUCP (Unix-to-Unix Copy) protocol events
- 9 (cron) - Cron scheduler and time-based job messages
- 10 (authpriv) - Restricted access security and authentication logs
- 11 (ftp) - FTP daemon events and file transfer logs
- 16-23 (local0-local7) - Reserved for custom application logging
Syslog severity levels
Severity levels indicate the importance and urgency of log messages, ranging from 0 (most critical) to 7 (least critical).
These levels help administrators prioritize their response to different types of events and configure automated alerting systems appropriately. Understanding severity levels is crucial for effective log management and incident response.
The eight standard severity levels are:
- 0 (Emergency) - System is unusable, immediate action required
- 1 (Alert) - Action must be taken immediately to prevent system failure
- 2 (Critical) - Critical conditions that could lead to system failure
- 3 (Error) - Error conditions that affect system operation
- 4 (Warning) - Warning conditions that indicate potential problems
- 5 (Notice) - Normal but significant conditions worth noting
- 6 (Informational) - Informational messages for general system activity
- 7 (Debug) - Debug-level messages for detailed troubleshooting
These severity levels allow you to filter logs based on importance, ensuring critical alerts reach the right people immediately while routine informational messages are stored for later analysis.
Most logging systems let you configure different handling rules for each severity level, such as sending emergency messages to on-call staff while archiving debug messages for developer use.
Syslog implementation
When you decide to implement Syslog in your environment, you need specialized software to handle the incoming messages. This is where Syslog daemons come into play.
A daemon is simply a background service that runs continuously on your server, automatically handling tasks without user intervention. Think of it like having a dedicated receptionist who sorts and files mail all day long.
Syslog daemons are the workhorses that make centralized logging possible. They listen for incoming log messages from across your network, decide what to do with each message based on your rules, and store or forward them accordingly.
During implementation, you'll configure the daemon to specify which messages to accept, where to store them, and whether to send copies to other servers. The daemon handles all this processing automatically, ensuring your logs are organized and accessible when you need them.
Syslogd
Syslogd is the original daemon from the 1980s. It's still the default on OpenBSD and older systems. This daemon handles basic syslog functions reliably. It processes messages through the /etc/syslog.conf configuration file.
However, syslogd has limitations. It only supports UDP transport, which doesn't guarantee message delivery.
Older versions may not support custom ports either. The daemon lacks advanced features like encryption or complex filtering. Despite these constraints, syslogd remains stable and lightweight for simple logging needs.
Rsyslog
Rsyslog emerged in 2004 as an enhanced replacement for syslogd. It maintains backward compatibility with the original configuration syntax.
This makes migration straightforward—you can copy your old config file directly. Rsyslog is now the default on Ubuntu, RHEL, and many modern distributions.
The daemon adds powerful features while keeping familiar syntax. It supports both TCP and UDP transport protocols. You get high-performance processing and modular architecture.
Advanced filtering, encryption, and database output are built in. Rsyslog uses /etc/rsyslog.conf for configuration. Remote forwarding uses simple syntax: @IP for UDP and @@IP for TCP.
Syslog-ng
Syslog-ng launched in the late 1990s as a next-generation solution. It introduced TCP support, encryption, and advanced filtering first.
The daemon uses object-oriented configuration that's highly flexible. Everything becomes an object: sources, destinations, filters, and rules.
This daemon stands out for its clear syntax and portability. It works across Linux, BSD, Solaris, and AIX platforms. The configuration file lives at /etc/syslog-ng/syslog-ng.conf.
However, syslog-ng uses a completely different syntax from traditional daemons. Remote forwarding requires more complex configuration compared to rsyslog. Despite this complexity, syslog-ng excels in multi-platform environments requiring sophisticated log routing.
Syslog protocol: pros, cons and use cases
Despite being decades old, Syslog remains popular for good reasons. Its simplicity and widespread adoption make it a reliable choice. However, you should understand both its strengths and limitations before implementing it. Let's take a look at some common use cases to understand it better, then jump right into pros and cons.
Use cases
- Security Monitoring and Incident Response: Syslog centralizes security events from firewalls, intrusion detection systems, and access controls. This gives you a complete view of potential threats across your network. Security teams can correlate events quickly and respond to incidents faster.
- Compliance and Auditing: Regulatory requirements like PCI-DSS, HIPAA, and ISO 27001 demand comprehensive logging. Syslog provides the audit trail organizations need for compliance reporting. You can demonstrate system access, configuration changes, and security events to auditors.
- Network Troubleshooting: When network issues arise, Syslog helps you trace problems across devices. Router, switch, and firewall logs combine into one searchable database. This makes root cause analysis much more efficient than checking individual devices.
- System Performance Monitoring: Applications and servers send performance metrics through Syslog messages. You can track CPU usage, memory consumption, and disk space warnings centrally. This proactive monitoring helps prevent outages before they impact users.
- Application Debugging: Developers use Syslog to track application behavior in production environments. Debug messages, error conditions, and user activities flow to central servers. This makes troubleshooting much easier than searching through scattered log files.
Pros
- Universal Compatibility: Nearly every operating system and device supports Syslog natively.
- Centralized Management: All your logs flow to one location for easier analysis and monitoring.
- Standardized Format: Messages follow consistent structure across different sources and vendors.
- Easy Implementation: Most systems include Syslog support out of the box.
- Scalable Architecture: The protocol handles large volumes of log data efficiently.
- Cost-Effective: Open-source daemons provide enterprise-grade logging without licensing fees.
Cons
- No Built-in Security: The protocol lacks encryption and authentication by default.
- Unreliable UDP Transport: Standard UDP implementation doesn't guarantee message delivery.
- Limited Processing: Basic filtering and routing capabilities compared to modern solutions.
- No Long-term Storage: Syslog itself doesn't handle log retention or archiving.
- Potential Performance Bottlenecks: High-traffic environments may overwhelm Syslog servers.
- Minimal Message Structure: Simple format limits metadata and context information.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!

Ritoban Mukherjee is a tech and innovations journalist from West Bengal, India. These days, most of his work revolves around B2B software, such as AI website builders, VoIP platforms, and CRMs, among other things. He has also been published on Tom's Guide, Creative Bloq, IT Pro, Gizmodo, Quartz, and Mental Floss.
