How to stay safe online
Browse safely, it's for your own good
Alternatively, you can also encrypt mail sent via webmail accounts such as Gmail, Outlook and Yahoo, simply by using a desktop email client like Mozilla Thunderbird, plus a few other tools.
With Thunderbird installed and configured as your email client, download and install the free GNUPrivacy Guard encryption software, and then download the Enigmail Thunderbird extension and follow the configuration wizard.
If that sounds like overkill for sending a couple of anonymous messages, then consider a disposable email address instead. Guerilla Mail and Mailinator both fit the bill, letting you quickly send and receive anonymous mail with no incriminating sign-up processes or content scanning. Both sites will however record your IP address when you visit, so consider connecting via Tor (see below).
The wonders of encryption can also keep instant messaging secure. Apps such as Cryptocat are available for Windows, Linux and Mac, giving you an encrypted chatroom to converse with other Cryptocat users using Off the Record Messaging (OTR).
Once you have registered your account on the main site, you can start your own conversation by adding your messaging buddies. You can then begin a private chat and send your buddy encrypted files and photos.
If you already have a messaging account with Yahoo, AOL and Google Talk and so on, consider installing the handy messaging app Pidgin, which is available for Windows, Mac and Linux.
If you and your buddies also install the Pidgin OTR Plugin, your conversations will be encrypted and no one will be able to decode what you're saying or see the contents of any files you send. Pidgin supports a wide variety of messaging protocols including the open XMPP standard. Register an account with Otr.im to make sure all messages are sent encrypted.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Paranoid or Prudent?
In 2013, Edward Snowden was revealed to have downloaded and leaked up to 1.7 million classified documents, revealing the extent of mass surveillance in the US and around the globe.

Key revelations from these leaks include the existence of PRISM: a partnership between the NSA and at least seven major internet companies, including Google, Apple, Microsoft, Yahoo and Facebook. PRISM enables the NSA to access the emails, documents, photos and personal details of any non-US citizen from its participating companies (which have immunity from possible ramifications), en masse, without having to specify an individual target or communications method.
The only crumb of comfort is the NSA apparently has to request the information, rather than having direct server access.
Snowden's leaks also revealed the UK's Government Communications Headquarters (GCHQ) taps around 200 fibreoptic cables carrying global internet and telephone data amounting to up to 600 million daily communications.
This program (codenamed 'Tempora') had the potential to deliver more than 21 Petabytes of information a day, roughly equivalent to sending all the information in every book in the National British Library 200 times a day.
Tempora intel is shared with the NSA and stored for up to 30 days for analysis. Snowden's leaks also detailed the NSA had collected over 200 million global text messages per day and stored details in a database accessible to GCHQ. The really scary bit? This surveillance made no distinction between those suspected of committing a crime and innocent people.

The big bad world
Exposing and blocking advertisers or encrypting email can help you take back some control of your privacy, but it's not enough to keep you and your location hidden.
Whenever your computer is connected directly to the internet, you're still within radar unless you've taken some measures to conceal your IP address.
There are many ways to hide your IP address – but consider if you really need to? The gatekeeper of your identifiable details is your internet service provider. But in the UK and the US, at least, they're unlikely to have the time (or the money) to want to snoop on you themselves.
Both the Creative Content UK alert programme and the US Copyright Alert System are more lenient than you might imagine. If you're found illegally downloading a copyrighted file by the rights holder, they can record and submit your IP address to ISPs in the alert program. If one ISP happens to be your provider, then you'll be sent a copyright infringement notification letter informing you of ways to avoid future breaches.
The UK system allows you to receive four such letters or emails a year. After that, well, not much happens, as it stands. In the US, you get up to six warnings. By the fifth or sixth warning, ISPs can start throttling bandwidth or using other measures to make subscribers play ball. Even then, however, US ISPs are not required to disconnect subscribers or even disclose personal details to the copyright holders.
This all sounds forgiving, but relying on your ISP to protect your identity isn't advisable. Even when most providers are reluctant to divulge your details, sooner or later they will have to give into the law.
Take the recent case of Voltage Pictures identifying and attempting to sue thousands of individuals in the US, Singapore and Australia for illegally downloading the film Dallas Buyers Club.
In November 2016, the "Snooper's Charter Bill' was also passed in the Uk. Known officially as the Investigatory Powers Act 2016, it requires requires web and phone companies to store everyone’s web browsing histories for 12 months and give the police, security services and official agencies unprecedented access to the data.
Tor of duty
One way to get closer to complete anonymity on the cheap is to use Tor, aka The Onion Router. If there's an element of the internet that divides opinion it's Tor. Tor has the same effect as a proxy server, fooling monitoring systems by faking your computer's location.
But it considerably boosts your anonymity by passing your internet data packets through multiple encryption servers (nodes) before they emerge on the open internet (clearnet) and scoot off to your requested website.
As your IP address is concealed by so many encryption servers, you get multiple layers of protection rather than just a single proxy server barrier. Each node only knows where the data came from and the next node it's travelling to, peeling away layers of encryption like an onion.
However, like its veggie namesake, Tor can also be eye-wateringly annoying. The numerous encryption servers that relay your data within the Tor network create speed bottlenecks, and, being volunteer-run, demand usually outstrips available bandwidth.
Although technically you can access the Tor network via installing a command line application and your regular browser, it's much safer to use the Tor project's own Tor Browser Bundle, which is based on Firefox.
While Tor makes it difficult for agencies to perform traffic analysis, it's not completely safe.
By default Tor doesn't make any attempt to disguise the fact you're accessing the Tor network, so while your ISP may not know which sites you're visiting, they'll know you're hiding something. They may even try to throttle or stop your access to Tor. If so, the Tor Browser Bundle allows you to connect to special network "bridges" which will help to disguise your web traffic.
The final Tor node that a packet is relayed through before exiting onto the clearnet is known as the exit relay.
There are more than 1,000 of these active at any one time, and though unlikely that is still possible to eavesdrop on an exit node, as the data emerging there is unencrypted.
You can reduce this risk by using websites that have SSL (look for the padlock icon in the address bar). Tor also operates "hidden services" which can be accessed in the form of a .onion address. For instance Facebook's address is http://facebookcorewww.onion. This makes intercepting your data much more difficult as your traffic never leaves the Tor network.
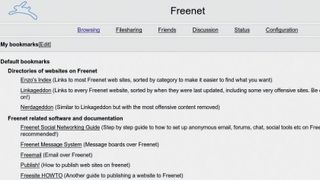
Freenet
An alternative anonymous network without this weakness is Freenet. This is different to Tor in that it's not a means of accessing the clearnet anonymously, but rather a secure network in which to communicate and share files with trusted circles of contacts.
Freenet uses a peer-to-peer model and allocates a portion of your hard drive to store Freenet data and serve it to the network. This is encrypted, as is all the data passed around Freenet, and thanks to such comprehensive end-to-end encryption, Freenet is almost impossible to penetrate and is ideal for anonymous communication and file sharing.
Users are also able to create and host Freesites, which are static websites hosted within, and only accessible from, the Freenet. There are also plug-ins for anonymous email, social network-style communication and forum contact. However, as with other peer-to-peer file-sharing systems, transfer speeds are seed-dependent, and don't expect the overall speed of the network to be lightning-fast either.
Going virtual
Though networks such as Tor and Freenet are useful for protecting privacy, their slow and limited functionality hardly makes them ideal for everyday anonymous internet usage.
To go totally incognito with the fewest possible restrictions or drawbacks, you need a VPN (Virtual Private Network). Where services such as BTGuard will hide torrent traffic, and Tor can keep web browsing anonymous, a VPN will hide the entirety of your internet traffic inside an encrypted tunnel.
Traditionally, VPNs have been used by companies to securely connect employees working off -site to a private corporate network, but now they're increasingly popular for the average Joe wanting to preserve their privacy.
To exploit a VPN, firstly you'll have to come up with at least $5/month to subscribe to one of the huge number of personal VPN providers out there, and you'll also need to install that provider's client software so you can access your VPN tunnel.
Inside the tunnel, data is encrypted to various degrees, depending on the quality of VPN you choose. Try to find a provider which supports OpenVPN which is generally more secure and reliable. Consider also installing a program like TunnelRat which will disconnect web applications when your VPN connection fails. Make sure that your VPN provider also provides DNS forwarding. You can check this is working by visiting the DNS Leak Test website.
In and out
Similar to the potential Tor exit node vulnerability, the weakest links of a VPN tunnel are its entry and exit points.
The VPN server is able to see all data that goes into and out of the tunnel, so if you want to sleep at night leave no stone unturned in ensuring your VPN provider doesn't log any user details or monitor traffic. It's also a wise move to select a company that accepts payments by Bitcoin, to avoid any potential privacy breach that could occur if paying by credit card or PayPal.
For more information on VPN providers, as well as comprehensive reviews, check out our Best VPN page. The We Use Coins website also has a list of VPN providers that accept Bitcoin.
With this amount of privacy protection in place, you'll now be well and truly under the radar. If you're still paranoid that your every move is being watched, it could be time to hone those secret agent skills and live completely off the grid.
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.
