Incydr by Code42 data loss prevention
Insider threat software enables security teams to respond quickly to data security risks
If you’ve heard of Code42 before, you might know it as the maker of cloud backup software Crashplan for small businesses. But the company is also responsible for one of the best data loss prevention services aimed at enterprises, particularly those with remote workforces.
Code42 has been one of the leading data protection companies for many years but recently has turned its focus to a particular aspect of data protection, insider threats. Its latest offering, Incydr, is designed for this purpose to help organizations quickly detect threats to potential data breaches from inside the business and respond to them appropriately.
Plans and pricing
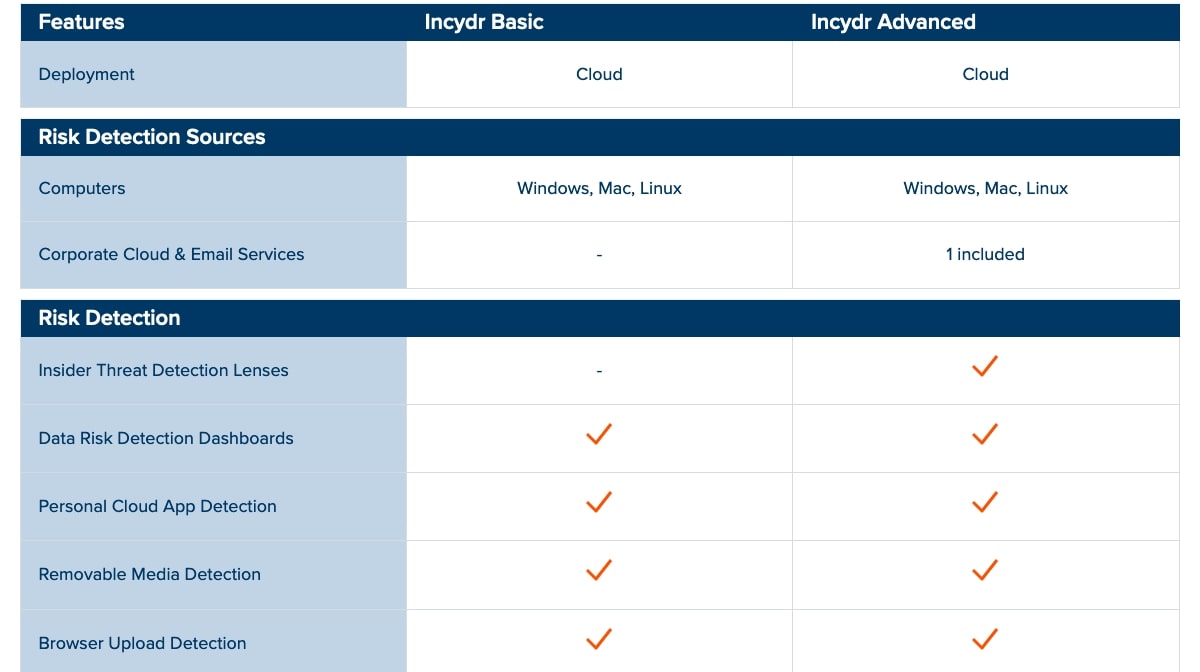
Code42 doesn’t list prices for Incydr, so you have to contact sales for pricing information. But it is available for a 30-day free trial. It comes in two plans: Basic and Advanced. The Advanced plan has more features and this includes support for cloud storage and email services like Microsoft OneDrive and 365, Google Drive and Gmail, and Box.
The Advanced plan will also provide detection of corporate cloud file sharing, email file attachments that violate company policies, and file deletion. And if you need to carry out investigations, the Advanced plan also includes searching through file metadata stretching back 90 days.
How it works
To get started with Incydr you can either contact the sales team to get a quote customized to your business, or you can start with the 30-day free trial.
The form you need to fill in will ask you for information about you and your company, including the number of employees and whether you use Microsoft OneDrive, Google Drive, or Box for cloud data storage.
Be aware that your company will need to have more than 200 employees to be able to use Incydr. The form does have an option for fewer than 200 employees, but if you choose it, you’ll receive an email that states the trial is only available for businesses with 200 or more. It would be better if the 200-employee minimum was stated upfront and wasn’t included as an option at all.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Once you have access to either a trial or full account and have logged in, you’ll have a dashboard that presents an overview of your company’s risk exposure. This includes high-risk and departing employees, and users with the most file activity. High-risk employees are those that have performed actions that fall under risk factor categories like increasing access privileges or being a flight risk.
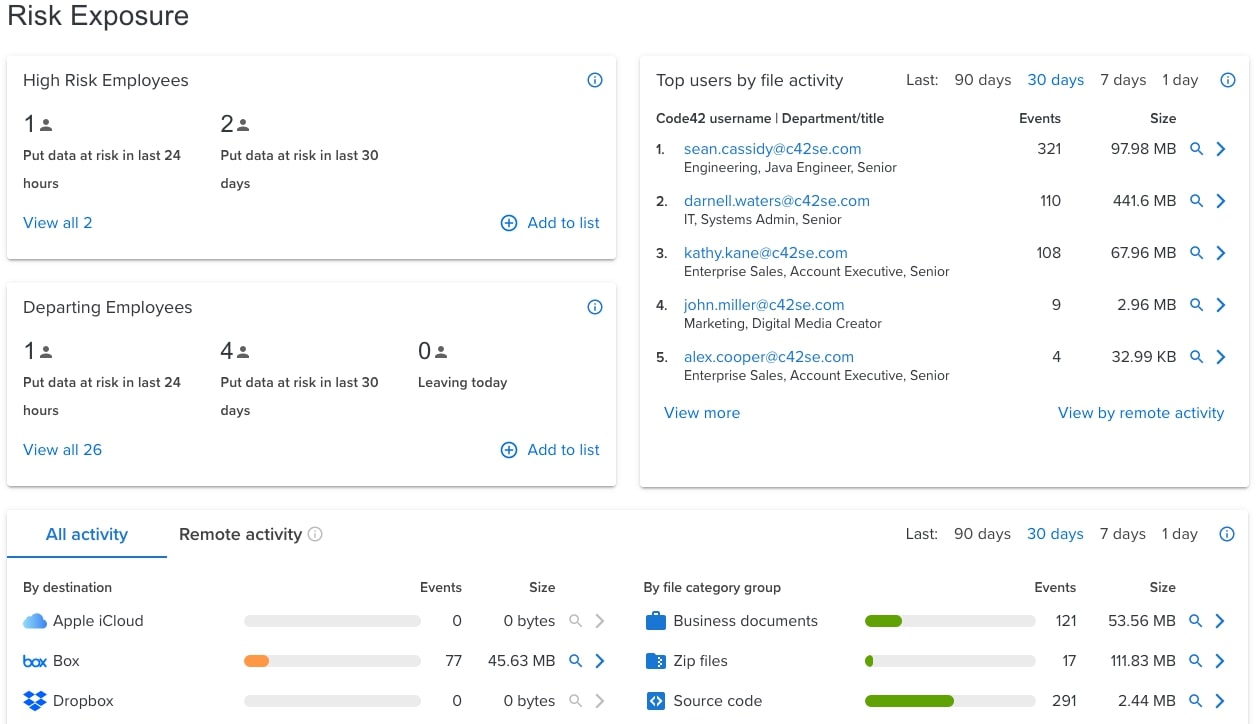
The dashboard will also give you an overview of your organization’s file activity including the type of files that have been moved or shared and where they have been moved to, whether it be iCloud, Box, Dropbox, Google Drive, Microsoft OneDrive, a web browser or other app, or removable media. From there you can either view events details or conduct a forensic search.
A forensic search will let you view file activity based on a variety of different criteria including date and time ranges, file category, exposure type (which includes being synced to a cloud service or copied to removable media), and event type (which includes being modified or emailed).
The links from the dashboard are shortcuts for specific types of searches. For instance, you can choose a forensic search for source code which will bring up a list of all code files that have had events in the specified time frame.
The forensic search will provide you with in-depth information about the event including the user and file involved, the file path on the user’s computer, and other file metadata like size and dates of creation and modification. You’ll also be able to review the contents of the files.
Features and services
The way Incydr works is to bring together information about what data is most important to your business, how, when, and where that data is moving, and who is moving it. It will monitor the creation, deletion, modification, and movement of all files whether the activity is considered a violation of company security policy or not.
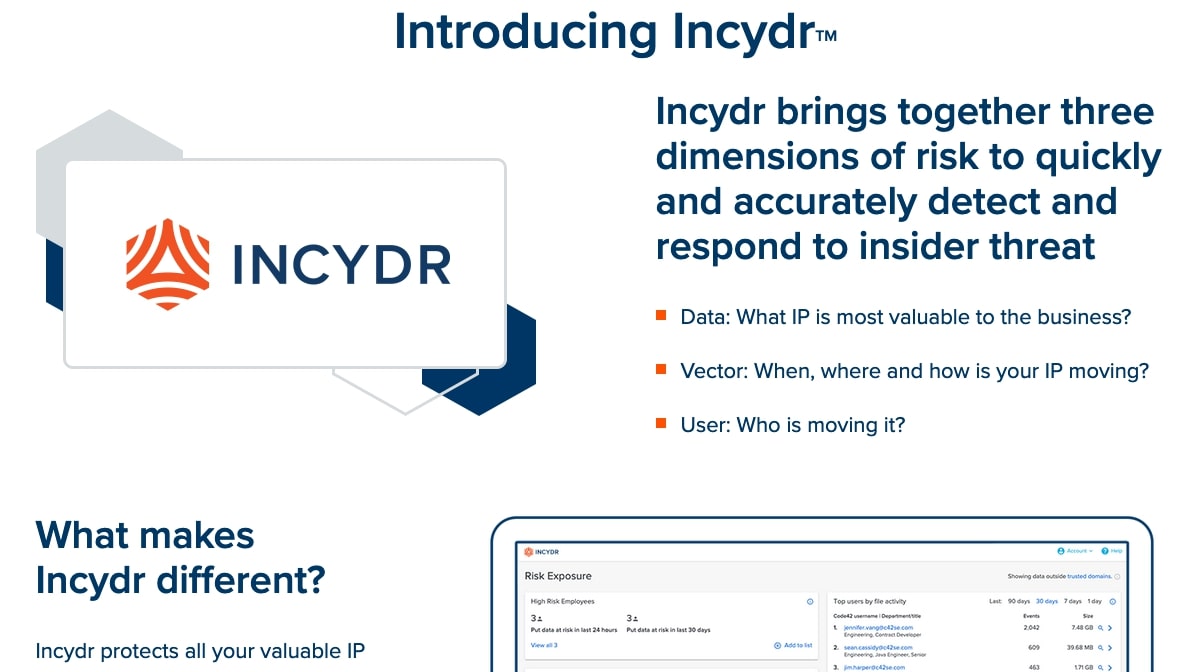
Even though Incydr is monitoring everything, it is smart to be able to tell the difference between normal team collaboration and events that are a real risk.
As well as information about the files involved, Incydr also provides vector information, i.e., the destination that files have been moved or copied to. If it was via a website, that would include the domain name, URL, and active browser tab title. If it was removable media, it would include the make, model, volume name, partition ID, and serial number of the device.
Incydr will also identify risk indicators like remote activity or activity outside normal hours of operation, and attempts to conceal the activity. This then allows security teams to monitor higher-risk employees like those on contract or soon to leave a company.
Support and customer care
Code42 offers basic, no-cost support in the form of documentation, knowledgebase, FAQs, and video training.
There are also three different levels of fee-based support that include email and chat—which are accessible from the Code42 website—and phone. The levels are Select, Premiere, and Premiere Plus, and phone support is available on the two Premiere levels. Most Code42 products include the Premiere level of support as part of the package.
The competition
The market for insider threat software vendors isn’t a particularly large one, but there are some alternatives to Code42 you might consider. These include Insider Threat from Forcepoint and Security Event Manager from Solarwinds.
Like Code42, you have to contact Forcepoint for pricing information on Insider Threat. It has a similar feature set to Incydr but also includes video replay of events and monitoring of verbal attacks on employees via social media, email, and instant messaging.
Solarwinds’ Security Event Manager (SEM) is another insider threat solution for which you need to contact the vendor to receive pricing information, although it is available for a 30-day free trial. It can be used to monitor devices for unusual activity and respond to alerts if there are any instances of suspected insider threats. Using automated responses, it will then block any unwanted attempts to gain access.
Final verdict
For large organizations with a lot of employees that need to protect their intellectual property, Incydr by Code42 would be an indispensable tool to have. Let’s be clear, though, this is not a tool for small businesses, it is only available for organizations of a certain size that have particular concerns about data exfiltration risks.
But if you work on the security team for such an organization, Incydr will undoubtedly make your job much easier and more efficient. The amount of information it captures with its advanced monitoring capabilities and the ease with which security researchers can delve into that information means that your organization will always be ready to respond quickly and effectively to any insider threat.
Further reading
John is a freelance writer and web developer who has been working digitally for 30 years. His experience is in journalism, print design and web development, and he has worked in Australia and the UK. His work has been published in Future publications including TechRadar, Tom's Guide, and ITProPortal.
