How to avoid online phishing to better protect yourself
The complete guide to protecting yourself online
We've all seen them, and we've all probably received one. The so-called 419 scam – named after the article of the Nigerian penal code that deals with fraud – is perhaps the most infamous of all phishing scams. It offers the recipient untold wealth if only they'd allow an even more significant sum of money to rest in their bank account temporarily on its route out of a distant nation – oh, and of course, to wire over a small amount to cover the sender's expenses.
It might sound tempting, but the reality is that no one, not even a desperate prince, will give you money for nothing. PhishTank, a collaborative clearinghouse for information about phishing on the internet operated by OpenDNS, had registered 1,198,703 verified phishing sites at the time of writing, of which 12,143 were still active.
Google is going one step further and actively flagging suspected phishing sites in users' browsers.
Take a look at our report, What is phishing and how dangerous is it?
A Techradar Choice for Best Identity Theft Protection
Aura is an excellent choice thanks to its user friendly interface, antivirus service and detailed reporting dashboard. Save up to 50% with a special Techradar discount.
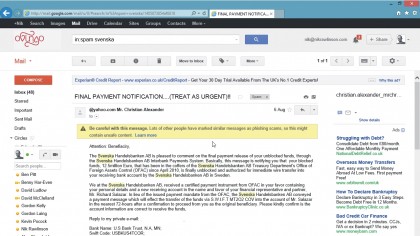
Far from the real deal
Increased public awareness means that phishers have to resort to subtlety. For example, the US Internal Revenue Service (IRS) is posting advisories on its website warning American taxpayers that scammers are passing themselves off as the IRS was hooking recipients with phony tax cuts and rebates.
IRS Commissioner Doug Shulman called it "a disgraceful effort by scam artists to take advantage of people by giving them false hopes of a nonexistent refund."
Its UK equivalent, HMRC, maintains an extensive list of spoofed email addresses frequently used by phishing operatives making similar claims, with such likely candidates as service@, secure@, and customs@hmrc.gov.uk all in circulation – and all fraudulent. Bookmark HMRC's webpage listing addresses used by scammers, and check that any addresses that you might receive future emails from HMRC don't appear on its updated list.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Phishers often go to great lengths to make their emails look authentic. Don't be fooled into thinking that it's been anywhere near those organizations' servers just because an email includes logos from HMRC, your bank, or PayPal.
Watch out for clues, like spelling mistakes or grammatical errors, that would less likely be made by a native speaker, as these too could indicate that the message might have originated from overseas.
Be wary of emails that are too familiar (tax authorities and credit card companies are unlikely to open an email with 'Greetings' or sign off with 'God bless') or ask for too much information.
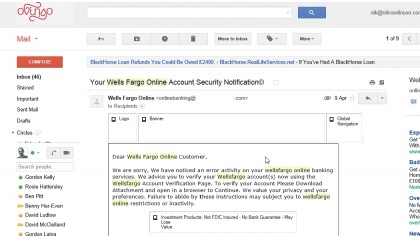
Online banks will never ask you to provide your password or username, sensitive data such as maiden names, or other login credentials. They usually confine sensitive communications to secure messaging areas within the account management screens that can only be accessed after logging in with a username and password, so don't trust emails that appear to include a lot of sensitive financial data.
Be wary of emails purporting to come from your bank that incites you to click a link to access its site; phishers use this tactic to present a genuine login page, which they use to harvest your access credentials. Even if you believe the email is real, open a new browser window, type your bank's URL and follow the links to find the page you need.
Not all phishing scams immediately look like they're after money or credit card details – some are designed to win your custom without realizing that you're leaving an existing supplier. Less reputable domain registration agents are among those who might write to the owners of domains approaching expiry, inducing them to click a link and renew their online property.
Rarely do they explain in anything but the smallest print that doing so will shift the domain away from your original registrar to themselves, leaving them free to apply new terms and conditions and potentially charge a higher price, either immediately or in the future.
What to do next
First of all, don't even think about clicking any links in a scam or phishing email. That's the golden rule. But, then, wherever possible, you should report it to any affected parties and any organizations that its senders may be attempting to spoof.
We live in a world where most banks and other financial institutions have dedicated email addresses to which you can report phishing scams (for HMRC, for example, it's phishing@hmrc.gsi.gov.uk). Type the organization's name followed by phishing into Google, and the result you're looking for will almost always be in the top spot.
Forward the email in its entirety to the reporting address, complete with its full headers, because these show the message's route to reach you, which can be helpful as digital forensic evidence. Most email clients suppress these for clarity by default, but you can usually expose them by clicking a small arrow near the email's subject line.
Usefully, you can report phishing and spam emails directly in Gmail by picking those options from the Reply menu attached to each message.
Check out: This phishing attack hijacks email chains to power up an ancient botnet and Phishing attacks hit more businesses than ever last year for additional information.
Bryan M. Wolfe is a staff writer at TechRadar, iMore, and wherever Future can use him. Though his passion is Apple-based products, he doesn't have a problem using Windows and Android. Bryan's a single father of a 15-year-old daughter and a puppy, Isabelle. Thanks for reading!

