Find out why a program keeps locking up
Troubleshoot hanging programs with these free tools
When you notice that an application has locked up, run WhatIsHang (right-click it and select Run as Administrator in Windows Vista or 7) and it should highlight the frozen window for you. Select this, click File > Get Hang Information and the program will display information that may help to explain the issue.
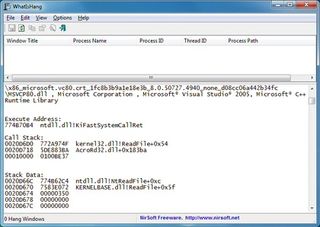
CLUED IN: WhatIsHang can sometimes offer clues as to why a program has locked up
If you're lucky this may include some very specific advice on possible causes of your problems. WhatIsHang might point out that the locked-up process appeared to have been working with a network file recently, for instance; if you're having network problems, or the file can't be accessed for some reason, then that may explain why your program has frozen.
WhatIsHang will also display your program's stack data, though, essentially just a list of information that the program has been working with recently.
Take a look at this: are there any file names you recognise? Could the program be trying to access some file or folder that's not available right now, like an external drive that hasn't been connected? Just browse the data on offer, and look for any clues that might give you an idea of what your troubled program is trying to do.
While WhatIsHang can help occasionally, often the problem is more deeply buried. But that's okay, there's a far more powerful option available.
3. Process Hacker
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Process Hacker is the ultimate souped-up Task Manager, a comprehensive tool that can tell you everything you need to know about your running processes. And, fortunately for our purposes, it's just as useful when it comes to figuring out why a program appears to have locked up.
To find out more about your broken application, first double-click its name in the Process Hacker list, and click the Handles tab. This will show you all the files, Registry keys and other Windows objects that the program has open, which again may offer you some clues about what it's trying to do.
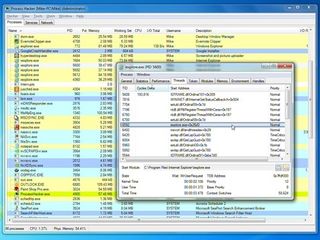
IN DETAIL: Process Hacker is an incredibly powerful tool for finding out more about what's happening on your PC
Next, click the Modules tab, which will reveal all the DLLs and other support files that your application is using. This generally won't mean much, even to experienced Windows users, but just browse the Description column anyway for anything that might be relevant.
For example, if a program started locking up a week ago, and you see it's loading something described as a "Microsoft Office 2010 Component", and you reinstalled Office a week ago, then that may well point you in the right direction. Enter the particular DLL file name at Google to see what comes up.
And finally, click the Thread tab to see a list of process threads, the Windows objects that are actually responsible for running code. Right-click each of these, select Analyze > Wait, and Process Hacker will tell you what, if anything, the thread is actually waiting for.
This might be a file, a user message (a mouse click or keypress), or one of many Windows objects: the Process Hacker author explains more about how to interpret the results, and use them to resolve any problems, on his own site (this is aimed at developers and other expert users, but his comments also contain much more accessible information).
If this still doesn't help, then we'd fall back to more generic troubleshooting techniques. Uninstall any unwanted applications, for example; use a tool like UpdateStar to check the rest are up-to-date; update your drivers via Device Doctor, and use CCleaner to free your system of unwanted junk.
It'll take rather longer than using Windows Resource Monitor, but this kind of cleanup can be surprisingly effective, and it just might leave your PC running smoothly again.

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.
