TechRadar Verdict
An excellent tool for creating virtual encrypted disks and partitions, VeraCrypt is also one of the best ways to encrypt an entire operating system to keep your valuable files safe, secure, and private.
Pros
- +
Free
- +
Multiple encryption options
Cons
- -
No support for cloud storage
- -
Somewhat intimidating for new users
Why you can trust TechRadar
VeraCrypt is a disk encryption tool for Windows, macOS, and Linux. You can use it to create a virtual encrypted disk, encrypt an entire partition, or encrypt your operating system so that no one will be able to access any of your files without the right authentication.
- Interested in VeraCrypt? Check out the website here
In our VeraCrypt review, we’ll show you what you can do with it and why we consider it one of the best encryption software utilities available today.
- Also check out our roundup of the best ransomware protection
Plans and pricing
VeraCrypt is freeware, so it costs nothing to download and use.
You can donate to the project through multiple means—PayPal, bank transfer, Liberapay, Flattr, Bitcoin, Bitcoin Cash, Ethereum, Litecoin, and Monero.
Features
VeraCrypt can be used in a few ways. You can create an encrypted virtual disk in a file, encrypt an existing physical volume, or encrypt the system drive of your operating system. Each of these options has different use cases, and we’ll discuss them below.
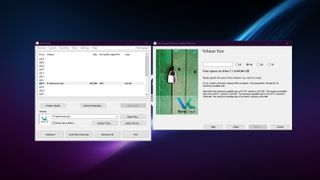
Your first option is to create a virtual disk with VeraCrypt. This virtual disk is stored as an encrypted file. You can then mount the drive in your operating system by supplying the correct authentication, such as a password or keyfile. Data is always encrypted before it is written to the disk and decrypted when it is read.
You can also encrypt any non-system disk volume on your computer in the same way.
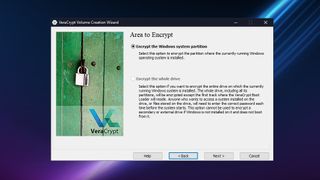
System encryption
You can use VeraCrypt to on-the-fly encrypt a system partition or entire system drive. From a security point of view, this has many advantages over just encrypting specific volumes.
As system encryption includes pre-boot authentication, you need to enter the correct password each time you boot your computer. If someone without the password was to steal your computer, they would be unable to access any of the contents of your drive even if they took out the hard drive and installed it in another machine.
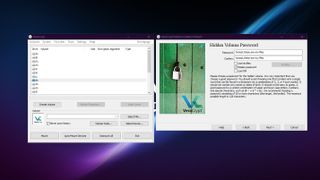
Hidden volumes
You can also create hidden volumes within VeraCrypt volumes. To access your hidden volume, you enter a different password when you mount the volume. A VeraCrypt volume with a hidden volume is indistinguishable from one that doesn’t have a hidden volume.
The idea of a hidden volume is to be able to keep your files secret even in the case of coercion. If you are compelled by someone to decrypt a VeraCrypt volume, you can enter the secondary password instead, revealing only benign files. Your sensitive files remain secret, and whoever is coercing you is none the wiser.
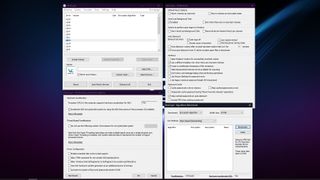
Interface and in use
Using VeraCrypt is slightly more involved than using Microsoft BitLocker, for example, mainly because there are more options you can choose. But setting up VeraCrypt is performed by running through its step-by-step wizards, which offer excellent guidance along the way.
The interface includes some other useful features like an encryption benchmark tool, volume expander, and keyfile generator. Under preferences, you’ll find a long list of tweaks to set up VeraCrypt exactly as you see fit.
Support
VeraCrypt is supported by excellent documentation that details all the features of the software in a succinct but understandable way.
VeraCrypt is developed by French company IDRIX, though its code is heavily based on the abandoned project TrueCrypt. For technical support, your first port of call is the VeraCrypt forums on SourceForge, which has thousands of topics of discussion and a ticketing system.
The VeraCrypt Reddit forum is also very active, so there are multiple community-based options for getting support.
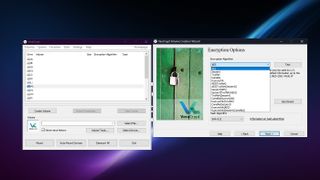
Security
VeraCrypt supports five encryption algorithms (AES XTS, Serpent, Twofish, Camellia, and Kuznyechik), and as you can combo them together there are really 15 options for the encryption algorithm. Then there are four hash algorithms (SHA-512, Whirlpool, SHA-256, and Streebog).
VeraCrypt has patched many vulnerabilities and security issues that were found in TrueCrypt, which could already be considered a secure system.
Because there’s no server authentication or direct sharing capability, VeraCrypt’s security is actually relatively simple, which means there are fewer avenues for potential attack.
VeraCrypt’s source code was independently audited by Quarkslab in 2016, and all vulnerabilities found were addressed in the following version.
The competition
Whole-disk on-the-fly disk encryption is already built into most versions of Windows in the form of Microsoft BitLocker. Like VeraCrypt, you can use BitLocker to secure your operating system so no one can access your files without entering the right password.
BitLocker is slightly easier to use than VeraCrypt because it's seamlessly built into the operating system. But VeraCrypt offers many more features than BitLocker, such as file-based virtual encrypted disks and a selection of strong encryption protocols. VeraCrypt is also cross-platform and the source code is available so you can be sure there are no hidden backdoors.
Final verdict
VeraCrypt is an excellent tool for keeping your sensitive files safe. The lack of a central server for authentication or built-in support for cloud storage could make VeraCrypt a challenge to use as the number of computers and users involved increases. But by keeping these features out of the software, potential attack vectors are reduced.
Its neat features, like file-based virtual drives with on-the-fly encryption, hidden volumes with separate passwords, and system encryption with on-boot authentication, make it an extremely useful free tool for anyone interested in encrypting files.
- We've also featured the best encryption software
Richard brings over 20 years of website development, SEO, and marketing to the table. A graduate in Computer Science, Richard has lectured in Java programming and has built software for companies including Samsung and ASDA. Now, he writes for TechRadar, Tom's Guide, PC Gamer, and Creative Bloq.

Meta’s massive OS announcement is more exciting than a Meta Quest 4 reveal, and VR will never be the same again

World's fastest broadband connection went live down under — Nokia demos 100 gigabit internet line in Australia in record-breaking attempt but doesn't say when it will go on sale

Don't miss the Samsung Galaxy S23 Ultra for just $849 at Best Buy right now