TechRadar Verdict
If you want a perfect penetration testing tool, with Burp Suite Community Edition you can get it for free. However, to get a web vulnerability scanner you’ll have to go with one of the paid plans.
Pros
- +
Paid plans can be purchased with Bitcoin
- +
Plenty of integrations
- +
Simple setup
- +
There’s a fermium edition
Cons
- -
The free edition is short on features
Why you can trust TechRadar
Burp Suite Community Edition is a toll-free version of a web vulnerability scanner and penetration testing tool that’s also provided as a proprietary product.
Created by PortSwigger, it’s particularly popular among white hat hackers since it makes penetration testing a piece of cake. Still, many non-tech-savvy users have successfully utilized its capacities as well.
Founded in 2008, PortSwigger is a UK-based company headquartered in Knutsford and celebrated for coming up with some of the most widely used cybersecurity software for businesses, Burp Suite being their first-rate release. This software is currently used by more than 60,000 users and 15,000 companies of all sizes across the world.
In their own words, PortSwigger is on the mission to “enable the world to secure the web”, and it’s clear that the company has come a long way since its humble start.
PortSwigger's official site benefits from a clear, color-coded, simple-to-understand design and provides plenty of information about its products. From there, you can jump off to their blog where you’ll find a couple of well-written articles.
As for social networking sites, PortSwigger can be found on Twitter, LinkedIn, and GitHub.
Plans and pricing
As suggested in the chapter above, the community edition is completely cost-free for all users.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The professional edition of Burp Suite comes as a single-user license, which means that each time a new user wants to install this edition they’ll have to purchase a new license. This will set them back for $399 per year and while you can subscribe for one, two, three, four, five, or ten years right off the bat, you won’t be rewarded with any discount for making a long-term commitment.
However, you’re invited to request a 30-day trial and try out this product for free before making a purchase.
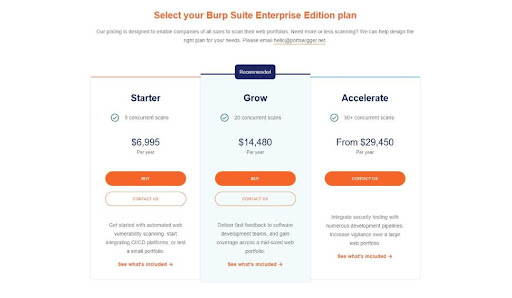
The third and final edition of Burp Suite is enterprise-oriented and comes in the form of three fully-featured plans ranging from $6,995 to $29,450 per year.
If you’re ready to purchase one of the paid editions of Burp Suite, you can do it with all major credit/debit cards, PayPal, wire transfer, check, or Bitcoin.
Features and functionality
As is so often the case with free editions of proprietary products, Burp Suite Community Edition is short on features that consist of penetration testing tools only.
So, if you still want to go with this plan, expect to get HTTP(s)/WebSockets proxy and history, essential Burp Suite tools (Repeater, Decoder, Sequencer, and Comparer), and a demo version of Burp Intruder.
Since Burp Suite operates as a web proxy, it works with a web browser while the penetration tester intercepts all traffic going between the web server and the browser.
The Repeater tool enables users to inject traffic into a stream where they can test specific apps in search of weaknesses.
As its name implies, the Decoder is there to decode encryption and encode source data into the right format.
The Sequencer is another analysis-focused tool that collects and inspects information trying to find any traces of randomness – it’ll scrutinize the pattern and value of all variations in the test strategy.
Last but not least, the Comparer will perform a comparison, or a visual "diff", between any two items of data that are difficult to decipher.
If you opt for a professional edition of Burp Suite you’ll get all this and a lot more including the Intruder module, which acts as an amalgam of penetration testing tools and a full-featured web vulnerability scanner. It’s customizable and automated, and attack probes can be integrated to run with it.
The enterprise edition provides substantially different sets of services in comparison with the community and professional editions as it is created as a pipeline testing service that can run continuously with a whole variety of probes at the same time. It comes with out-of-the-box integrations with ready-made CI plugins, Jira, Jenkins, ThreadFix, and “rich” API.
Interface and ease of use
If you’re on PortSwigger’s official site, go to “Products” and select “Burp Suite Community Edition” which will take you to the page containing a download button. To download the software you’ll be asked to enter your e-mail address but you can skip this and go straight to the download page. Here you’ll select the edition you wish to use, the operating system (OS) you’re using, and tap into “Download”.
The download and installation processes shouldn’t take more than a couple of minutes and as soon as the installation is complete you’ll be able to access Burp Suite’s user interface (UI).
It might seem a bit confusing that all three Burp Suite editions utilize the same old-fashioned yet well-thought-out UI. However, you’ll soon notice that everything beyond the essential features is locked in the community edition.
Burp Suite’s UI also features dark mode, which is good (or bad) news for our eyes, depending on what scientific research you’ve consulted.
Customer support
If you find yourself in need of a helping hand, PortSwigger got you covered with a couple of helpful options. If you’re not in a hurry, you can use their e-mail address – the technical team is available around the clock from Monday to Friday. They also add that there’s no tiered support with PortSwigger, which means you’ll get equal treatment regardless of which edition of Burp Suite you’re using.
As for the self-support options, PortSwigger’s support center should prove useful enough. It is split into two primary sections, one dedicated to the enterprise edition of Burp Suite and the other one to its professional and community counterparts. Both sections look well-supplied with simple-to-understand guides and a couple of video tutorials.

Competition
For some strange reason, people have mistaken Burp Suite for open-source software so often that PortSwigger had to include a question about this in their FAQ section. This couldn’t happen with OpenVAS since its name says it all – it’s open-source and it’s a vulnerability assessment scanner, and a solid one to boot.
However, if you’re looking for an enterprise-level web security scanner and don’t mind paying big bucks, Burp Suite might be a better choice.
Vulnerability Manager Plus is a cross-OS, priority-driven web vulnerability scanner that offers built-in remediation, and (like Burp Suite) it comes in a cost-free edition as well. However, this fermium is much richer in features than the community edition of Burp Suite – plus, it’s more novice-friendly.
Much like Burp Suite, Probely is aimed at security teams and software developers. However, users with less experience are better off with Probely since it’s simpler to use, has a more intuitive UI, and offers superior customer support.
Final verdict
Burp Suite Community Edition is a pretty popular free web app scanner that often gets brought up as one of the best of its kind in the industry today. It’s a fine solution for finding and fixing zero-day vulnerabilities. However, its free community-focused edition is somewhat short on features which leave a lot to be desired.
- Here's our take for the best firewalls right now
Sead is a seasoned freelance journalist based in Sarajevo, Bosnia and Herzegovina. He writes about IT (cloud, IoT, 5G, VPN) and cybersecurity (ransomware, data breaches, laws and regulations). In his career, spanning more than a decade, he’s written for numerous media outlets, including Al Jazeera Balkans. He’s also held several modules on content writing for Represent Communications.