How to add encryption to Office 365
Services such as Ferado and FiLink offer a new dimension to security
Being able to encrypt confidential messages and documents is a useful tool, but managing what users can do when they decrypt them may be even more useful.
If you're sending business information in email or storing confidential documents on Office 365, you might need more protection than that provided by your account password. If you want to control who can see the information you're sharing with colleagues and partners, and make sure they can't pass along anything you don't want shared more widely, you can add encryption to Office 365.
Files and emails are protected in transit to the Office 365 service (using the same SSL encrypted connection as for secure websites) and they're secure while they're on Office 365. Microsoft retains control of the encryption keys, but if you don't trust a service provider to act ethically you shouldn't be using their service at all.
Protection and regulation
What about protecting your messages and documents on employees' computers? And what about regulated businesses that may require encryption at rest to protect information? There are several options, depending on what extra protection you're looking for.
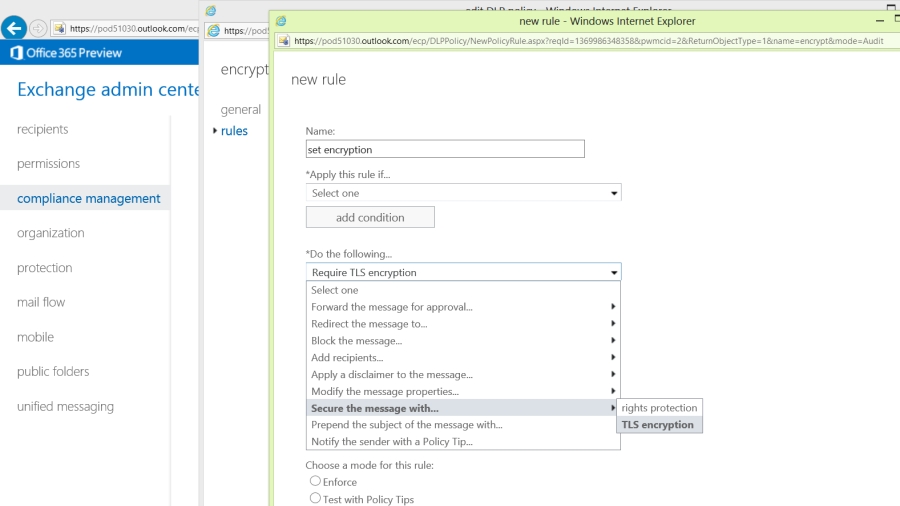
Exchange Hosted Encryption, EHE, is currently among them, but Microsoft seems to be phasing it out. It was originally a service to use with on-premise Exchange servers, but you can also use it with Exchange Online and Forefront Online Protection for Exchange in older Office 365 tenants if you have an enterprise rather than a small business account.
You have to purchase it through Microsoft partners rather than directly (and the Office 2013 update to Office 365 no longer includes Forefront Online Protection for Exchange (FOPE) as a specific service, instead integrating many of the tools directly into the Exchange admin console).
With EHE you can choose which users can encrypt messages and use policy rules in FOPE to enforce encryption on specific messages; for example, by giving users a keyword like ENCRYPT to include in the subject line). Or you can write a macro to put a button on the Outlook toolbar that they can use to set the sensitivity level of the message and use a FOPE policy rule to encrypt any messages they mark as 'company confidential'.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Complications
Reading EHE-encrypted messages is more complicated; users have to open the message, click a link and enter their password to see the message and they only have 15 minutes to read and reply to the message – plus they can only click the authentication link once. To read the message again, they have to open the message, get a new authentication link and enter their password again.
You get more straightforward options with the rights management service that's available for the new version of Office 365, which is a good reason for even a smaller business to pick an enterprise Office 365 account rather than a small business tenant. You don't even need to host your own Active Directory to use it; it works with Windows Azure Active Directory. You will need to make sure you have a subscription to IRM and enable it both in the general Office 365 settings and in the SharePoint admin console.
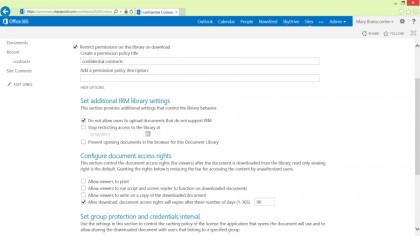
We've already looked at how you can use IRM to block personal information that shouldn't leave your company using the Data Leak Prevention policy rules, but when you venture beyond the pre-set templates you can also use it for encrypting email and protecting documents (in PDF, XPS and Office file formats) in SharePoint.
Rather than simply encrypting messages and documents and choosing who can see them, rights management makes you think about what you're protecting the information against. Do you want to stop people changing an encrypted document, copying information out of or printing an encrypted document, or stop them decrypting and forwarding or printing an encrypted message, or do you want to have an encrypted price list or contract no longer be available when it expires?
Mary (Twitter, Google+, website) started her career at Future Publishing, saw the AOL meltdown first hand the first time around when she ran the AOL UK computing channel, and she's been a freelance tech writer for over a decade. She's used every version of Windows and Office released, and every smartphone too, but she's still looking for the perfect tablet. Yes, she really does have USB earrings.