Criminals could pick up your voice through a foot-thick concrete wall, thanks to AI and a flaw in popular laptop microphones - here's what you need to know
New AI trick turns regular FM radios into creepy eavesdropping tools

Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
- AI can now reconstruct speech through concrete using just a laptop’s unshielded microphone wiring
- Laptop mic cables double as antennas, leaking audio through radio harmonics
- MEMS microphones emit signals that betray private conversations without any system compromise or malware
A new form of eavesdropping uses artificial intelligence to recover speech from devices through walls.
A report by eeNews outline how it exploits a vulnerability in widely used MEMS (microelectromechanical systems) microphones, and the most affected devices are laptops, due in part to their internal wiring design.
Researchers from the University of Florida and Japan’s University of Electro-Communications demonstrated even through a 25 cm concrete barrier, attackers can accurately reconstruct speech using nothing more than an FM receiver, a copper antenna, and machine learning tools.
So, why laptops?
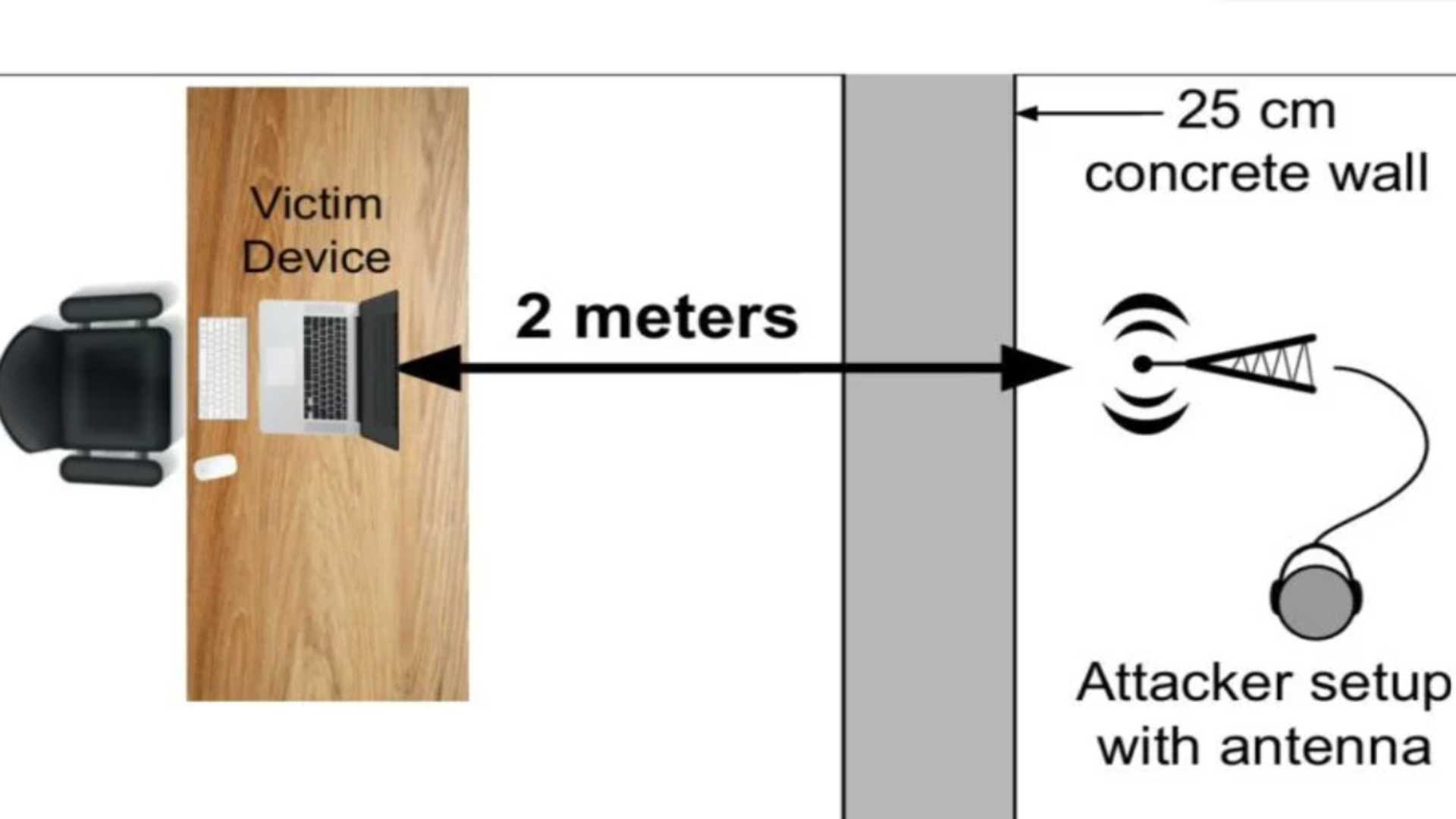
The microphones in many laptops are connected via long, unshielded wires, effectively turning them into antennas, the researchers note.
“With an FM radio receiver and a copper antenna, you can eavesdrop on these microphones. That’s how easy this can be…It costs maybe a hundred dollars, or even less,” said Prof. Sara Rampazzi at the University of Florida.
The research revealed an accuracy of up to 94.2% in recognizing spoken digits, while OpenAI’s generative models achieved a transcription error rate as low as 6.5%.
The researchers examined several MEMS microphones, including the MP34DT01-M from STMicroelectronics, Knowles SPM0405 (now Synaptics), TDK InvenSense CS-41350 and T3902, and Vesper’s VM3000 (now part of Qualcomm).
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
These microphones emit electromagnetic signals that can leak acoustic data through radio harmonics.
According to STMicroelectronics, “this is an intrinsic behavior of Digital PDM MEMS microphones,” and the design used in laptops often lacks shielding, turning flat cables into ideal antennas.
To mitigate this risk, experts recommend relocating microphones within laptops to reduce cable length and shielding the wires. They also propose using spread spectrum clocking to reduce the intelligibility of emissions without affecting performance.
These fixes are relatively simple, but they are relevant for newer devices moving forward. What about pre-existing devices, then?
Regular users need to invest in the best antivirus or endpoint protection solutions, which offer some protection even though they are not explicitly listed to defend against this new threat.
These tools typically operate at the software level and may not detect passive attacks that don’t involve code execution or system compromise.
For individuals seeking the best identity theft protection, this research shows that even conversations assumed to be private may be within reach of sophisticated, low-cost surveillance.
You might also like
- These are the best VPNs with antivirus that you can use right now
- Take a look at our pick of the best internet security suites available
- I’m an AI expert and this is why strong ethical standards are the only way to make AI successful

Efosa has been writing about technology for over 7 years, initially driven by curiosity but now fueled by a strong passion for the field. He holds both a Master's and a PhD in sciences, which provided him with a solid foundation in analytical thinking.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.