Sponsored by Paessler
What is SNMP and why does it matter?
Standardize data collection across your network equipment
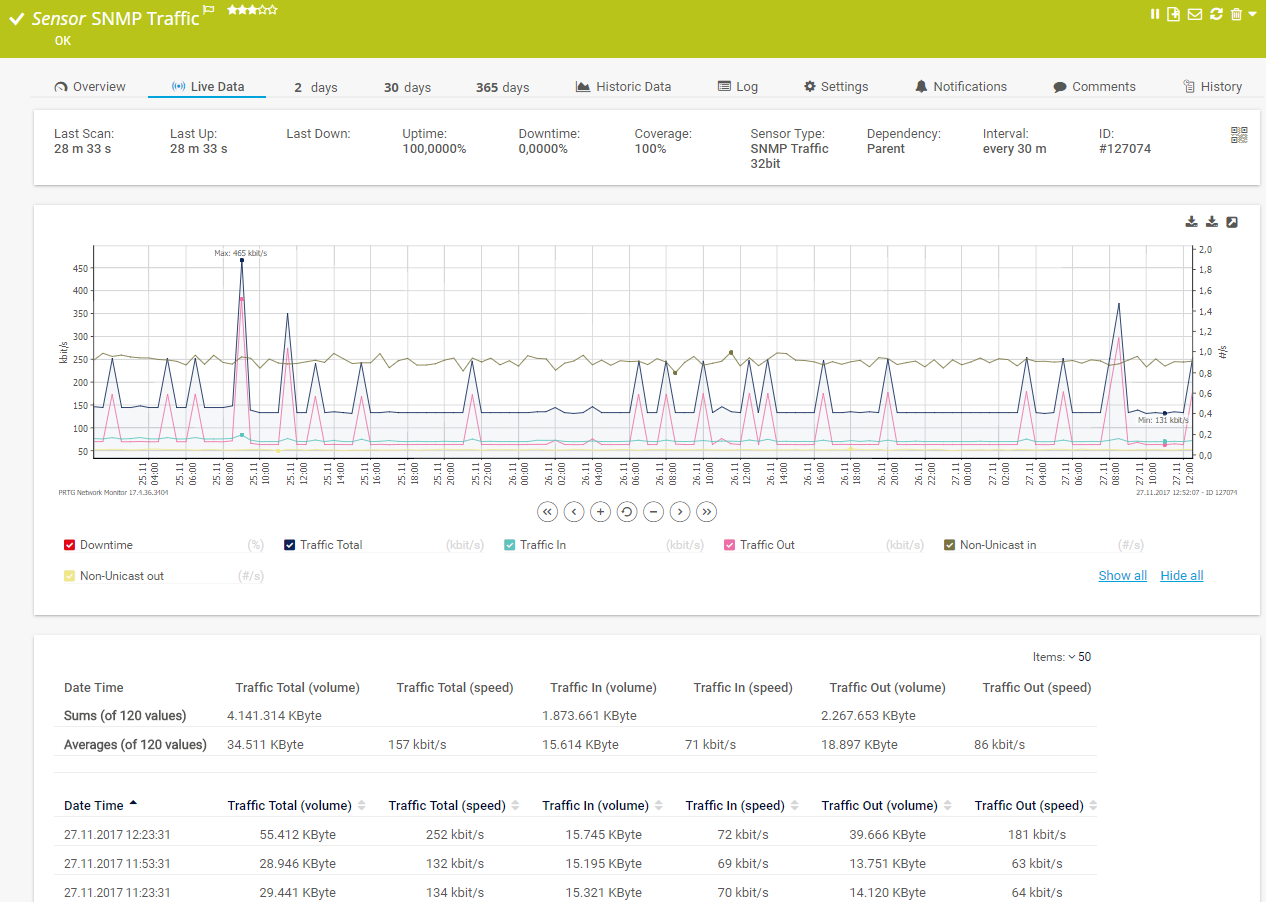
When devices fail and servers go down without warning, you need a real-time monitoring system that actually works.
Suppose you're managing complex networks with hundreds of devices. In that case, SNMP gives you the standardized monitoring framework you need to stay ahead of problems that can bring your servers down and grind business activity to a halt.
Many network monitoring systems today run on the SNMP protocol, making it easier to connect with devices that support this framework.
Get the unlimited trial version for 30 days, absolutely free
For a limited time, new users can head over to Paessler’s website, navigate to the PRTG Network Monitor solution, and click “Free Trial”. They will be redirected to the download page, where they will receive a unique, freshly generated license key. The download will start automatically, and installation can be completed in just a few moments.
Techradar Pro Approved Sponsored Offer
What is the SNMP Protocol: Definition with examples
Simple Network Management Protocol (SNMP) is an application-layer protocol that enables network administrators to monitor and manage network devices across IP networks. It provides a standardized way for devices like routers, switches, servers, and printers to communicate status information to centralized management systems.
SNMP operates on a simple client-server model. It lets network management systems collect data from distributed devices, configure remote equipment, and receive alerts when problems occur. Think of it as a universal language that lets your network devices talk to your monitoring software, regardless of manufacturer or device type.
Most network devices come with SNMP agents pre-installed, making deployment straightforward once you configure the basic settings. This means you can monitor everything from enterprise switches to small office printers using the same protocol.
Example: Your company has 200 network devices across multiple locations. Instead of manually checking each device daily, you deploy a monitoring system that automatically polls each device every few minutes.
When a router in your remote office starts running hot, SNMP agents immediately send a trap message to your central monitoring dashboard, alerting you before the device fails.
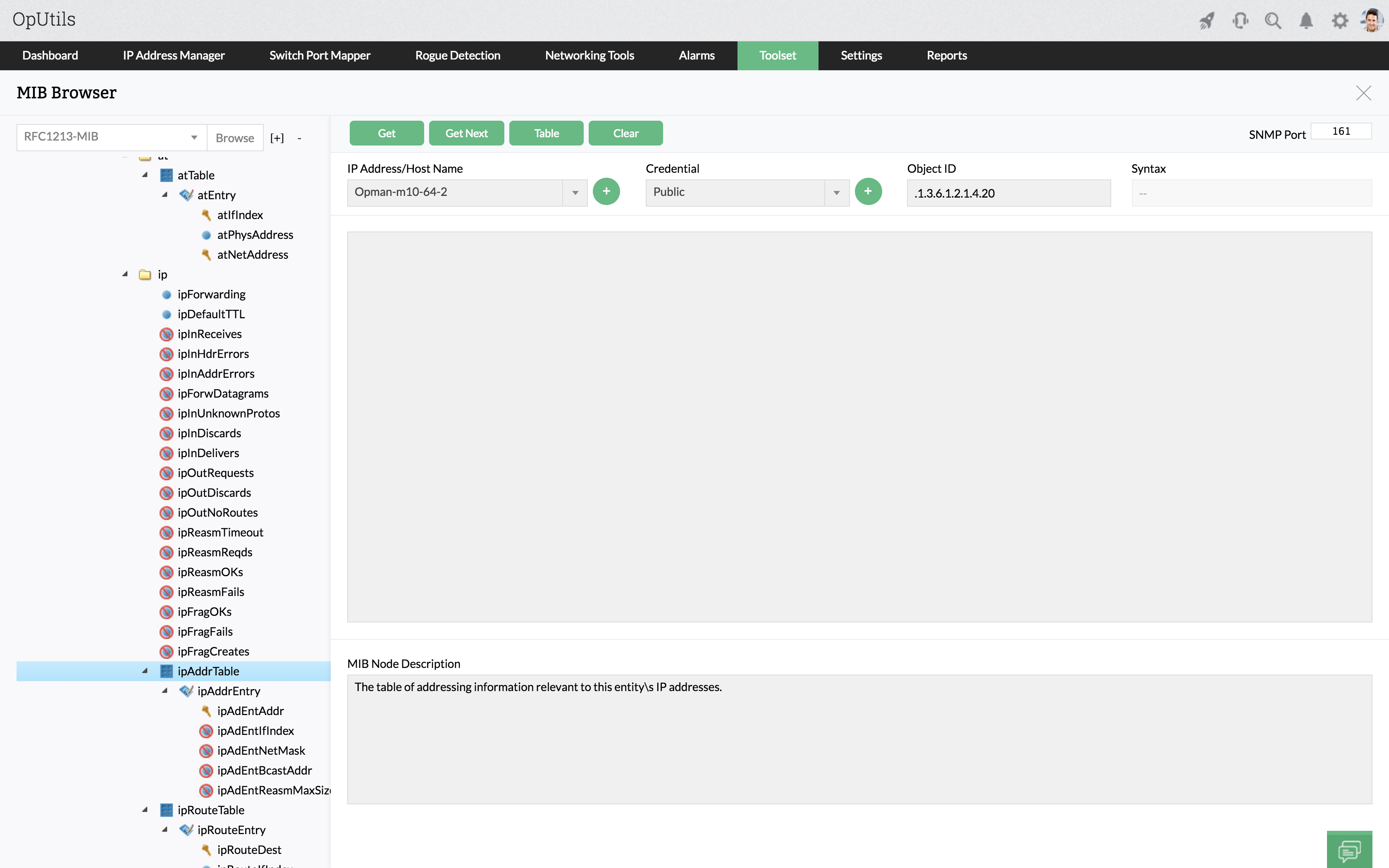
How does SNMP work? Versions, components, and architecture
SNMP operates within the application layer of the Internet protocol suite using UDP for transport. The protocol uses a manager-agent architecture where SNMP managers (your monitoring systems) communicate with SNMP agents (software running on network devices) to collect data and send commands.
All communication happens over well-defined ports. So agents receive requests on UDP port 161, while managers receive notifications on port 162.
SNMP revolves around Management Information Bases (MIBs), which are structured databases that define what information each device can provide. Each piece of data in a MIB has a unique Object Identifier (OID) that serves as an address, enabling managers to request specific information from agents.
SNMP's distributed architecture makes it incredibly scalable. You can monitor thousands of devices from a single management station, with each device independently reporting its status and responding to queries.
This design ensures that network monitoring doesn't create significant overhead on your network infrastructure.
SNMP versions
SNMP has evolved through three major versions, each addressing many limitations of its predecessors. SNMPv3 has made significant advancements in network management capabilities over SNMPv1, now offering better security and enhanced performance.
- SNMPv1: Original implementation described in RFC 1157, using simple community strings for authentication. This version operates only over UDP and provides basic monitoring capabilities with 32-bit counters. While functional, it lacks security features and has limited error-handling capabilities.
- SNMPv2c: An improved version with enhanced error handling and efficiency, described in RFC 1901. It introduced 64-bit counters and bulk operations for better performance. The "c" stands for "community," indicating it still uses community strings for authentication but can work over both UDP and TCP.
- SNMPv3: Most recent SNMP version, introducing comprehensive security features through RFC 3410. It provides authentication, encryption, and access control mechanisms using Hash-based Message Authentication Code (HMAC). This version supports both UDP and TCP transport, making it suitable for enterprise environments requiring robust security.
SNMP components
SNMP's architecture consists of four components that work together in tandem. Each component plays a specific role in the SNMP ecosystem. Together, they enable distributed network management across different device types and network topologies.
- SNMP Manager: The centralized system that monitors and manages network devices, acting as the client in the client-server model. It sends requests to agents, processes responses, and receives trap notifications from devices experiencing issues. Modern SNMP managers often include graphical interfaces and automated alerting systems.
- SNMP Agent: Software running on network devices that collects and manages device information, acting as the server. Agents maintain local MIB databases and respond to manager requests with the current device status. They also generate trap messages when significant events occur on the device.
- Management Information Base (MIB): A structured database that defines what information can be collected from devices and what can be configured. MIBs use a hierarchical tree structure with unique Object Identifiers (OIDs) for each data element. Standard MIBs are defined by organizations like IETF, while vendors create proprietary MIBs for device-specific features.
- Managed Devices: The actual network equipment (routers, switches, servers, printers) that run SNMP agents. These devices expose their operational data through MIBs and can be monitored and configured remotely. Any IP-addressable device can potentially be managed via SNMP.
SNMP messages: explained
SNMP communication relies on Protocol Data Units (PDUs) that carry management information between managers and agents. These messages follow a standardized format that includes IP header, UDP header, SNMP version, community string, PDU type, request ID, error status, error index, and variable bindings.
The structured format ensures consistent communication regardless of device manufacturer or network complexity.
The message format enables efficient data exchange while maintaining protocol simplicity. Each message contains enough information for the receiving device to process the request correctly and respond appropriately.
SNMP's use of UDP makes communication lightweight, though it means the protocol doesn't guarantee message delivery.
Message types fall into two categories: request messages initiated by managers and response messages from agents. This bidirectional communication model supports both polling-based monitoring and event-driven notifications, giving you flexibility in how you monitor your network infrastructure.
SNMP message commands
SNMP defines seven core message types that enable comprehensive network management operations. These commands provide the foundation for all SNMP-based monitoring and configuration activities.
Each message type serves a specific purpose in network management workflows. Understanding when and how to use each command type helps you optimize your monitoring strategies and reduce network overhead.
- GetRequest: The most common SNMP message, where managers request specific data from agents using Object Identifiers. The agent responds with the current value of the requested object. This forms the basis of most network monitoring operations.
- GetNextRequest: Allows managers to discover available data by requesting the next object in the MIB hierarchy. Starting from OID 0, managers can traverse the entire MIB tree without prior knowledge of available objects. This enables network discovery and inventory management.
- GetBulkRequest: Introduced in SNMPv2, this optimized version retrieves multiple objects in a single request. It reduces network traffic by combining multiple GetNext operations into one message. This improves efficiency when collecting large amounts of data from devices.
- SetRequest: The only write operation in SNMP, allowing managers to modify configuration parameters on remote devices. Agents confirm successful changes by responding with the new value. This enables remote device configuration and management.
- Response: Messages sent by agents in reply to manager requests, containing the requested data or confirmation of changes. These messages include error codes if the requested operation cannot be completed. Response messages form the backbone of SNMP communication.
- Trap: Unsolicited messages sent by agents to notify managers of significant events or threshold breaches. Traps enable real-time alerting without requiring continuous polling from managers. They're essential for proactive network monitoring and incident response.
- InformRequest: Similar to traps, but includes an acknowledgment mechanism introduced in SNMPv2. Agents can resend informative messages until they receive confirmation from the manager. This ensures critical notifications are not lost in network transmission.
SNMP security levels
SNMPv3 comes pre-equipped with three security levels that define authentication and encryption requirements for SNMP communications.
They provide graduated security options to match your network's risk profile and compliance requirements.
Higher security levels provide better protection but require more processing power and network overhead for encryption and authentication operations.
- noAuthNoPriv: Provides no authentication beyond username matching and no encryption of SNMP messages. This level offers the same security as SNMPv1 and SNMPv2c, relying only on community strings or usernames. It's suitable for low-risk environments where network traffic is already protected.
- authNoPriv: Requires cryptographic authentication using HMAC with MD5 or SHA algorithms but provides no message encryption. This level ensures message integrity and sender authentication while keeping content readable. It's appropriate when you need to verify message authenticity but don't require content privacy.
- authPriv: Provides both authentication and privacy through encryption using DES-56 or AES algorithms. This highest security level ensures both message integrity and content confidentiality. It's essential for environments handling sensitive data or operating over untrusted networks.
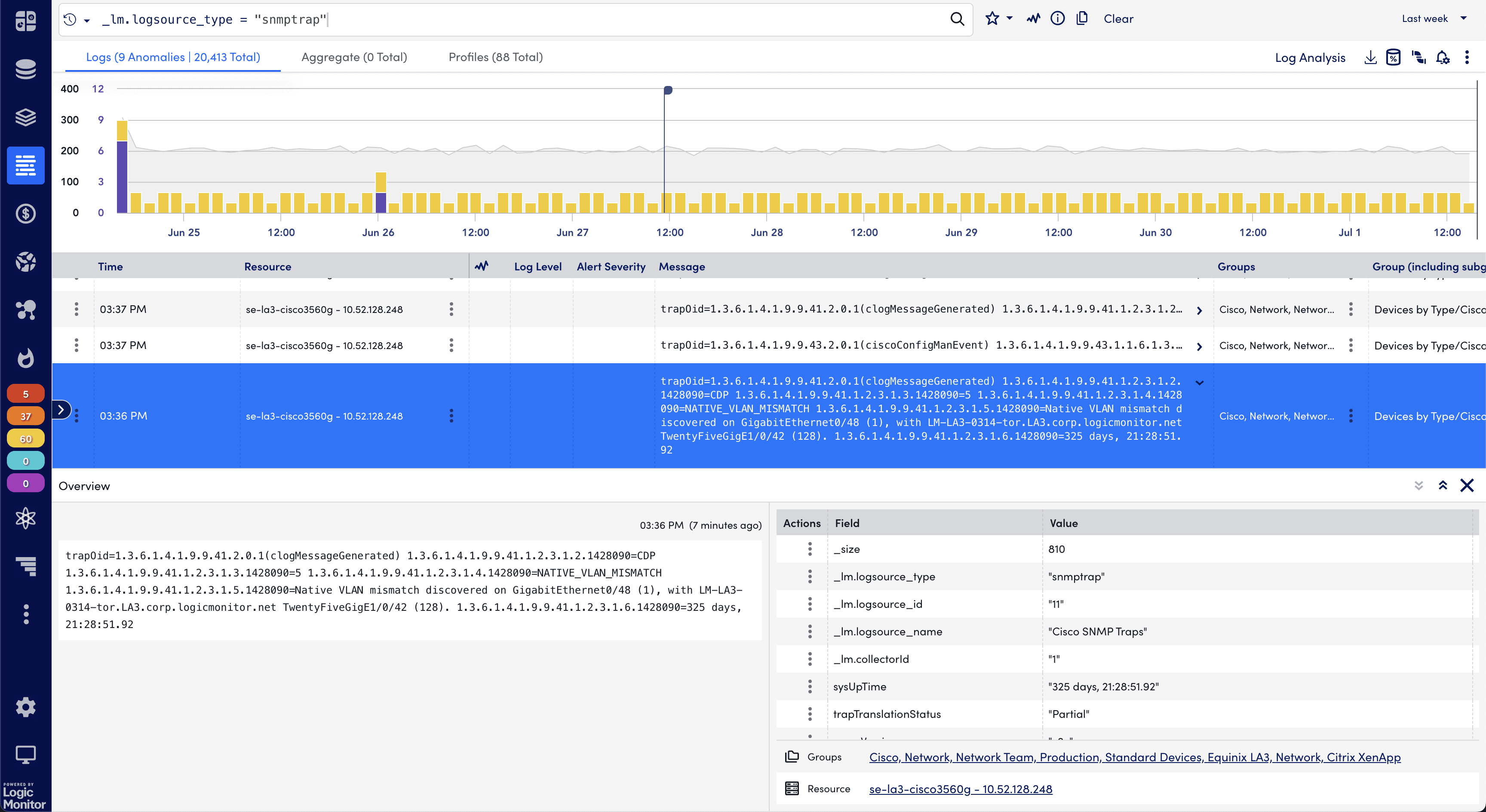
SNMP implementation
SNMP network monitoring tools are specialized applications that leverage the Simple Network Management Protocol to discover, monitor, and manage network devices.
These tools act as SNMP managers, automatically polling devices for performance data and receiving trap notifications when issues arise. They provide centralized dashboards where you can visualize network health, set up automated alerts, and generate reports for capacity planning.
Most SNMP monitoring tools work by using auto-discovery features to scan your network and identify SNMP-enabled devices.
Once discovered, they create monitoring templates based on device types and manufacturers, then begin collecting data at regular intervals. Here are popular network monitoring tools that support SNMP:
- Paessler PRTG Network Monitor: Offers comprehensive SNMP monitoring with preconfigured sensors for major vendors like Cisco, Dell, and HPE. The tool provides auto-discovery functionality and can monitor up to 100 sensors free for personal use. PRTG includes customizable dashboards and acts as both an SNMP manager and trap receiver.
- SolarWinds Network Performance Monitor: Provides real-time SNMP monitoring with advanced network mapping and topology visualization features. The tool supports all SNMP versions and includes the Orion Discovery Wizard for automatic device detection. However, it requires a separate Log Analyzer tool for SNMP trap processing.
- ManageEngine OpManager: Focuses on passive SNMP monitoring using trap messages and can function as an SNMP trap processing engine. It automatically discovers SNMP devices and offers device-based pricing that scales with network size. The tool includes free complementary utilities like SNMP Trap Viewer and MIB Browser.
- Nagios: A highly customizable open-source solution that supports extensive SNMP monitoring through plugins and add-ons. The tool can function as both an SNMP trap receiver and sender, making it suitable for complex network environments. While free, it requires significant configuration time and specialized knowledge for optimal setup.
- LogicMonitor: A cloud-based platform offering SNMP monitoring with out-of-the-box LogicModules for quick deployment. The tool provides SNMP Active Discovery and can monitor up to 200 devices on its Pro plan. However, SNMP trap configuration requires manual setup and collector configuration file modifications.
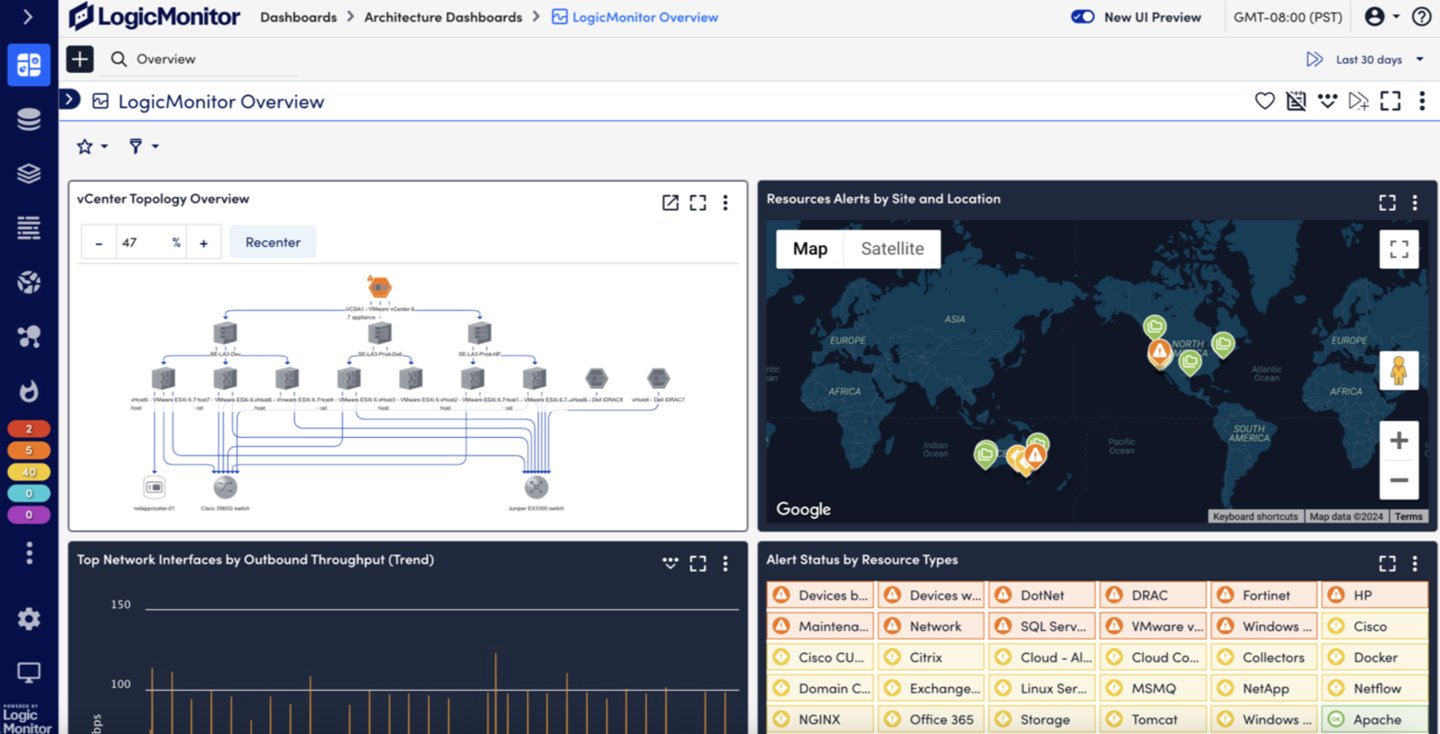
SNMP protocol: Pros, cons, and use cases
SNMP handles many network management functions across different environments and industries.
From small office networks to enterprise data centers, it addresses many monitoring and management challenges. Let's take a look at all its use cases, along with the advantages and disadvantages it offers.
Use cases
- Device Performance Monitoring: SNMP continuously tracks critical metrics like CPU usage, memory utilization, and network traffic across routers, switches, and servers. This real-time visibility helps you identify performance bottlenecks before they impact users. You can set thresholds to receive alerts when devices approach capacity limits.
- Network Fault Detection: The protocol enables rapid identification and diagnosis of network device failures through trap notifications and regular polling. When hardware problems occur, SNMP immediately alerts administrators, reducing downtime and service disruption. This proactive approach prevents small issues from becoming major outages.
- Capacity Planning: By collecting historical performance data over time, SNMP helps forecast future network capacity requirements. You can analyze usage trends to determine when equipment upgrades are needed. This data-driven approach ensures your network can support organizational growth.
- Infrastructure Compliance: SNMP monitoring supports regulatory compliance by maintaining detailed logs of network activity and device configurations. You can generate reports demonstrating adherence to security standards and data retention policies. This documentation is essential for audits and compliance reviews.
- Multi-Vendor Environment Management: The protocol provides standardized monitoring across devices from different manufacturers, eliminating vendor lock-in. You can manage Cisco, HP, Dell, and other equipment using the same monitoring tools. This interoperability reduces training requirements and operational complexity.
Pros
- Industry Standard Protocol: SNMP enjoys universal support across network devices and management software from all major vendors.
- Highly Scalable Architecture: The protocol efficiently manages networks ranging from small offices to enterprise environments with thousands of devices.
- Open Standard Design: Being vendor-neutral prevents proprietary lock-in and ensures long-term compatibility across different systems.
- Automated Monitoring Capabilities: SNMP enables proactive monitoring through traps and regular polling, reducing manual oversight requirements.
- Cost-Effective Solution: The protocol's widespread adoption keeps implementation costs low compared to proprietary alternatives.
- Centralized Management: You can monitor distributed network infrastructure from a single management console.
Cons
- Security Vulnerabilities: Earlier versions transmit data without encryption, making networks vulnerable to interception and attacks.
- Complex Configuration: Setting up SNMP agents, managers, and MIBs requires specialized knowledge and significant time investment.
- Resource Consumption: Regular polling and data collection can consume network bandwidth and device processing power.
- Limited Granularity: SNMP struggles to provide sub-minute monitoring data without overloading network devices.
- Polling Accuracy Issues: Infrequent polling can miss traffic spikes and create misleading performance graphs.
- No Source Timestamping: Variable response times introduce uncertainty in data accuracy and timing.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!

Ritoban Mukherjee is a tech and innovations journalist from West Bengal, India. These days, most of his work revolves around B2B software, such as AI website builders, VoIP platforms, and CRMs, among other things. He has also been published on Tom's Guide, Creative Bloq, IT Pro, Gizmodo, Quartz, and Mental Floss.
