How to secure your business
Prevent hackers gaining access to sensitive data

Apparently, up to 80 per cent of small businesses that experience a data protection breach go bankrupt shortly afterwards, either through adverse publicity or loss of trade. That's an astonishing figure, but in the excitement of setting up a new venture, securing your data assets is often seen as desirable, but optional - something to do once you begin making money.
On the contrary, it's vital to understand the risks and address them as part of getting everything up and running. You know that you need to buy solid commercial versions of anti-malware applications, along with a good firewall, but it's not just your network that needs protecting.
In a fast-moving world where the bottom line is king, modern working practices can leave you vulnerable. Read on for our complete checklist of everything you need to know to secure your future business.
Physical security

Securing your data network is only part of the business security story, so it's important to lay out a complete policy for handing sensitive information. This is the document that all employees must follow as part of their work. Get them to read it and then sign it as an undertaking to follow it, so that if anything untoward does happen there's no comeback.
The question is, what should go into such a policy? The company information security policy has to cover all aspects of handling information, including anything to do with your customers - names, addresses, orders, general correspondence, and credit card and bank details. It also needs to include anything relating to your finances - spreadsheets, business plans, correspondence with the bank, and communications with partners and suppliers.
Finally, staff records and appraisals must be kept secure, not only from interlopers but also from employees. None of this information must be put at risk through either inattention to security or negligence.
The policy should have a section about physical security. This should include keeping all filing cabinets locked if they contain confidential information. At the end of the day, if you don't intend to take laptops home for safety, the policy should mandate that they be locked away in a desk or cupboard set aside for the task.
Get daily insight, inspiration and deals in your inbox
Get the hottest deals available in your inbox plus news, reviews, opinion, analysis and more from the TechRadar team.
Instead of a wastepaper basket, use a shredder. The shredded paper makes ideal guinea pig bedding.
Social engineering is a great way to gain physical access to a network, so you need to make sure that all employees are aware that they must not hold doors open for people they don't know, and should challenge anyone not known to them.
If you plan to run your own servers, they should be kept in their own locked room with access limited to the staff with responsibility for running them.
The press loves stories about employees of public bodies losing laptops and USB memory sticks containing sensitive information, but such stories are only the tip of the iceberg. Devices, especially USB sticks, go missing at an alarming rate. As a rule of thumb, the fewer copies of sensitive data you have, the easier they are to track and secure.
As a cover-all clause, ensure that your information security policy states that sensitive information must not leave the premises without your expressed permission, and that no laptop or other computing device should be left unattended (in a car while the owner visits a motorway service station, for example, or on a table on a train while the owner visits the toilet).
Now that most people have access to domestic broadband, it's far cheaper to let people work at home than to rent an expensive office. In some industries, home working is now the norm. However, this convenience introduces a new set of security headaches.
If employees are allowed to use company laptops at home, you should be satisfied that they will be used in a secure environment. Company PCs must only be used for company work. If employees want to play games, they must use their own machines.
As we showed in issue 319, it's easy to encrypt the entire hard disk of any laptop using the free tool TrueCrypt. To boot up a protected computer, you must enter a password. Therefore, if a laptop goes missing (targeted muggings do happen), the thief won't get far trying to read your data. This goes for USB sticks, too.
Data use
How you plan to use the sensitive data you collect has a direct bearing on how you need to store and secure it, and on your responsibilities in law. For example, do you need to implement your own e-commerce sever to take orders? Many companies take credit card details and pass them to a secure payment gateway like SagePay or WorldPay.
However, what you do with customer details after a sale is important. Some companies store credit card details as part of each customer's account details. The idea is that these can be recalled for convenience when the customer next places an order. Storing such details along with the CVV number (the three digits on the back of the credit card) carries a responsibility to keep those details absolutely secure. If you store such information, you must register under the Data Protection Act as a Data Controller.
For a new company selling direct to the public, it's easiest to simply create a PayPal account and link it to your company's bank account. You can then add 'Pay now' or 'Add to cart' buttons created under PayPal's secure Website Payments Standard to your web catalogue.
In many cases, the ability to pay through a trusted service like PayPal will enable you to entice customers who might not want to entrust credit card details to privately held ecommerce servers.
Network auditing
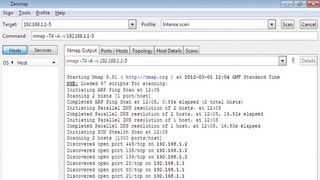
Auditing the hardware on your network and monitoring it for additions is easy using Nmap. The idea is to first run Nmap against the network when no one is using it. This will give you a baseline against which you can monitor subsequent connections. Download and run the Nmap executable and accept the defaults to install it.
Nmap provides a useful GUI in the shape of Zenmap, which runs from the Windows Start menu. In the target input box, enter your subnet in the format 192.168.1.1-254, substituting your own subnet numbers. The '1-254' ensures that Nmap carries out a full scan of all machine addresses on the subnet. Select 'Intense scan' and wait for the results.
As Nmap does its stuff, a list of hosts will begin to build up in the left-hand pane. Is there anything there that you don't recognise? Address 1 is usually your default gateway through to the internet. Click the hosts and their details will appear in the main pane, including the best guess at the running operating system. This will help you identify each device.
If you recognise everything then you have a good baseline for the hardware. Your staff may be adding their own mobile devices when they use the network, so re-run Nmap at regular intervals to get a feel for what they connect.
Check Wi-Fi points
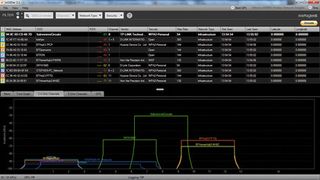
Staff with laptops and other devices they use at home will need to connect to both their own network and the corporate one, so there's scope for a Wi-Fi hacker to set up their own wireless access point nearby with a name that closely resembles your own when read by bleary eyes on a Monday morning.
You can check for such networks by clicking on the Wireless Network icon in the Windows 7 system tray, but you can also monitor nearby networks graphically throughout the day using the excellent InSSIDer by Metageek.
To install it, simply run the executable and accept the default settings. Click the '2.4GHz' tab and you should see all the networks advertising their presence in your vicinity. Is there one trying to mimic yours with a similar name?
If so, you can zero in on it by installing InSSIDer on a laptop. Click the 'Time graph' tab. This shows the relative strength of the signal. Select the suspect signal in the table at the top of the screen and its strength graph becomes bold. Now carry the laptop a few feet - if you're getting nearer the base station for the suspect network, the signal will increase in strength. If the strength gets up to about 25dB or more, you'll be right on top of the base station.
Hardware firewalls

The part of network security that gives corporate types the most trouble is how to secure the gateway between the company network and the rest of the world.
Thankfully, the days of complex software configurations involving multiple network cards and proxy packages are long gone. Instead, you can simply plug in a hardware firewall between the internet connection and the network itself.
Modern hardware firewalls are comprehensive corporate gatekeepers with a surprisingly wide set of resources - even low-end models. They will take care of scanning all incoming and outgoing data streams, for example, which means that they can scan traffic for malware and spam.
Typically, they come with service contracts that include regular updates to their defences, much like those provided by your antivirus supplier. Remember that one of your employees may bring an infected mobile device into the office that could bypass your hardware firewall, so you still need to ensure that the firewall on each corporate computer is active and that each machine also has up to date antivirus protection.
For home workers, many cheaper hardware firewalls now offer virtual private networking (VPN) facilities. This means that home workers can log into the corporate network and work as if they were in the office by connecting to shared drives, the internal mail system and so on. The connection is secured by SSL.
A major headache for bosses is the lure of social networking sites like Twitter and Facebook - not only because they destroy productivity, but because the implicit trust involved makes them highly effective infection vectors for new strains of malware.
To protect your network and the futures of all your staff, look for a hardware firewall featuring content filtering. Why not pick one that allows different sites to be reached at different times? That way you could open up access to social networking sites at lunchtime and impose definite times during which it's okay to visit them.
