We recently looked at various techniques you can use to hide data in Windows, from simple filename tricks to complete encryption of the OS. Now we're going to turn the tables and discover ways to uncover hidden activity.
There are plenty of reasons why someone might not want you to know that your security has been breached. The most obvious is infection with malware. If you believe others may be using your PC without your consent, the issues can become serious. What are they doing? Will people assume it was you?
Luckily, finding out is easier than you might think, and you can even monitor your computer from your inbox.
Exploring Explorer
How you can tell if someone has modified or even added a new file to your computer?
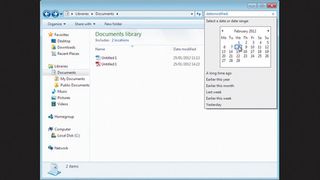
The easiest method is to open Windows Explorer in an account with Administrator rights over the system. Now click 'Organise > Folder and search options'. Click the 'View' tab and in the advanced settings, ensure that 'Show hidden files, folders and drives' is selected. Click 'OK'.
Now click the search box in Windows Explorer. This will reveal several search criteria, including 'Date modified'. Click this and a calendar appears along with some interesting options, including 'Earlier this week'. Click one of these and press [Enter]. All the files modified since this time, including hidden ones, will be listed. Is there anything that you don't like the look of?
Of course, much of today's malware is capable of faking the modify time on a file to hide from this search. The worst malware, the rootkit, maintains its anonymous presence by not only faking modification times, but also ensuring it fools the OS into returning results that make everything seem okay. The rootkit can then allow other malware, like a keylogger, to run.
Get daily insight, inspiration and deals in your inbox
Get the hottest deals available in your inbox plus news, reviews, opinion, analysis and more from the TechRadar team.
To uncover this kind of infection, we need a way of examining the disk while Windows sleeps. Read a sleeping PC The easiest way of achieving this is to boot a Linux live CD, mount the disk and have a look around.
What are we looking for? Luckily, we needn't know. Several security vendors distribute Linux live CD discs designed to simply run a Windows antivirus scanner. Without a subverted Windows system getting in the way, all malware is naked and visible.
One such disk is the Avira Rescue CD. You can download the ISO file and burn it to a bootable disc using your favourite software, but there's another option. If you download and run the EXE version, you'll find that it contains burner software. You'll be asked to insert a DVD, after which the ISO will be unpacked and burned to disc, ready to boot.
If you're using a wireless network card, you'll have to plug your PC into your broadband router with a cable if Linux doesn't contain a driver for your wireless card.
When you boot the rescue disc, you'll be met by a boot menu. Press [Enter] to continue booting. The Avira scanner will load and run.
The software has four tabs. Click 'Update' and then click 'Yes' in the window that appears asking if you want to update the malware definitions. Once complete, click the 'Configuration' tab. Ensure that in the Scan Method section, the option selected is 'All files'. Also ensure that you select the tick boxes for joke programs, security privacy risks and runtime compression utilities. This last option is important because some malware stays securely compressed until it's run, thereby obscuring its purpose.
Finally, click the 'Virus scanner' tab and click 'Start scanner'. Once the scan is complete and any stealthy infections have been identified and hopefully fixed, you can click 'Shut down' and either shut down the computer or reboot. Once Linux has shut itself down, you can remove the DVD and boot into Windows.
Tracking activity
Another major problem, especially if you have to leave your PC unattended for a while, is an interloper using it without your permission. If someone really wants to read your hard disk, booting a Linux live CD will allow them to mount your disk and read whatever they like.
If you don't want to encrypt your entire OS as we demonstrated last issue using TrueCrypt, you can thwart their attempts to even boot the computer by setting a password on your BIOS.
The BIOS contains the first software to be run when your machine powers up. Because there's no way to stop this, telling the BIOS to ask for a password at boot time will stop most would-be hackers dead. What's more, modern BIOS implementations allow for several different passwords that perform different jobs, and newer hard disks can be made to work in conjunction with the BIOS to prevent secrets being revealed.
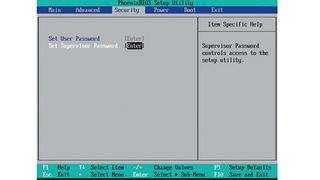
To set a BIOS password, you need to get into its setup mode. Most modern BIOS implementations respond to holding down [F2], [F10] or [Delete]. Your PC's manual will tell you which. Hold this key immediately after power on in cases where the BIOS screen flashes by too quickly.
Different BIOS types have different interfaces, but in general there'll always be a security or password screen. There may be different types of password you can set.
When you boot the computer, the password you're asked to enter is the user password. However, what's to stop someone going into the BIOS and removing it? That's the job of the supervisor password. If you set this, then even entering the BIOS becomes problematic for a hacker.
Because there are techniques for overriding BIOS passwords, laptop BIOS implementations also have an HDD password. This is stored in the hard disk controller and must be supplied before the disk gives up one byte of access.
Evidence gathering
If you think someone is using your PC without permission, sometimes the best thing is to gather evidence, then either confront them or take steps to ensure you have a legitimate reason why they can't continue to use it.
One method of doing this is to install a keylogger. Keyloggers aren't always used illegally. In some situations they can be used to check that personnel are only doing what they're supposed to and not abusing their position.
A word or warning first: Never be tempted to install a keylogger or any other piece of spyware onto a computer that you do not personally own. If you're caught and the case goes to court, you could be liable under the Misuse of Computers Act, and receive a prison sentence and a fine of up to £5,000.
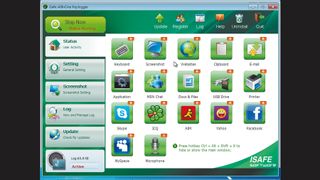
There are many free Windows keyloggers. We'll use iSafe from iSafeSoft. The trial version will last for seven days, which should be enough to discover unauthorised use of your PC. Download the executable to the PC you wish to monitor (which we'll call the target) and run it.
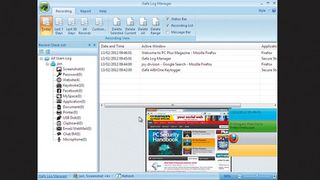
The installation process consists of simply accepting the licence agreement and the defaults. Once installed, press [Ctrl]+[Alt]+[Shift]+[X] and enter the default password 123 to open the keylogger's user interface.
Each part of the system that can be logged has its own icon. At the top of each icon is a number, indicating the records that have been collected. To stop your activity being logged, click the green button marked 'Stop now'.
With iSafe logging events, try opening a web browser and entering a search phrase. Surf to a few sites and then go back to the iSafe user interface. Click 'Log' at the top of the screen. In the left hand panel, expand the username that did the surfing and select the 'Website' category.
In the right-hand panes you'll see the dates and times of each element of surfing activity, along with the site involved. Select one and the lower panel shows the details. Select the 'Keystroke' category in the left hand panel and click an entry from the web surfing traffic you just generated. The lower pane shows the exact keystrokes (including deletions and other edits), and the text entered.
Another valuable feature is the Screenshot category. Screenshots are taken at regular intervals, and are a powerful piece of evidence when looking for untoward activities by others. Back on the main iSafe interface, click the 'Screenshot' tab on the left to access the settings.
By default iSafe makes a capture every minute, but this could soon fill your hard disk. It's more useful to take a shot of the active window. You can further reduce the amount of space taken by each shot by selecting the capture quality. To compress the shots (and protect them), select the option to compress them into an archive. This is protected by the iSafe password.
iSafe won't take screenshots when the computer is idle (in other words, when the suspect isn't using it). To keep taking snaps anyway, click 'Setting', then click 'Screenshot' on the resulting right-hand pane. Untick 'Don't take screenshots when user is idle.'
One excellent function of the screenshot facility is the ability to start taking shots as soon as iSafe detects that the user has entered one or more specified keywords. On the Screenshot tab, click 'Enable Smart Sense' and associated buttons become active. Enter a keyword and click 'Add' to add it to the list. To remove it, select it and click 'Delete'.
More settings
The default password is insecure, so click the 'Settings' tab and then click 'General'. To the right, enter the old 123 password and a new, longer one. Click 'Apply' to change it. The setting allow you to set many other useful options. For example, you can hide the use of iSafe by changing the hotkey sequence from the default of [Ctrl]+[Alt]+[Shift]+[X].
You can also set the parameters for the Stealth mode. These include becoming invisible in Task Manager. Click the 'Users' category and you can specify the users you want to monitor. This enables you to narrow down your evidence gathering to just those people or accounts you suspect.
You can also have relevant data emailed to you. Select the Delivery category and set 'Deliver logs to email' to 'On'. Enter your email address and set the options. Emailing yourself the information captured by iSafe will enable you to monitor activity when your suspect believes they're safe. Provided you can get to your inbox, you can still see what they're up to.
Sifting the evidence
Rather than having to plough through every keystroke, screenshot and other piece of information, you can target a specific date range.
On the main iSafe interface, click 'Log'. Select a date and click 'View log'. Only the entries for that day are shown. You can also select the previous seven or 30 days, or define a custom range. Click the 'Custom' button at the top of the screen, then enter the start and end dates before clicking 'OK'.
You can delete the logs and other collected information using the buttons at the top of the log view. You can also delete a date range or all data here to save on disk space.
Uninstalling iSafe after you've finished is as simple as clicking the 'Uninstall' icon at the top of the interface.
Most Popular

