TechRadar Verdict
You get loads of features with this antivirus offering, but there are too many problems and not enough protective power to justify the price.
Pros
- +
Lots of features
- +
Bitdefender engine
Cons
- -
Scanner repeatedly crashed during testing
- -
Antivirus capabilities are average at best
- -
No scores from the major testing labs
Why you can trust TechRadar
San Francisco-based IObit is best known as a popular developer of PC maintenance utilities, including IObit Uninstaller, Advanced SystemCare and Driver Booster.
IObit Malware Fighter Pro is the lead product in the company's security range, and has what looks like a capable feature set. It boasts both the IObit and Bitdefender antivirus engines, anti-ransomware capabilities, URL filtering, ad blocking, anti-cryptocurrency mining, webcam protection, and more.
The headline price looks great at $20, until you look closely, realize this includes a 50% discount for year one only, and renews at $40, and the license covers just one device.
Bitdefender Antivirus Plus 2020 is a little more expensive at $25 for year one, $60 on renewal, but that covers up to three devices.
A very limited free build allows you to get a basic idea of how the package works. But we do mean basic – the free version doesn't include the Bitdefender engine, has minimal real-time protection, can't prevent ransomware attacks during the boot process, and apparently can't even 'detect malicious processes running in RAM'. Which sounds like a fairly fundamental issue, to us.
IObit doesn't mention a trial on the main Malware Fighter page, but we found one available here. You must hand over your payment details, but won't be billed for 30 days, and can cancel at any time if you're unhappy.
IObit also offers a 60-day money-back guarantee, although the small print contains a lot of potential gotchas. The company says you won't get a refund if you've failed to read the product description, for instance, or have 'suddenly changed your mind.' It appears you can't just ask for your money back – you're going to have to persuade IObit that you've a good enough reason to escape its financial clutches.
Setup
Installing most antivirus packages is as easy as downloading and running the installer, and waiting a few seconds. Even the greenest of newbies can do it. However, it seems that IObit isn't convinced of this, and after ordering the trial build it suggested we call a toll-free US number where a 'certified technician' would securely connect to our PC and remotely activate the software. Is this really supposed to be easier?
Why would IObit even begin to think this was a good idea? Reading the small print explained what was going on. During the remote connection, IObit explained, 'at your request, we will diagnose your PC for other hard-to-identify problems. And paid service will be offered when needed.' It's just upselling for the company's remote support service.
If you'd rather not get involved with IObit's over-the-top marketing, wait a few seconds and an email should arrive with a download link and license code.
Setup was straightforward, and the installer equipped our test system with a copy of Malware Fighter Free within a very few seconds.
We activated the full version using the license code from the email. This kicked off another setup process as Malware Fighter downloaded and installed the Bitdefender engine, but the package didn't require any further intervention, and we were able to leave it to finish the job. (And no, we saw not the tiniest reason why 'remote activation' would make this easier. If anything, enabling remote access could be far more complicated.)
In previous reviews we've found that Malware Fighter's processes to be poorly protected, and could be disabled by malware using little more than a basic batch file. It's improved a little, but still has its weaknesses. Any process with administrator rights can freely delete its core service, for instance. Whether any malware would bother to do this is open to question - and if malicious code is able to run on your system then you're in big trouble, anyway - but this is still a vulnerability we don't usually see elsewhere.
Features
IObit Malware Fighter Pro may be crammed with features, but its main console is simple and straightforward. There's a clear display of your security status, a large Smart Scan button, and a tiny toolbar on the left-hand side.
IObit's Smart Scan is the standard way to check your computer, and works its way through system areas, currently active processes, the Registry and key files. Scanning speeds are below average, not least because the package can spend up to a minute on an 'initialize database' step before it even starts to do anything else.
It wasn't possible to run scans in parallel. If you need to check a file from Explorer, for instance, you can normally right click it, select Scan with IObit and get a report immediately. But if a Smart Scan was running, IObit simply switched to the Smart Scan window and left us waiting to get the results.
We tried running full system scans, but found Malware Fighter Pro kept crashing in the same folder tree. Some oddball fluke? We rebooted, tried again, reinstalled and tried again, with the same results. A separate crash in another folder persuaded us that this probably wasn't some rare one-off issue: Malware Fighter Pro really can be that flaky.
Crashing is bad, but somehow IObit found a way to make the situation worse.
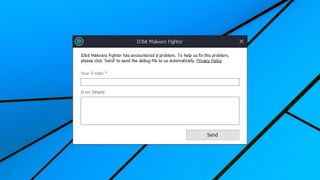
After we approved sending a crash report to IObit the first time, the package did it again, automatically, after each crash, and didn't display any alert to the user. If you left the program alone to complete its scan, then on your return you might find a message telling you your system was clean, with nothing to clearly warn you that the scan finished prematurely and who-knows-how-much of your system had never been checked. That's potentially dangerous.
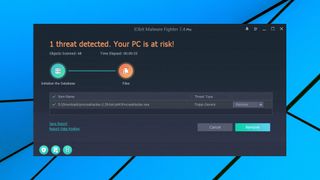
Malware Fighter Pro scans all downloads by default and tells you if it thinks they're safe. Sounds great, but it can be a little misleading. We noticed that if we downloaded a file that Malware Fighter Pro couldn't read - a password-protected zip, say - we still got the 'file is safe' message. In theory the program should still detect known threats when they're unzipped, so this isn't a critical error, but we still think it's a bad idea to give users the impression a file is safe when it's not even been scanned.
We also found that we could download simple test threats such as Eicar without any issue, even though when we manually scanned the files later, we were told they were dangerous.
Elsewhere, an anti-ransomware engine allows only trusted apps to edit common user file types (Office documents, images, music, videos, archives and more). That's the theory, anyway, but when we turned the feature on, it made no apparent difference.
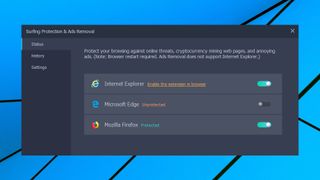
An 'IObit Surfing Protection & Ads Removal' browser extension aims to block ads, highlight dangerous links in search engine results and prevent access to malicious sites. Other packages take a similar approach, but somehow IObit makes a horrible mess of the installation process.
Malware Fighter's interface marked 'Surfing Protection' as on, which most users will assume mean they are protected. But that's misleading. Tapping a Details link shows it's been added to Explorer, Edge and Firefox, but there's no mention of Chrome. You'll only get the Chrome extension if you manually locate and install it from the Chrome store.
We set up the extension anyway, but weren't too impressed. Ad blocking didn't match top add-ons such as uBlock Origin. And when we tried to access a site marked as dangerous, it told us the information was provided by 'Google and IObit', suggesting it may not offer much more protection than we'd get from Chrome alone.
There doesn't appear to be any sensible whitelisting system, either. We tried visiting a falsely flagged site in Chrome, bypassed the warning and were able to visit it. When we tried to visit it again, the browser let us access the page without any further warning. The URL wasn't on a whitelist, so there was no obvious way to undo this and have it blocked again. And, confusingly, although the extension no longer blocked the page, its History list still recorded that we had visited a dangerous site.
There's better news with a ‘webcam guard’ which aims to stop ‘unauthorized programs’ accessing your webcam. We tried using a test command line program to sneakily capture and save a camera image, but Malware Fighter noticed what we were doing, displayed an alert, and didn't allow the capture unless we specifically gave our permission.
Malware Fighter Pro has several other tools which work in the background. Homepage Protection prevents malicious changes to your browser home page and search engine, while anti-tracking clears tracking cookies when your browser closes, and DNS Protect makes it easy to set custom DNS servers, and prevents malware changing them. We didn't test these in depth, but they all have some value, and aren't the type of features you'll normally get with the competition.
Protection
IObit Malware Fighter Pro had average detection results in our tests, but as they are too small-scale to give a definitive picture of antivirus accuracy, we normally check how a product is reviewed by the major testing labs. Unfortunately, that's not possible here as IObit isn't covered by any of them.
We do know that Malware Fighter Pro includes the excellent Bitdefender engine, which is a definite plus. But it's not implemented in the same way as the original, and doesn't include the same level of real-time protection, so it's unlikely you'll get the same degree of malware-blocking effectiveness as with Bitdefender's own products.
Adding IObit's own engine may help protect you from even more threats, but we're unconvinced. It mostly raised false alarms for us.
With no information available from other sources, we decided to try an additional test of our own. We've developed a custom ransomware simulator which spiders through a specific folder tree on our test system, finding and encrypting potentially thousands of media and document files. Would Malware Fighter be able to protect against a threat it had never seen before?
Well, no. The antivirus engine didn't detect or block the threat. Bitdefender's own products block it with ease, reinforcing the idea that you're not getting the same level of protection with Malware Fighter.
Previously, IObit's generic Ransomware Shield stopped our simulator, but it had no effect this time, and thousands of files were encrypted during the attack.
Our simulator wasn't real malware, so we can't draw any big conclusions from this. In fact, IObit might argue that because it wasn't malware, it took the right action in allowing it to run. The overall results don't fill us with confidence, though, and it looks like there's much better protection to be found elsewhere.
Final verdict
IObit Malware Fighter Pro has a lengthy feature list, but some features don't work as expected, the core antivirus seems average at best, and there's no comparative scores available from the big testing labs.
- We've also highlighted the best antivirus software in this roundup

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.