Sponsored by NinjaOne
5 essential features every remote monitoring and management platform needs to have
Stay on top of your devices at all times

Managing IT environments, especially distributed or hybrid ones that are growing in popularity, can quickly become overwhelming and tiresome without the proper tools.
That’s where you must enlist the help of a reliable remote monitoring and management platform (RMM).
An effective RMM solution is the lifeline of your IT operations. It gives IT specialists the power to proactively monitor endpoints, automate tasks, troubleshoot issues remotely, and enforce security policies - all from a centralized dashboard.
But with so many options out there, it’s difficult to discern which features truly matter. Here are five must-have capabilities every efficient RMM platform should offer.
Reader offer: Get a 14-day free trial on NinjaOne
NinjaOne is a cloud-based IT management platform designed for IT professionals. It offers features like remote monitoring, patch management, asset tracking, and automated remediation, enabling efficient device management across various environments. With capabilities such as secure remote access, real-time alerts, and mobile device management, NinjaOne streamlines IT operations.
1. Automated monitoring and alerts
The core part of any RMM platform is the ability to continuously monitor endpoints and infrastructure in real time.
Automated monitoring accompanied by smart alerting guarantees IT teams are instantly notified when something goes wrong. This can be anything from an overloaded CPU to connectivity problems to a security anomaly, and being on top of it is critical.
In other words, automated monitoring and alerting will help IT administrators respond more swiftly to fix issues, as it consistently seeks out threats and anomalies in your network and alerts you immediately to any single one it detects.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Luckily, many tools today employ artificial intelligence and machine learning to spot such threats more easily.
Monitoring the performance of every device connected to your network allows you to watch out for problems such as power outages, database crashes, router failures, and the like. If you observe a flaw with a specific device, it will let you troubleshoot it and identify the issue to fix it.
Your platform should have network maps, giving administrators a bird’s-eye view of the network, which is particularly important for large enterprises with a substantial number of devices connected to their networks.
Staying on top of everything at all times will help you prevent issues that can cause a widespread network collapse.
2. Patch management
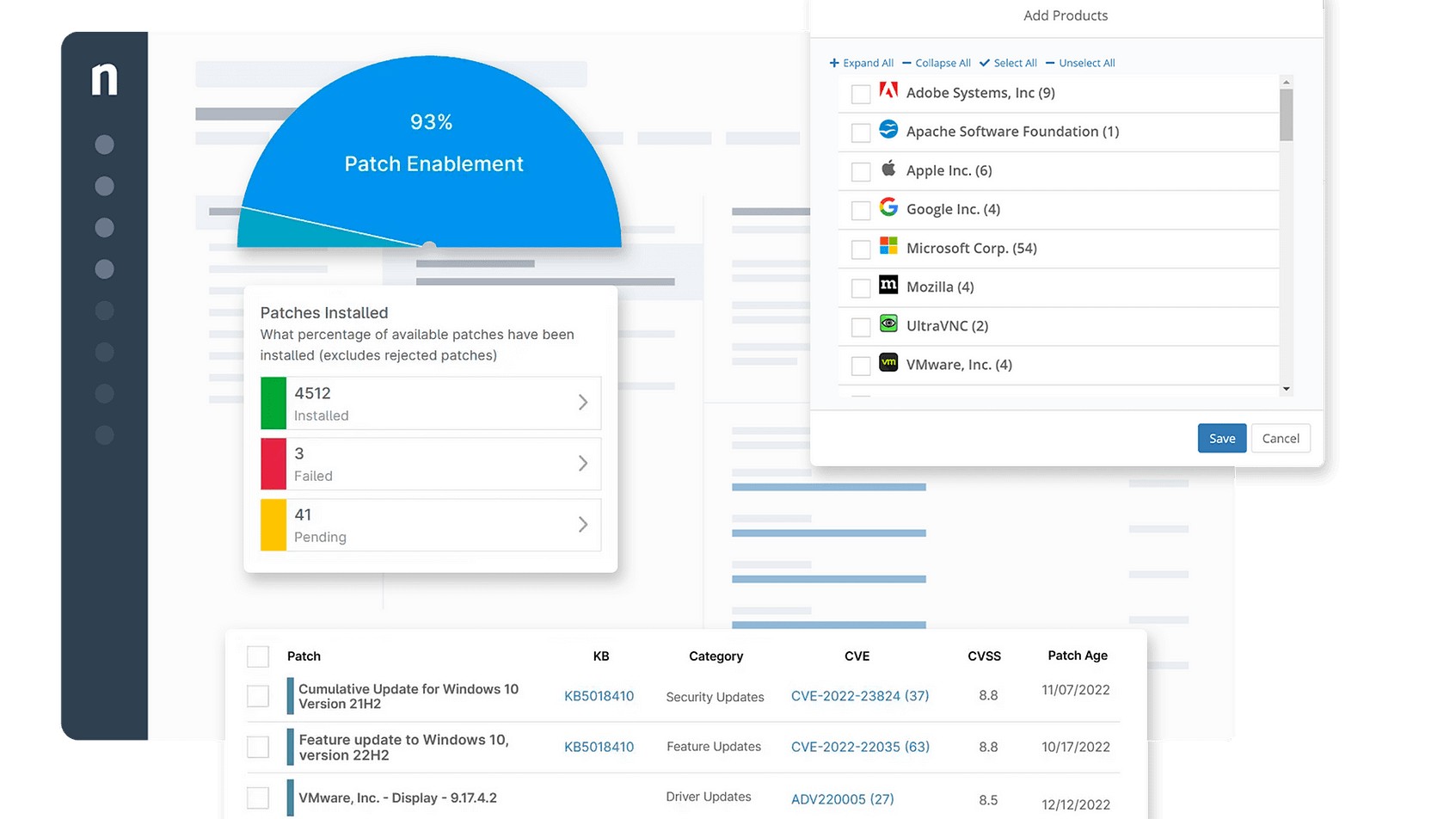
With new software vulnerabilities and exploits appearing daily, it’s massively important to install operating system and application security patches as soon as they’re released.
Failing to keep your software up-to-date and in the best condition is one of the biggest oversights you can commit. Slipping up in this area leaves your proverbial doors open to all kinds of attackers preying in the internet’s darkest corners.
Strong patch management via a capable remote monitoring and management platform allows you to schedule, deploy, and verify critical updates across all devices automatically. This way, you’re keeping systems secure and compliant without manual intervention.
As opposed to the standard approach to patch management, in which every app handles its own updates, a dedicated patch manager is more streamlined.
It acts through a single central interface to scan multiple apps for updates, reporting any missing patches it finds, and automatically rectifies the situation.
3. Remote access and control
Secure remote access is another prerequisite for a successful IT environment maintenance. Any self-respecting RMM platform allows IT admins to manage devices from anywhere, reducing response times, improving resolution rates, and supporting productivity - even when away from the office.
Optimally, IT technicians can access your endpoints remotely and resolve any issues with full console access. They may even allow your IT teams to solve problems via the user’s camera through proprietary solutions without additional downloads, or require a third-party software integration to achieve the same goal.
Some RMM platforms also feature a stealth mode remote control, giving you access to an endpoint without the user’s knowledge. This means its desktop, memory utilization, file and directory transfer, and sometimes even allowing you to browse its drive, add, modify, or delete files.
Ideally, this remote access should allow for smooth and instant connections to company-owned devices and include screen sharing, file transfer, and command-line access. It should also be able to work in the background without bothering end users.
4. IT asset and inventory management
Having a clear idea of what’s connected to your network is just as important as the security aspect of it all.
Built-in IT asset and inventory management offers visibility into every device, software license, and hardware component. As such, it helps you optimize resource usage and plan upgrades well in advance.
Software asset management refers to managing and optimizing the acquisition, deployment, and maintenance of software tools in an organization.
This means listing the software required for specific tasks, its pricing, subscription renewals, and other relevant details.
As for hardware management, it involves identifying and securing various IT assets, from Windows and Mac to Android and iOS. It should provide comprehensive application control on these devices and allow IT teams to manage users' privileges and application access across your infrastructure.
With a strong RMM solution, you can generate detailed reports about your software and hardware inventory to identify potential issues and fix them.
Some platforms allow you to schedule these reports to be generated automatically at specific intervals.
5. Scripting and automation
Instead of repeating manual and menial tasks over and over again, an RMM platform can do it for you with scripting and automation. This way, it will allow you to streamline processes like system cleanup, configuration updates, patch management, and security scans.
A capable RMM platform will aid teams in automating various tasks through AI scripting and Network Operations Center (NOC) services, compiling your diverse data and consolidating it into meaningful reports. They save you time, reduce errors, and allow you to scale your IT operations effectively.
Some of the more popular RMM solutions offer informative dashboards coupled with unified UIs, automated OS, third-party patching, AI scripting, and intelligent monitoring.
They also support multiple third-party integrations for any additional tools and services you might require.
Conclusion
Overall, RMMs have become indispensable for today’s IT teams. They offer visibility, control, and scalability in modern dynamic environments. But to be truly effective, an RMM platform has to go beyond the basics and include the above features to ensure proper management of your IT environments.
It must offer real-time monitoring to prevent problems before they escalate, patch management to close security gaps automatically, remote access to allow rapid support, inventory tracking to provide a clear view of your IT landscape, and automation tools that enhance your team’s efficiency.
If your current solution is missing any of them, it might be time for you to reevaluate and consider upgrading.
FAQs
What is a remote monitoring and management system?
A remote monitoring and management (RMM) system is a software tool that allows IT teams to monitor, maintain, and manage endpoints, networks, and systems from a centralized location remotely. In other words, it doesn’t matter where those devices are located, as you can access them from any place.
It enables proactive detection of issues, remote troubleshooting, automated tasks, and better overall control of IT environments. RMM tools are particularly valuable in distributed or hybrid work environments, where physical presence at every endpoint isn’t practical.
What is remote monitoring?
Remote monitoring refers to the process of continuously observing the health and performance of computer systems, devices, and networks from afar. It enables IT teams to track key performance indicators, like CPU usage, memory consumption, connectivity status, and more.
Additionally, it alerts IT teams to potential problems like outages, unusual behavior, or performance dips that could indicate system failures, security breaches, or hardware issues. This way, they can fix them before they cause real damage.
What is the RMM system?
An RMM system is short for Remote Monitoring and Management system. It’s the foundation of IT operations in many businesses, giving administrators the tools to automate maintenance, apply updates, deploy patches, monitor performance, and access devices remotely.
It’s a one-stop platform for keeping everything in your IT ecosystem running smoothly and securely. As such, it helps IT teams boost efficiency, strengthen security, and scale their operations without constantly putting out fires.
What is RMM and MDM?
RMM (Remote Monitoring and Management) and MDM (Mobile Device Management) are both used to manage IT systems, but they focus on different things.
Specifically, RMM focuses on the overall IT environment, including servers, computers, and networks, providing tools to monitor, patch, and control them remotely.
On the other hand, MDM deals with managing mobile devices like smartphones and tablets. It enforces security policies, tracks device usage, and manages apps on those mobile endpoints.
Together, they offer comprehensive coverage for both desktop and mobile IT assets.
Sead is a seasoned freelance journalist based in Sarajevo, Bosnia and Herzegovina. He writes about IT (cloud, IoT, 5G, VPN) and cybersecurity (ransomware, data breaches, laws and regulations). In his career, spanning more than a decade, he’s written for numerous media outlets, including Al Jazeera Balkans. He’s also held several modules on content writing for Represent Communications.
